In mid-June 2020, QNAP devices were found to be vulnerable to older Qsnatch malware campaigns of 2014 and 2017.
Description
The vulnerabilities due to Qsnatch has high to critical impact on QNAP NAS devices. A joint advisory published by CISA and NCSC says that “it has infected 62,000 devices worldwide, including 3900 in the UK and 7600 in the US”.
The malware blocks any sort of firmware updates to run on the infected devices. It does this in various ways such as a credential scraper, SSH backdoor, CGI password logger, webshell functionality and the ability to exfiltrate a predetermined list of files, including system configs and log files.
According to CISA, “The infection vector has not been identified, but QSnatch appears to be injected into the device firmware during the infection stage, with the malicious code subsequently run within the device, compromising it. The attacker then uses a domain generation algorithm (DGA)—to establish a command and control (C2) channel that periodically generates multiple domain names for use in C2 communications—using the following HTTP GET request:
HTTP GET https://[generated-address]/qnap_firmware.xml?=t[timestamp]”
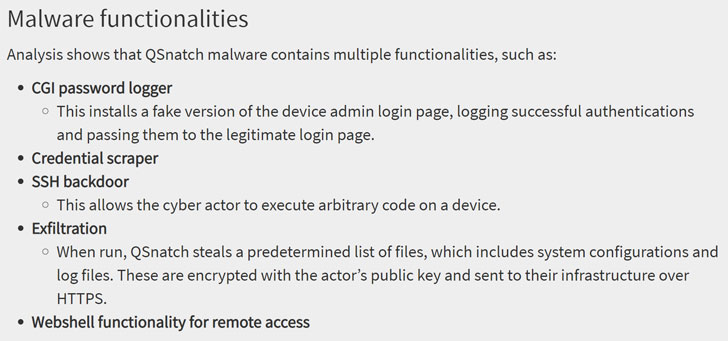
Image Source: Thehackernews
Steps to remediate and mitigate the risks of “Derek” are enlisted in QNAP’s advisory, nas-201911-01.
QNAP NAS devices affected by the eCh0raix ransomware include QNAP TS-251, QNAP TS-451, QNAP TS-459 Pro II, and QNAP TS 253B.
Affected Products
QNAP NAS devices
Detection:
Qualys customers can scan their network with QID 48121 to detect QNAP NAS devices. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources:
- https://www.qnap.com/en/security-advisory/nas-201911-01
- https://us-cert.cisa.gov/ncas/alerts/aa20-209a
- https://www.ncsc.gov.uk/news/legacy-risk-malware-targeting-qnap-nas-devices
- https://www.infosecurity-magazine.com/news/ukus-governments-warn-of-qnap-nas/?utm_source=dlvr.it&utm_medium=twitter
- https://thehackernews.com/2020/07/qnap-nas-malware-attack.html