Overview:
An active privilege escalation vulnerability was observed in Docker Desktop application. This vulnerability is assigned as CVE-2020-10665 and the research credits belongs to ACTIVELabs team. Successful exploitation leads to local elevation of privilege to NT AUTHORITY\SYSTEM.
Docker Desktop for Windows is an easy-to-install application that enables you to build and share containerized applications and microservices.
POC is available on GitHub.
Description:
Vulnerability occurs due to improper handling of the collection of diagnostics with Administrator privileges.
Docker desktop troubleshoot page have an option “Run Diagnostics” to diagnose any issues. This operation was performed under the NT AUTHORITY\SYSTEM context with no user impersonation. Process com.docker.diagnose.exe does all this diagnostics data collection operation. During this operation, diagnose process creates globally unique Identifier (GUID) folder under Appdata folder. Under this newly created folder zip file will be created to write diagnostic data.
The bug exists because process grants Full Control permissions to the zip file for the Everyone group diagnose.
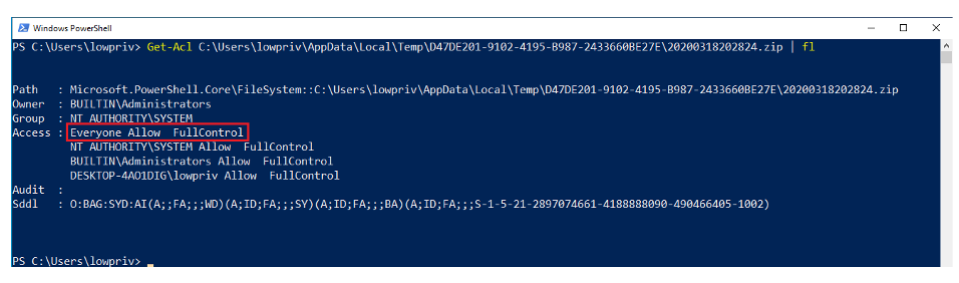
Image source: ActiveCyber
“In essence, we have privileged processes that perform several operations on a file under a folder that is controllable by a standard non-privileged user, leading to an arbitrary DACL permissions overwrite.” says the research team of ACTIVELabs.
Researchers have used hard links to exploit this vulnerability. Once the permissions were modified, they have used the method discovered by Andrea Pierini here to achieve elevation of privileges.
Affected products:
- Docker Desktop Enterprise prior to 2.1.0.9
- Docker Desktop for Windows Stable before prior to 2.2.0.4
- Docker Desktop for Windows Edge before prior to 2.2.2.0
Advisory:
To protect your system, affected organizations are advised to download the latest patch from following Docker webpage,
https://docs.docker.com/docker-for-windows/release-notes/
Detection:
Qualys Threat Research Lab provides detection with the QID(s)# 372941. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.activecyber.us/activelabs/docker-desktop-local-privilege-escalation-cve-2020-10665
- https://github.com/spaceraccoon/CVE-2020-10665
- https://decoder.cloud/2019/11/13/from-arbitrary-file-overwrite-to-system/
- https://docs.docker.com/docker-for-windows/release-notes/