Summary:
Recently cyber-security researchers from Zecops disclosed a new critical vulnerability affecting SMB(Server Message Block)v3 protocol that may allow an attacker to leak kernel memory remotely, also when combined with a previously disclosed SMBGhost(CVE-2020-0796) bug, the flaw can further be exploited to achieve remote code execution on the target system.This issue was assigned under CVE-2020-1206.
Description:
SMB protocol is a client-server communication protocol that is used for sharing access to serial ports, files, printers, and other resources on a network. Researchers have found a new critical vulnerability in SMB(Server Message Block)v3 protocol that may allow an attacker to leak kernel memory remotely.
Similar to SMBGhost, SMBleed vulnerability exists in Srv2DecompressData function in the srv2.sys SMB server driver. The flaw exists due to the way Srv2DecompressData improperly handles specially crafted message requests sent to a targeted SMBv3 Server.
The Srv2DecompressData function receives compressed message that is sent by the client, allocates the required amount of memory, and then decompresses the data. Then, if the Offset field is not zero, it copies the data that is placed before the compressed data as is to the beginning of the allocated buffer.
Image Source: https://blog.zecops.com
Affected Products:
Windows 10 version 1903
Windows 10 version 1909
Windows 10 version 2004
Exploitation:
As per researchers “The message structure contains fields such as the amount of bytes to write and flags, followed by a variable-length buffer which is perfect for exploiting the bug ,a message can be crafted where we can specify the header, but the variable-length buffer contains uninitialized data”.
The uninitialized kernel data is treated as a part of message. The FinalCompressedSize is set to x + 0x1000 as well due to the implementation of the SmbCompressionDecompress function. In successful decompression, the FinalCompressedSize is updated to hold the value of CompressedBufferSize, that is the size of buffer.
Image Source: https://blog.zecops.com
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-1206. We’ve used a publicly available PoC on github to exploit the vulnerability.
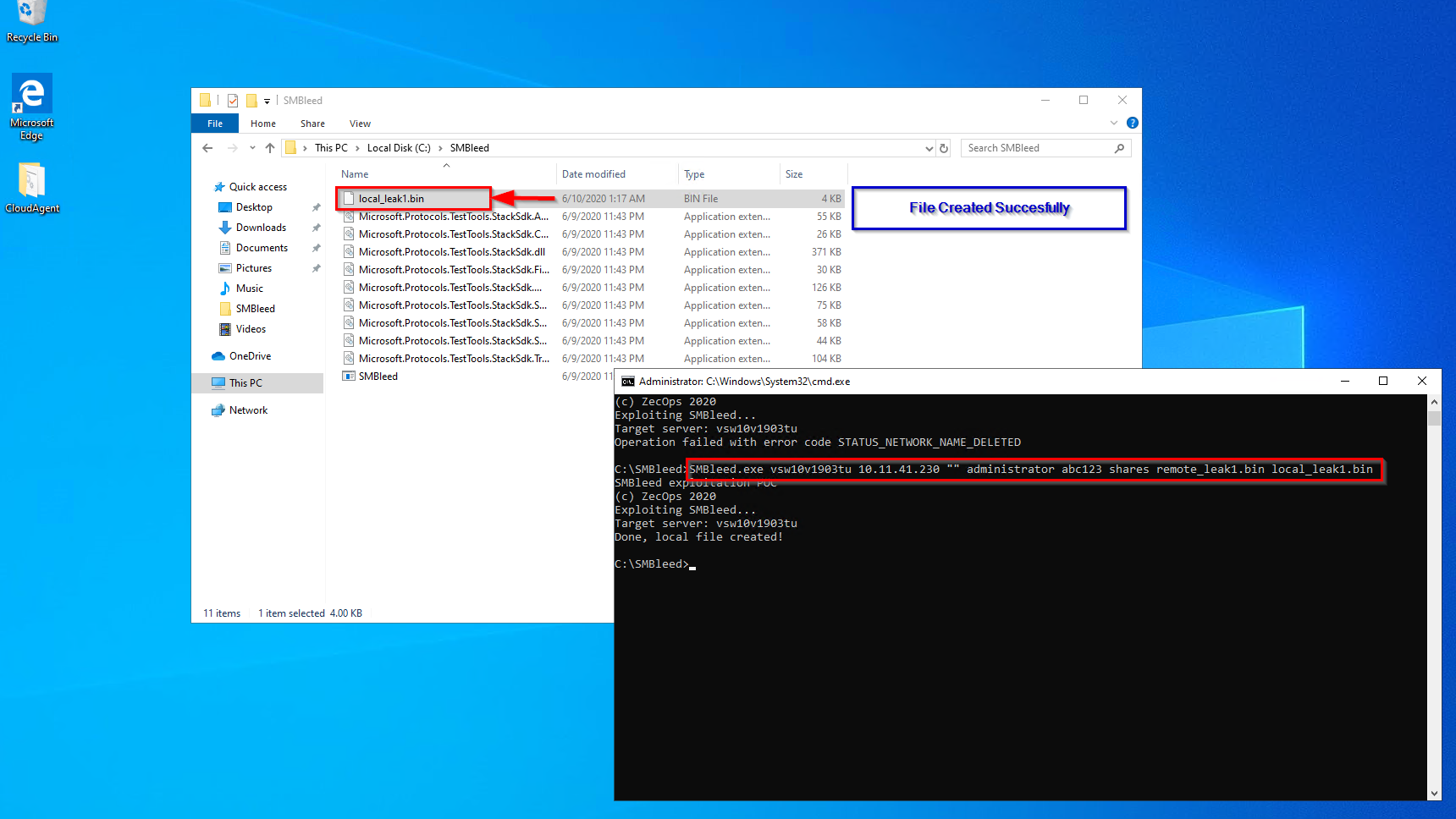
Exploit Source: https://github.com/ZecOps/CVE-2020-1206-POC
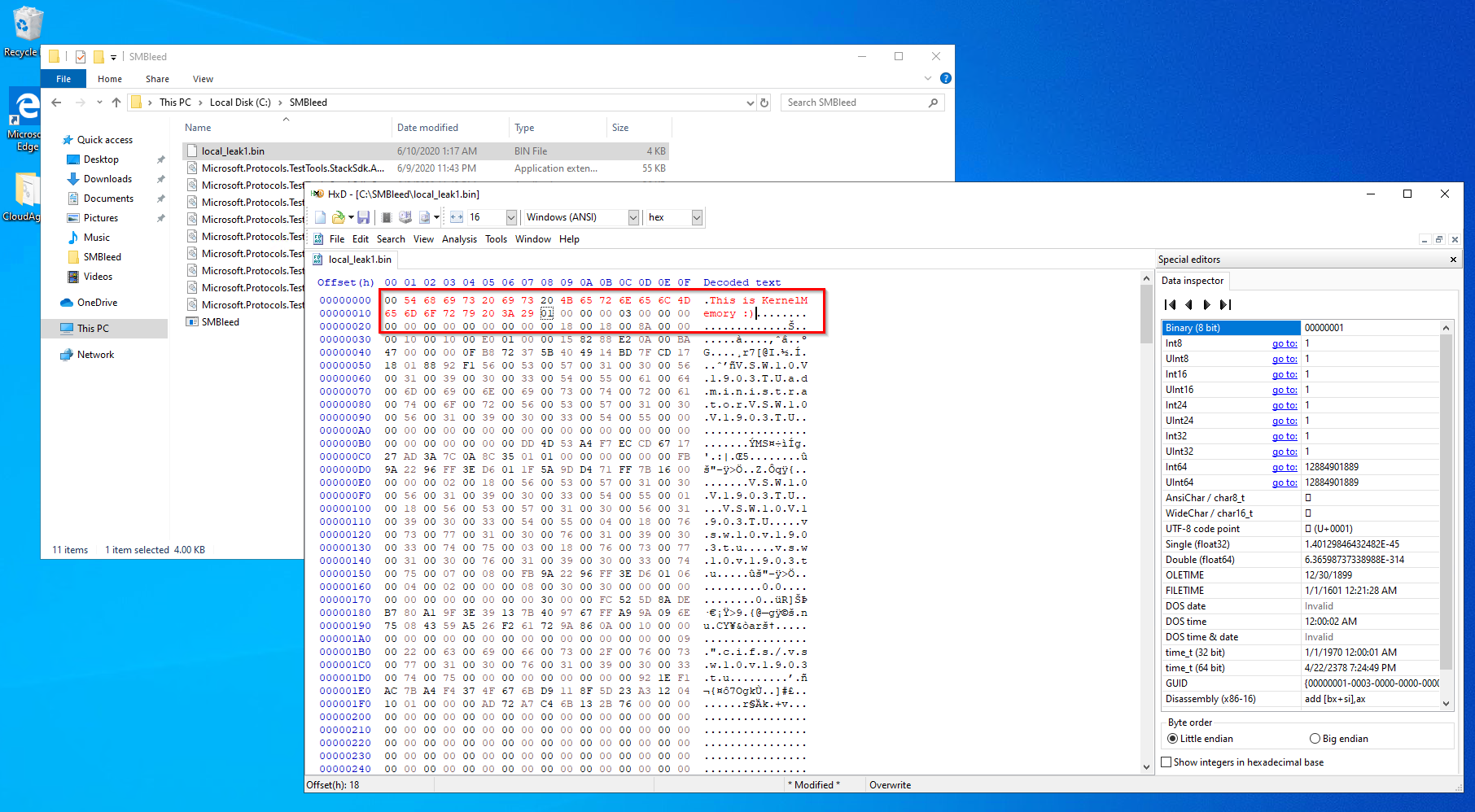
Exploit Source: https://github.com/ZecOps/CVE-2020-1206-POC
Further the researchers were able to Exploit the SMBleed bug and SMBGhost together to achieve Remote Code Execution on the target system. They have also released a Proof-of-concept demonstrating the vulnerability.
Source: https://github.com/ZecOps/CVE-2020-0796-RCE-POC
Mitigation:
Microsoft has officially released their official Advisory mentioning the patch and workaround for the vulnerability. Customers are requested to update their windows versions.
Qualys customers can scan their network with QID(s)#91651 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References and Sources:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1206
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0796