On July 14, 2020, Microsoft issued a new security advisory on Microsoft Windows Patch Day – addressing CVE-2020-1350, also known as SigRed – a Remote Code Execution (RCE) vulnerability in Windows Domain Name System (DNS) servers.
SigRed affects Windows servers that are configured to run the DNS Server role as described in advisory.
Description
Microsoft mentioned that, “it found no evidence to show that the bug has been actively exploited by attackers and advised users to install patches immediately”. Furthermore, it added that the vulnerability has the potential to spread via malware between vulnerable computers without any user interaction. No authentication is mandatory to execute this wormable vulnerability. A nefarious actor who is successful in exploiting this vulnerability could run arbitrary code in the Local System Account.
The flaw impacts only Windows DNS servers and not DNS server client. Check Point Research team members Sagi Tzadik and Eyal Itkin have presented their research to Microsoft and shown it in a video here.
The following components are vulnerable to CVE-2020-1350:
Function: dns.exe!SigWireRead
Vulnerability Type: Integer Overflow leading to Heap-Based Buffer Overflow
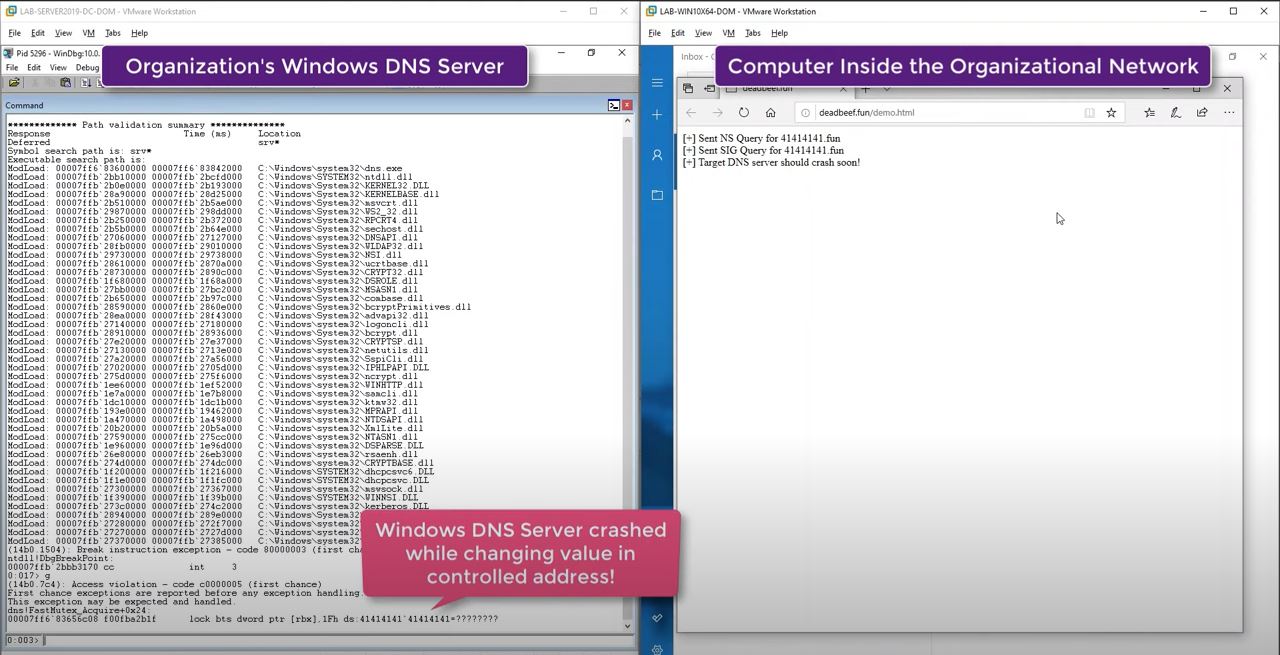
Image Source: Check Point
“Without any human interaction or authentication, a single exploit can start a chain reaction that would allow attacks to spread from one vulnerable machine to another,” the researcher said. “This means that a single compromised machine could spread this attack throughout an organization’s network within minutes of the first exploit.”
Affected Windows Products
Windows Server 2004
Windows Server 2008
Windows Server 2012
Windows Server 2016
Windows Server 2019
Mitigation
Microsoft has officially released a public advisory for the affected products and their patches. Customers are advised to visit the Microsoft Support Portal and apply the patch on priority to mitigate risks. Alternatively, the following registry modification can be used as a workaround for this vulnerability.
Workarounds
Registry modification
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
DWORD = TcpReceivePacketSize
Value = 0xFF00
Note: You must restart the DNS Service for the workaround to take effect.
Workaround/Mitigation Detection
Qualys Policy Compliance customers can evaluate workaround based on Control ID
18935 Status of the ‘TcpReceivePacketSize’ parameter within the ‘HKLM\System\CurrentControlSet\Services\DNS\Parameters’ registry key
Detection
Qualys customers can scan their network with QID# 91662 to detect vulnerable Microsoft DNS assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources:
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350
- https://www.youtube.com/watch?v=PUlMmhD5it8
- https://research.checkpoint.com/2020/resolving-your-way-into-domain-admin-exploiting-a-17-year-old-bug-in-windows-dns-servers/
- https://thehackernews.com/2020/07/windows-dns-server-hacking.html