Overview
A Content Security Policy bypass vulnerability (CVE-2020-6519) exists in Google’s Chromium-based browsers, which could allow attackers to steal data and execute arbitrary codes.
Content Security Policy (CSP) is a set of rules that helps detect which content sources can be trusted and which ones should be blocked. CSP helps detect and mitigate certain types of attacks, including Cross Site Scripting and data injection attacks.
Gal Weizman, security researcher from PerimeterX who discovered the vulnerability, says “Having a vulnerability in Chrome’s CSP enforcement mechanism doesn’t directly mean that sites are breached, as the attackers also need to manage to get the malicious script called from the site (which is why the vulnerability was classified as medium severity).”
The researcher has provided POC files and a demonstration video on GitHub as disclosed to Google Chrome project.
Test your browser
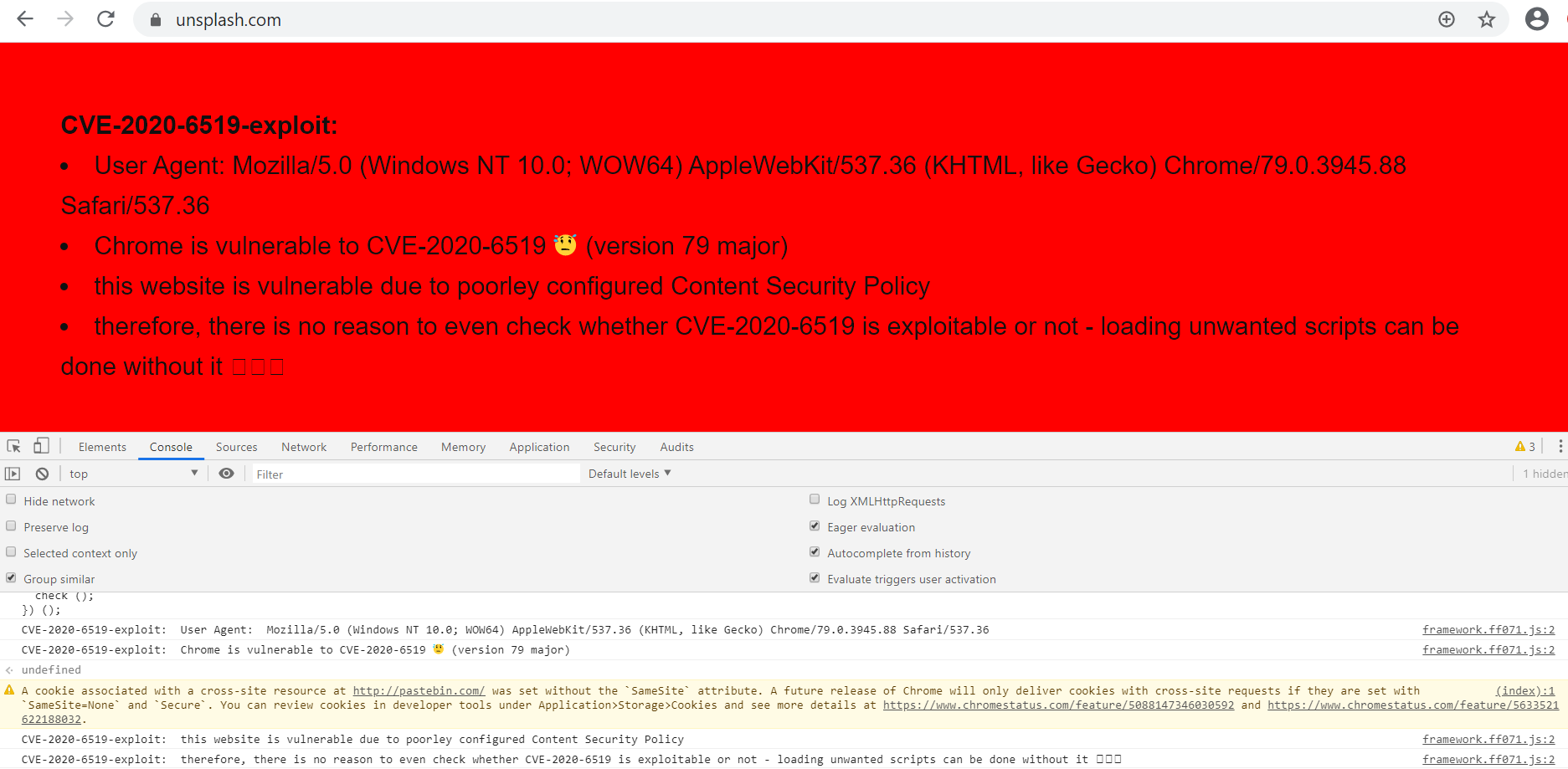
To check if your Chrome browser is vulnerable, users can use the POC available on GitHub. Run the POC code into DevTools Console browser and load any website. Following content will be displayed if your browser and website is vulnerable.
Image Source: Qualys Lab
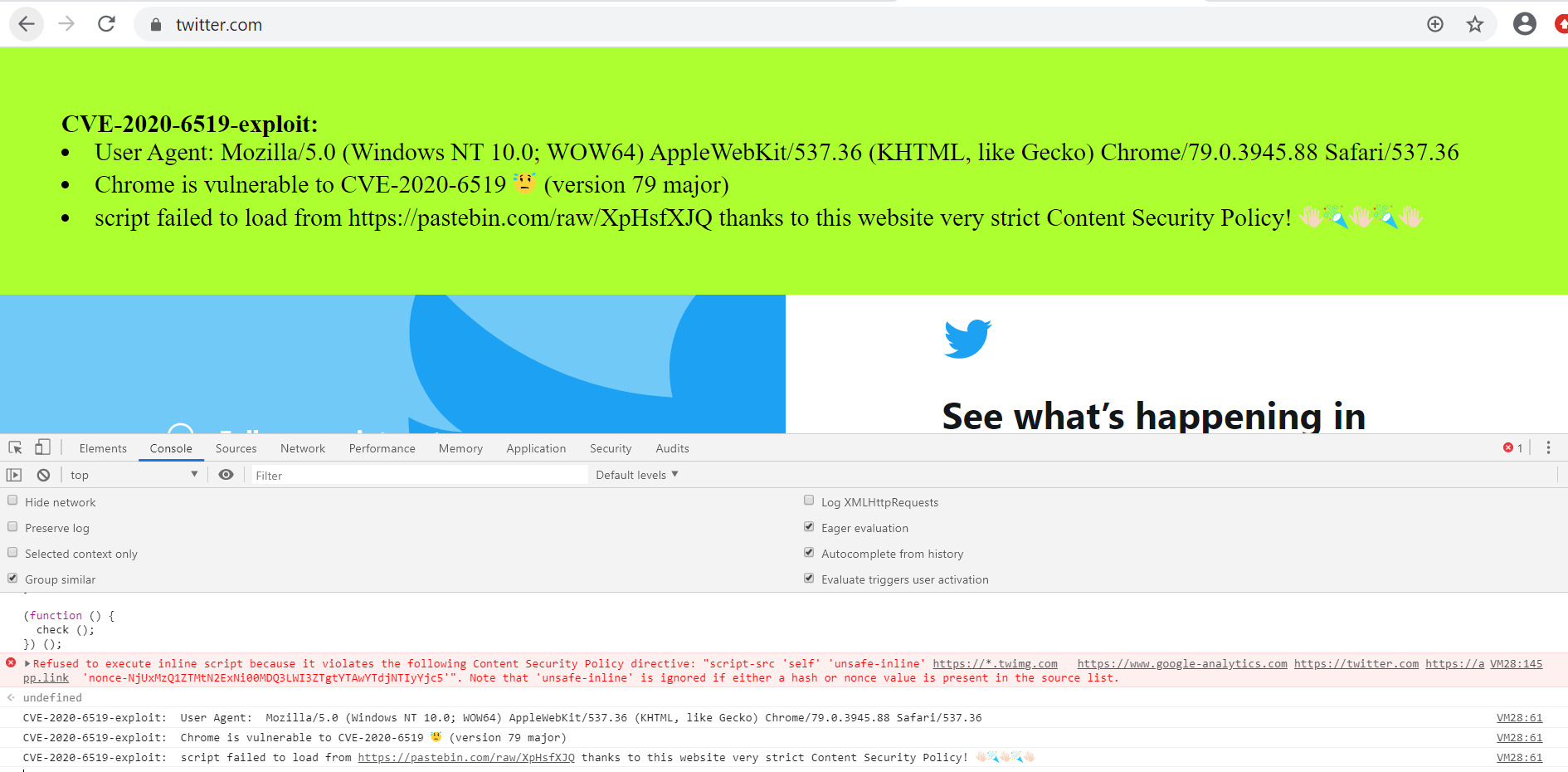
Some websites such as Twitter, Github, and LinkedIn are protected by CSP, and are not vulnerable as they have implemented CSP using nonce or hash. Testing POC for these websites shows that although Google Chrome is vulnerable, the website is not due to its strict content security policy.
Image Source: Qualys Lab
Remediation
- Ensure your CSP policies are well defined.
Consider adding additional layers of security such as nonce or hash. This requires server-side implementation.
CSP alone is not enough for most websites, so consider adding additional layers of security. Consider JavaScript-based detection and monitoring of Shadow Code for real-time mitigation of web page code injection.
- Make sure your Chrome browser version is 84 or higher.
Affected products
Google Chrome versions 73 through 83.
Detection
Qualys customers can scan their network with QID 373151 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References: