Overview:
Recently, an authenticated RCE vulnerability was found in the Wing FTP Server. This vulnerability allows authenticated remote attackers to execute arbitrary commands on the targeted server.
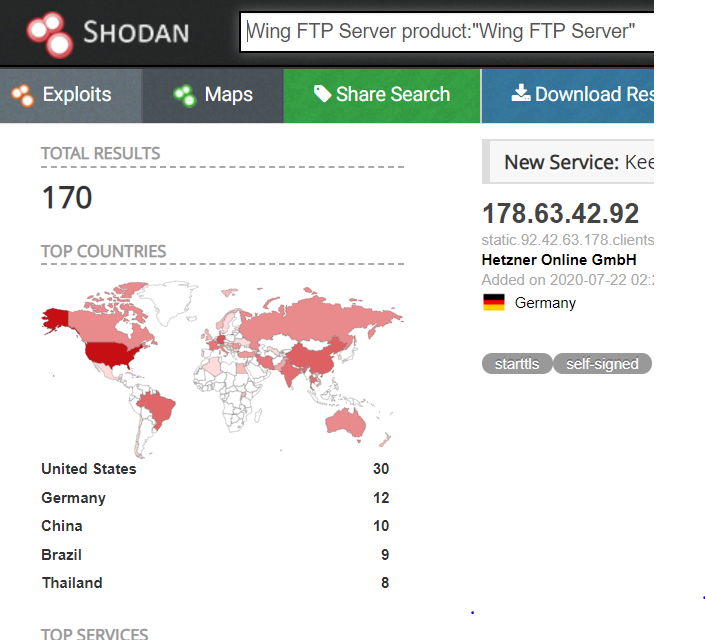
On Shodan, we observed more than 150 devices that are publicly available on the internet, which may be vulnerable.
Image Source: Shodan
POC is available on ExploitDB
Description
Following vulnerabilities found in Wing FTP server:
- Admin Credentials on HTTP Request:When an admin logs in to the Wing FTP Server, the credentials are sent in plain text.
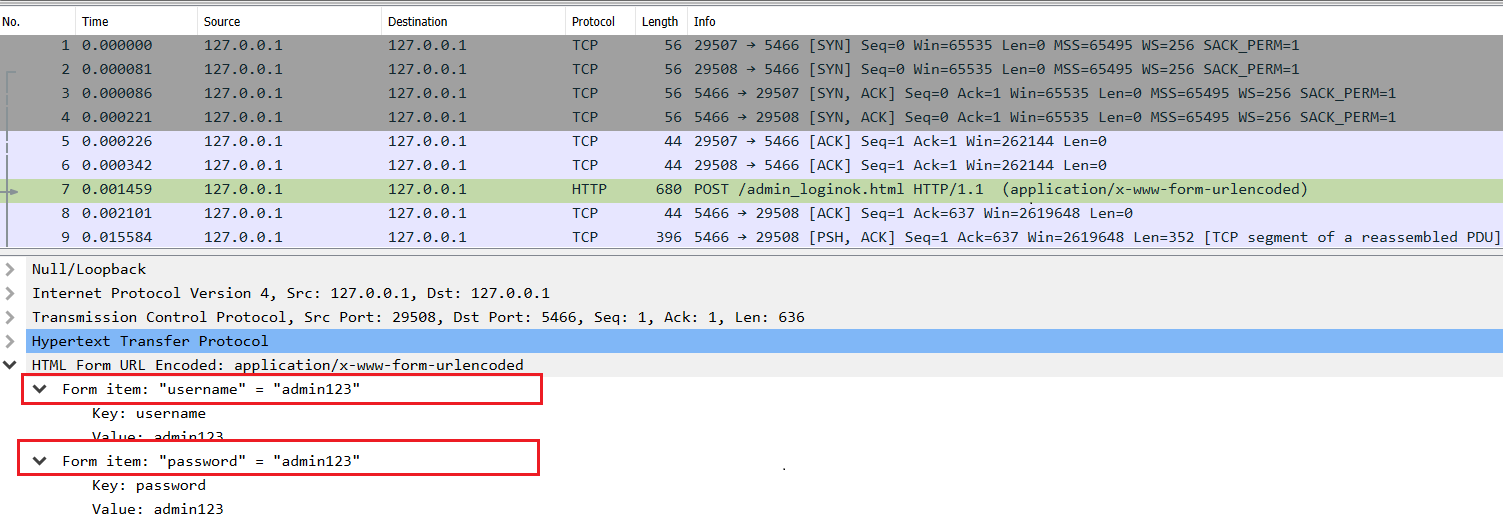
Image Source: Qualys Lab
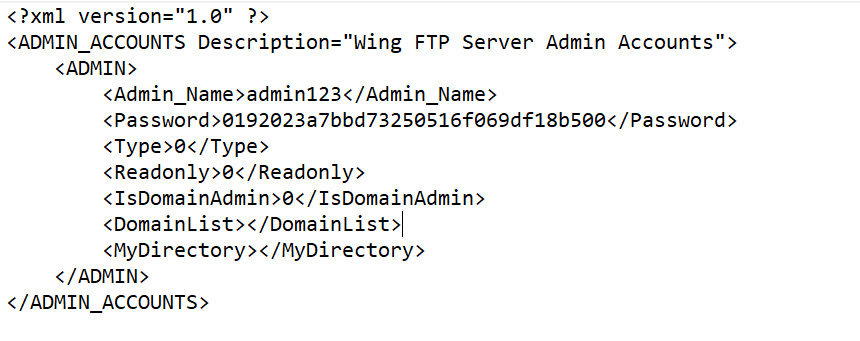
- Unprotected Store Credentials:
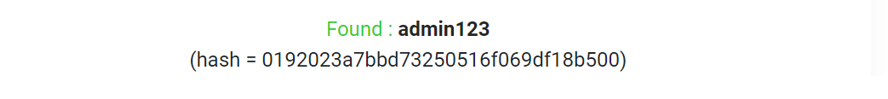
A file named admins.xml contains the username and MD5 hashed password. This file can be found in the C:\Program Files\Wing FTP Server\Data\_ADMINISTRATOR location.
This hash password can easily convert into plain text using an online decrypter.
- Remote Code Execution (authenticated):
Wing FTP Server console is written in LUA language. For authenticated users, this console can be exploited to obtain a reverse shell using the os.execute() function, which is native to LUA.
To obtain a reverse shell, generate a payload and send it to Wing FTP server using the following POST http request:
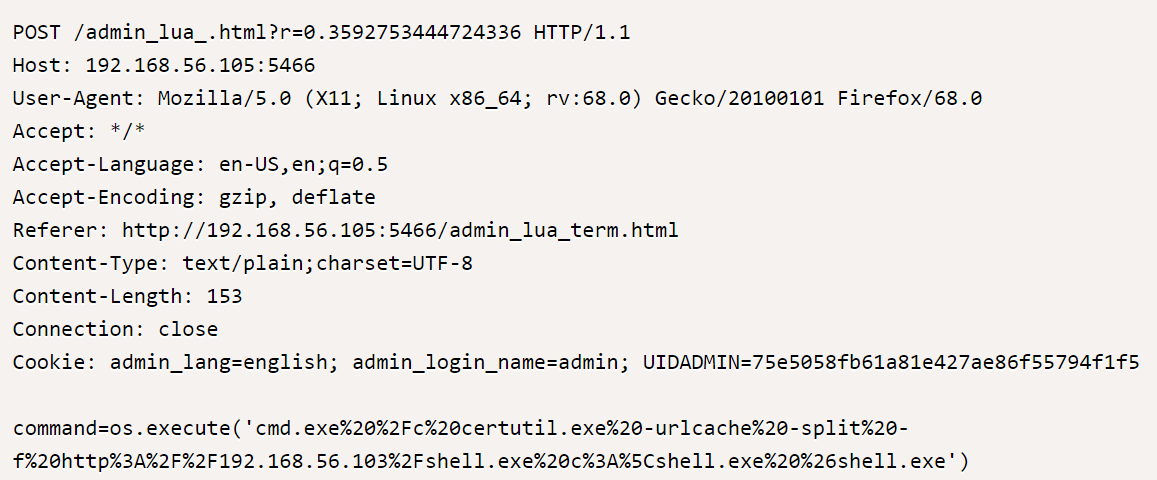 Image Source: exploitdb
Image Source: exploitdb
Affected Products
Wing FTP Server 6.3.8 and earlier versions may also be affected as the versions earlier than 6.3.8 send credentials in plain text format and stores the MD5 hash password in the admins.xml file.
Remediation
Detection
Qualys customers can scan their network with QID 373310 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.