Summary:
A sensitive and yet extreme scope changing vulnerability was disclosed as zero-day recently in Netgear Routers. Adam, who has deep-dived into Netgear routers had tested various models and firmware has come up with this idea of this vulnerability. As an organization, Netgear it trying to workaround for the same, henceforth, no official advisory or CVE have been assigned to this.
Description:
The flaw is observed in the httpd service used by Netgear routers to listen on TCP port 80. The length of the user-supplied data lacks in input validation, while copying it to fixed length. Ideally, the server should have appropriate parsing to user supplied data that comes from network using CGI functions. Firstly, this router lacks in parsing data using CGI data function, and again, they do not use stack cookies.
As Adam quotes “The R7000 does not use stack cookies. In fact, of all the Netgear products which share a common codebase, only the D8500 firmware version 1.0.3.29 and the R6300v2 firmware versions 1.0.4.12-1.0.4.20 use stack cookies. However, later versions of the D8500 and R6300v2 stopped using stack cookies, making this vulnerability once again exploitable.”
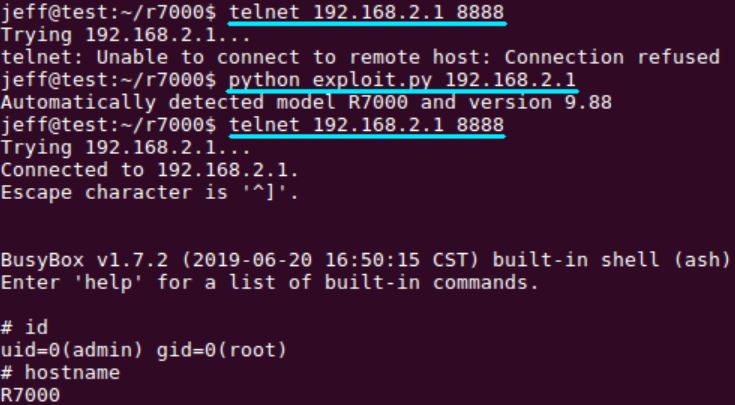
Image Source: Adam
No authentication process is involved. An attacker can bypass the authentication, if any as well as get the root level privileges to execute command remotely. This vulnerability affects firmware as early as 2007 (WGT624v4, version 2.0.6).
Affected Products:
Multiple models and firmwares were affected, whole list can be found here.
Advisory:
https://kb.netgear.com/000061982/Security-Advisory-for-Multiple-Vulnerabilities-on-Some-Routers-Mobile-Routers-Modems-Gateways-and-Extenders
Remediation to risks:
Netgear have released an advisory covering multiple products and their firmware versions, quoting “Vulnerability was already fixed in an earlier firmware release. The current firmware release or firmware hotfix includes all earlier fixes.”
Threat_Protect:
Qualys customers can scan their network with QID(s)# 13801 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/grimm-co/NotQuite0DayFriday/blob/master/2020.06.15-netgear/exploit.py
- https://blog.grimm-co.com/2020/06/soho-device-exploitation.html
- https://www.zerodayinitiative.com/advisories/ZDI-20-712/