Overview
Microsoft has released a patch in April,2020 to fix the Remote Code Execution vulnerability CVE-2020-0932 discovered in SharePoint. Successful exploitation of this vulnerability allows authenticated user to execute arbitrary command on the server.
POC is available on GitHub.
Description:
There are different web services present in SharePoint. One of them is WebPartPages, provide the methods for Web Part.
Web parts are server-side controls which run inside a web part page. By using web parts, you can modify the appearance, content and behavior of pages of a SharePoint site by using a browser.
The vulnerability occured because when SharePoint parses the XML configuration of WebParts, it doesn’t restrict available Types for properties.
Exploitation
Before doing exploitation, first understand how POC works.
POC uses following web reference to access the WebPartPages service and its method,
![]()
Above web reference is the starting point of attack.
RenderWebPartForEdit is one of the method of this service, used to parse XML WebParts configuration. POC stored payload in webpart xml and given as a argument to RenderWebPartForEdit function.
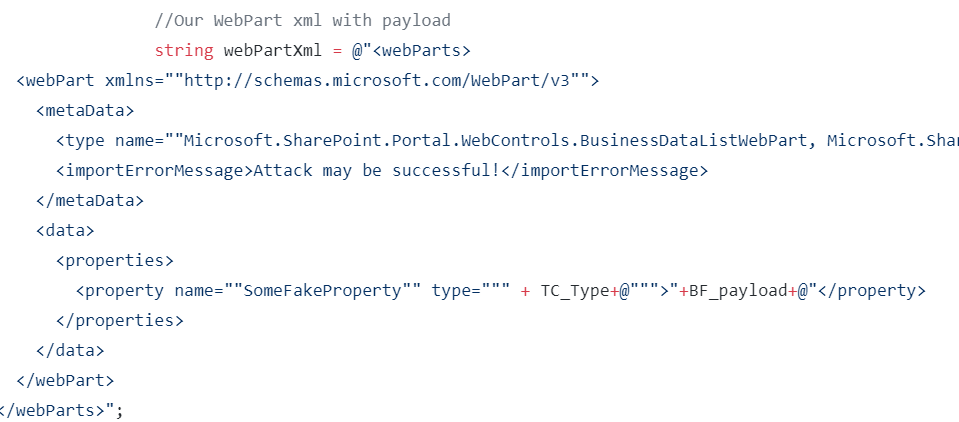
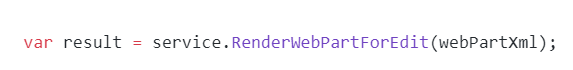
Image Source: thezdi Github Repository
Exploitation steps:
To exploit this vulnerability user must be authenticated. Follow below steps for exploitation,
- Generate resource file:
RCE_Resource.resx file contains payload, first compile it into .resource file using visual studio. - Check the SharePoint process id using IIS manager.
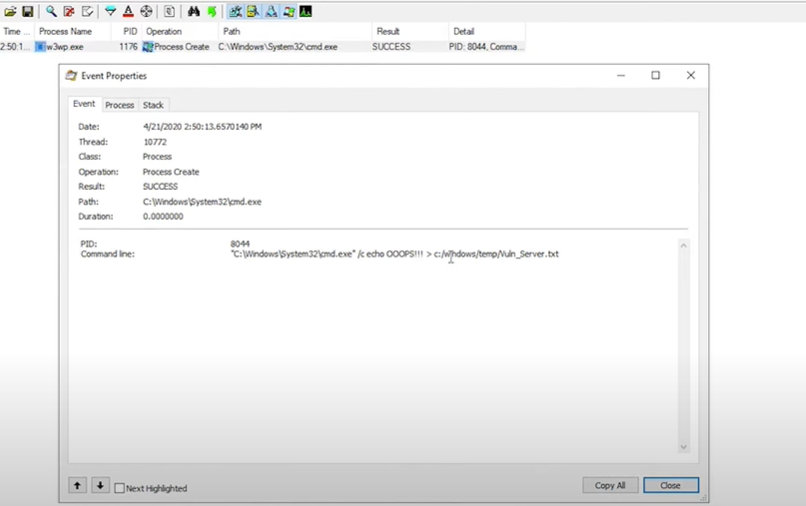
Image Source: thezdi - Apply filter for SharePoint process id on Process Monitor, to check the activity of SharePoint
- Open following uri on sharepoint,
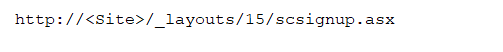
web page will be opened to create new site. Created new site having name MyNewSite1. Base URL for newly created site is http://<Site>/MyNewSite1
- To run POC available on GitHub following arguments are required,
![]()
Remote_path_to_resource_file is the SMB path where payload is located.
Run POC,
Image source: thezdi
After executing POC, we will received the error on command prompt“The control type ‘System.Resources.ResourceSet’ is not allowed on this page.”.
- Now check the process monitor, w3wp.exe process is created. Checked its property, Vuln_server payload file is successfully created on temp folder. Authenticated user can execute arbitrary command on the server
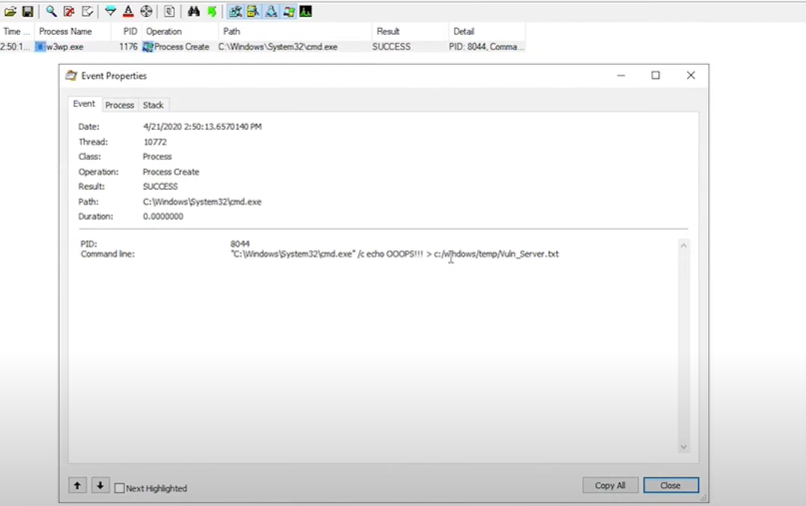
Image Source: thezdi
Affected Products:
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Foundation 2013 Service Pack 1
Advisory
To protect your system from attack, patch with recent update from Microsoft web page
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0932
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 110347. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources: