Treck IP stack implementations for embedded systems are affected by multiple zero-day vulnerabilities. Total 19 vulnerabilities in a widely used low-level TCP/IP software library developed by Treck, Inc have been discovered by the JSOF research lab, who calls them Ripple20.
Treck TCP/IP Stack
Treck IP network stack is designed for and used in a variety of embedded systems. The software is often licensed and integrated in various ways, including compiled from source, licensed for modification and reuse and eventually as a dynamic or static linked library.
Ripple20
The set of 19 vulnerabilities affects hundreds of millions of devices (or more) and include multiple remote code execution vulnerabilities.
As the researchers said in JSOF report “Ripple20 vulnerabilities are unique both in their widespread effect and impact due to supply chain effect and being vulnerabilities allowing attackers to bypass NAT and firewalls and take control of devices undetected, with no user interaction required. This is due to the vulnerabilities being in a low-level TCP/IP stack, and the fact that for many of the vulnerabilities, the packets sent are very similar to valid packets, or, in some cases are completely valid packets. This enables the attack to pass as legitimate traffic.”
Four of the Ripple20 vulnerabilities are critical, with CVSS scores over 9 and enable Remote Code Execution. One of the critical vulnerabilities is within the DNS protocol and potentially could be exploitable by a remote attacker, or even on devices that are not connected to the internet.
| CVE ID | CVSS V3 | Short Summary | Potential Impact |
| CVE-2020-11896 | 10 | Improper handling of crafted IPv4 packets by a device which support IPv4 tunneling | Remote Code Execution |
| CVE-2020-11897 | 10 | Improper handling of crafted IPv6 packets | Remote Code Execution |
| CVE-2020-11901 | 9 | Improper processing of a DNS request | Remote Code Execution |
| CVE-2020-11898 | 9.1 | Improper Handling of Length Parameter by IPv4/ICMPv4 component | Remote Code Execution |
Rest of the vulnerabilities have CVSS score in between 3.1 and 8.2, and can cause Denial of Service, Remote Code Execution or Disclosure of Sensitive Information.
| CVE ID | CVSS V3 | Short Summary | Potential Impact |
| CVE-2020-11900 | 8.2 | Possible Double Free issue in IPv4 tunneling component while handling certain packets | Remote Code Execution |
| CVE-2020-11902 | 7.3 | Improper validation in IPv6OverIPv4 tunneling component while handling certain packets | Remote Code Execution |
| CVE-2020-11904 | 5.6 | Integer overflow while handling certain packets | Remote Code Execution |
| CVE-2020-11899 | 5.4 | Insufficient sanitization in IPv6 component while processing certain packets | Denial of Service |
| CVE-2020-11903 | 5.3 | Out-of-bounds Read in DHCP component while handling some packets | Sensitive Info Disclosure |
| CVE-2020-11905 | 5.3 | Out-of-bounds Read in DHCPv6 component while handling some packets | Sensitive Info Disclosure |
| CVE-2020-11906 | 5 | Improper packet validation in Ethernet Link Layer component | Remote Code Execution |
| CVE-2020-11907 | 5 | Improper sanitization of Length Parameter in TCP component | Remote Code Execution |
| CVE-2020-11909 | 3.7 | Improper Input Validation by IPv4 component when handling certain packets | Sensitive Info Disclosure |
| CVE-2020-11910 | 3.7 | Improper Input Validation by ICMPv4 component when handling certain packets | Sensitive Info Disclosure |
| CVE-2020-11911 | 3.7 | Improper access control in ICMPv4 component when handling certain packets | Denial of Service |
| CVE-2020-11912 | 3.7 | Insufficient input validation in TCP component while handling crafted packets | Denial of Service |
| CVE-2020-11913 | 3.7 | Improper Input Validation by IPv6 component when handling certain packets | Sensitive Info Disclosure |
| CVE-2020-11914 | 3.1 | Improper Input validation in ARP component when handling certain packets | Sensitive Info Disclosure |
| CVE-2020-11908 | 3.1 | Improper Null Termination in DHCP component during handling of crafted packets | Sensitive Info Disclosure |
CVSSv3 Scores were provided by JSOF in Ripple20 Advisory.
“Ripple20 vulnerabilities are unique both in their widespread effect and being vulnerabilities allowing attackers to bypass NAT and firewalls and take control of devices undetected, with no user interaction required. This is due to the vulnerabilities being in a low-level TCP/IP stack, and the fact that for many of the vulnerabilities, the packets sent are very similar to valid packets, or, in some cases are completely valid packets. This enables the attack to pass as legitimate traffic.” the JSOF researchers explained.
Consequence
Ripple20 can have some serious consequences.
Successful Exploitation of any of the Ripple20 vulnerability can allow
- A Remote attacker to take control over a device within the network, if internet facing.
- An attacker who has already managed to infiltrate a network can use the library vulnerabilities to target specific devices within it.
- An attacker could broadcast an attack capable of taking over all impacted devices in the network simultaneously.
- An attacker may utilize affected device to remain hidden within the network for years
- A sophisticated attacker can potentially perform an attack on a device within the network, from outside the network boundaries, thus bypassing NAT configurations with the help of a MITM attack or a DNS cache poisoning.
Affected Products
Affected version of Treck TCP/IP stack is different for each CVE.
As per the report published by JSOF, researchers explained “Ripple20 reached critical IoT devices from a wide range of fields, involving a diverse group of vendors. Affected vendors range from one-person boutique shops to Fortune 500 multinational corporations, including HP, Schneider Electric, Intel, Rockwell Automation, Caterpillar, Baxter, as well as many other major international vendors suspected of being of vulnerable in , industrial control ,medical, transportation, enterprise, energy (oil/gas), telecom, retail and commerce, and other industries. The list of vendors has been assembled carefully by different means and represents vendors that may be affected. The list only contains vendors that CISA ICS-CERT has listed in an internal document as having been contacted. “
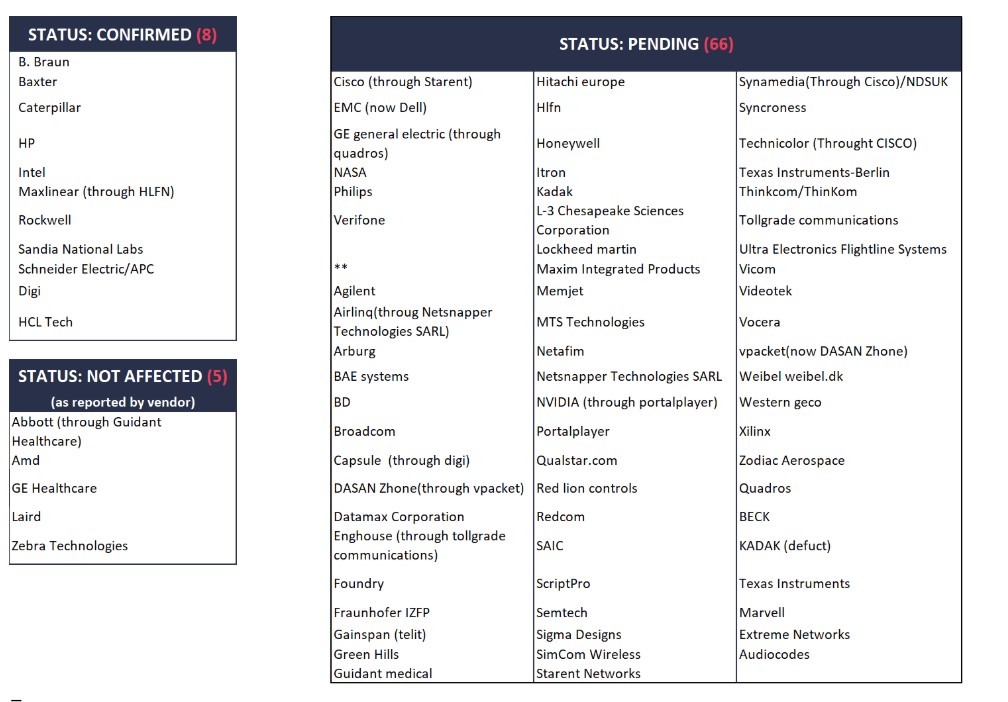
The following vendors are affected or might be affected:
PoC
JSOF has demonstrated exploitation of these vulnerabilities on different devices as a proof-of-concept.
Please check out the PoC demo here.
Workaround
Treck released patches to address the Ripple20 vulnerabilities, but in some cases it’s not always possible to apply the patches.
- Minimize network exposure for embedded and critical devices, keeping exposure to the minimum necessary, and ensuring that devices are not accessible from the Internet unless essential.
- Segregate OT networks and devices behind firewalls and isolate them from the business network.
- Enable only secure remote access methods
- Blocking network attacks via deep packet inspection. Like modern switches, routers, and firewalls will drop malformed packets with no additional configuration.
Further Mitigation for operators and networks or for device vendors are available on Github and Ripple20.
How to Detect Vulnerable assets ?
Qualys has released the information gathered (IG) QID 48106 to detect Treck IP stacks on systems by remote unauthenticated scan using TCP/IP_Fingerprint as well as an ICMP probe.
Along with the IG QID 48106, Qualys also released vulnerability QID 38789 for Multiple HP Printers Network Stack Potential Vulnerabilities.
Additional References
JSOF has been working with several organizations to coordinate the disclosure of the flaws, including ICS CERT, CERTCC, JPCERT/CC, CERT-IL, tech giant like Intel, HP,Schneider Electric have released their own advisories.
https://www.jsof-tech.com/ripple20/
https://www.kb.cert.org/vuls/id/257161/
https://github.com/CERTCC/PoC-Exploits/blob/master/vu-257161/recommendations.md
https://www.helpnetsecurity.com/2020/06/16/flaws-tcp-ip-library/
How long until we have unauthenticated checks for this given the researchers are making available their discovery scripts available on request ?