For 2020, June’s Patch Tuesday, Microsoft published Advisories addressing Multiple Vulnerabilities in Microsoft Windows Defender.
CVE-2020-1163 and CVE-2020-1170 was assigned to these vulnerabilities.
Microsoft Windows Defender
Microsoft Defender is an anti-malware component of Microsoft Windows, designed to protect computers from viruses, spyware and other forms of malware.
CVE-2020-1163 and CVE-2020-1170
An elevation of privilege vulnerability exists in Defender that leads to arbitrary file deletion on the system. The vulnerability exists due to application does not properly impose security restrictions in Windows Defender. A local user can use a specially crafted application and take control of an affected system.
Recently a detailed analysis Report of CVE-2020-1170 is published.
Let’s see this vulnerability in Nutshell.
Vulnerability Details
The Vulnerability exist due to incorrect way of handling Windows Defender log files. MpCmdRun.log and MpSigStub.log, these two files are for Windows Defender logs, located in C:\Windows\Temp.
When Signatures updates for Windows Defender, some information is being written to C:\Windows\Temp\MpCmdRun.log by Windows Defender (as NT AUTHORITY\SYSTEM)
Administrators and SYSTEM have Full Control over these files by default, whereas normal users can’t even read them or have write access to them, but when normal user (low-privileged) trigger the Signature Updates process, information will be written to these log files as NT AUTHORITY\SYSTEM.
With help of Log Rotation Mechanism, an attacker can exploit this vulnerability. In Log Rotation, every time Signatures Updates, it writes information in log files and when these log files reached to the file size limit (16MB), the original file renamed as MpCmdRun.log.bak and creates a new one.
so, an attacker can create the directory C:\Windows\Temp\MpCmdRun.log.bak\ and set it as a mountpoint to another location on the filesystem. To trick the system using MpCmdRun.log.bak, MpCmdRun.log file must be filled up to 16 MB. An attacker needs to run Update-MpSignature command in a loop for 10000 times. According to the link, the researcher has been able to exploit this vulnerability using this same trick to demonstrate the PoC.
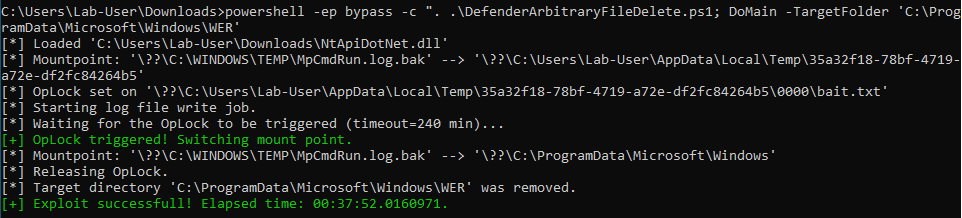
C:\ProgramData\Microsoft\Windows\WER is specified as the target directory to delete, because, once this folder has been removed, an attacker can get code execution as NT AUTHORITY\SYSTEM.
From directory deletion to SYSTEM shell process explained by @jonaslyk can be used to escalate privileges on the system.
Vulnerable Versions:
Windows Defender anti-malware platform Version prior to 4.18.2005.1
To know more about Vulnerable Platform please visit CVE-2020-1163 and CVE-2020-1170
Mitigation
Microsoft advised users to ensure update for the Windows Defender is installed to mitigate any risk.
Qualys has released QID 91649 to Detect this vulnerability.
Additional References
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1163
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1170
https://itm4n.github.io/cve-2020-1170-windows-defender-eop/
https://secret.club/2020/04/23/directory-deletion-shell.html