Vulnerability Overview:
Recently, a vulnerability has been discovered in Docker Desktop. This flaw allows a local user to escalate privilege on the system. Vulnerability exist in the docker Desktop service.
Before looking into vulnerability, understand few concepts Docker Desktop and named pipe.
Docker Desktop for Windows provides an environment for building, shipping, and running dockerized apps. It uses Windows-native Hyper-V virtualization, networking and supports both Linux and Windows Docker containers.
Named pipes provide interprocess communication on a local computer or network. It supports client impersonation. This functionality allows the service to drop its credentials in while connecting to client, under impersonated. Anything started by the Service Control Manager(Special system process) will automatically get the impersonation privilege.
Vulnerability Description:
When Docker Desktop application start, it creates number of child processes. Docker service having high privileges act as a client and communicate with child process using named pipe.
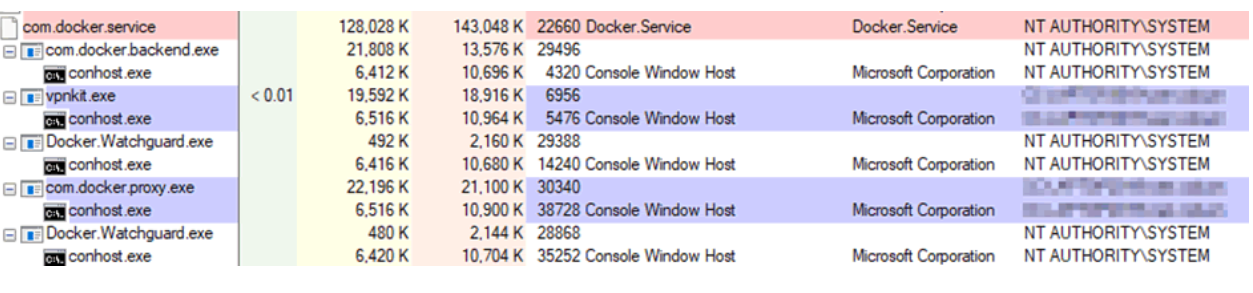
Image Source: pentestpartners
If malicious code executed under the process having impersonate privilege, it can setup a pipe \.\pipe\dockerLifecycleServer. Here the question arises under which process execute malicious code. For exploitation we need a vulnerable application for executing code and docker desktop for windows on same machine.
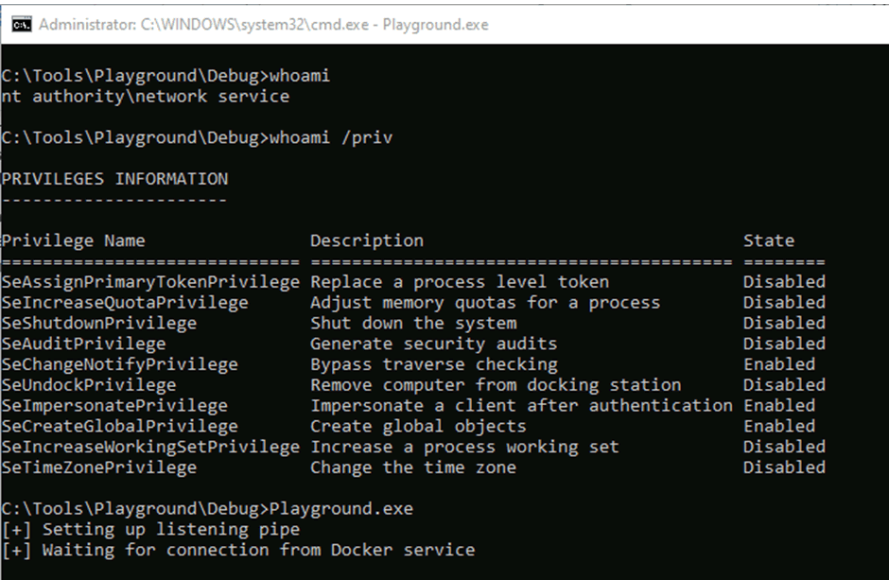
Image Source: pentestpartners
As soon as docker desktop service starts, it will connect to created malicious pipe. Named pipe impersonate client and docker service runs under high privilege NT AUTHORITY/SYSTEM, results into privilege escalation.
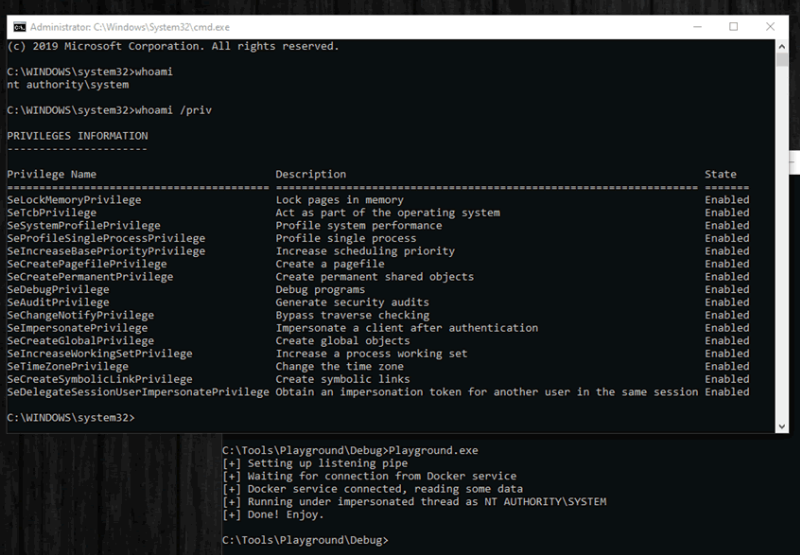
Image Source: pentestpartners
Affected version:
Docker Desktop for windows prior to 2.3.0.2
Advisory:
Docker release 2.3.0.2 to fix the vulnerability CVE-2020-11492. Download latest patch from following Docker webpage,
https://docs.docker.com/docker-for-windows/release-notes/
Mitigations:
Qualys Threat Research Lab provides protection with the QID(s)# 372758. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://www.pentestpartners.com/security-blog/docker-desktop-for-windows-privesc-cve-2020-11492/