Overview:
On January 2020, an Improper Access Control vulnerability had discovered in eG manager. Exploitation leads to Remote Code Execution. Improper Access Control describes failure in AAA (Authentication, Authorization, Accounting) security model.
The eG Manager is a central web portal which provides administrators with authenticated access over the web to the performance statistics stored in the repository.
Vulnerability Description:
eG Manager provides the different features, one of them is access key. eG Manager used predefined access key for authentication.
For login any web portal, we use login interface. In case of eG Manager, provides another way to access the its console. User can login using access key directly Attackers can use this access key, to access admin panel and perform Remote Code Execution.
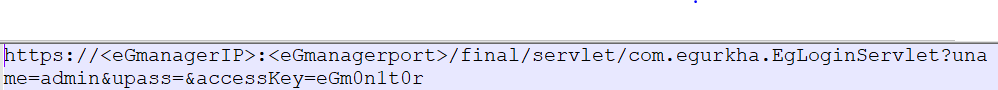
Access key can be found in their documentation. Using access key attacker can easily access admin panel without the need of authentication using below URL,
Successfully logged in to the eG management console, as eG Enterprise system will automatically pick password that corresponds to the specified user name from the database.
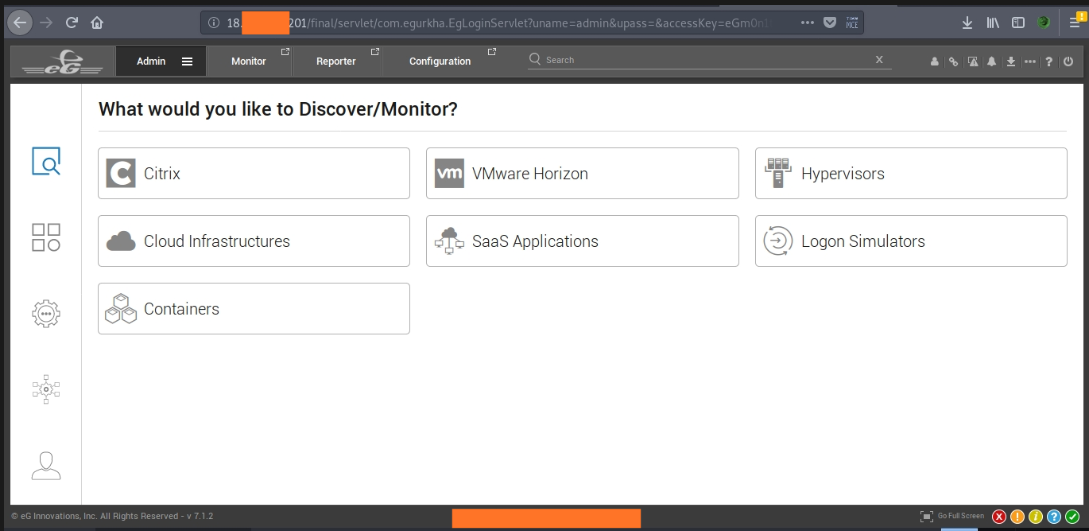
Image Source: pyaefromucsp
After successful login, attacker can do remote code execution. On admin panel command execution function available at Manager setting. Once the option enable, we can execute any commands in Remote Control Panel(Admin -> Agents-> Agent Status-> Remote Control)
Affected version:
eG Manager 7.1.2
Advisory:
Follow procedure from below webpage, upgrade your application to latest patch,
https://helpdesk.eginnovations.com/support/solutions/articles/6000170282-eg-agent-upgrade-procedure
References & Sources:
https://pyaefromucsp.blogspot.com/2020/02/eg-manager-v712improper-access-control_3.html