Overview
Cisco has addressed four vulnerabilities in Cisco Jabber for Windows. The most critical of these vulnerabilities, CVE-2020-3495, when exploited, allows an attacker to execute arbitrary code via a crafted chat message.
Description
Cisco Jabber is an instant messaging and video-conferencing application. Cisco Jabber uses the Chromium Embedded Framework (CEF) to embed a Chromium-based web browser inside the application to support web technologies in instant messaging chatting. Cisco has released advisories and security updates to fix CVE-2020-3495, CVE-2020-3430, CVE-2020-3498, and CVE-2020-3537 for Cisco Jabber on Windows.
CVE-2020-3495 (CVSS v3 score 9.9) is an arbitrary code execution vulnerability when handling Extensible Messaging and Presence Protocol (XMPP) messages. Cisco Jabber uses XMPP to support HTML content in instant messaging. The HTML content received from a chat message goes through the anti XSS filter and is then passed to the embedded (CEF) engine to process. The vulnerability exists in the XSS filter which fails to filter all the unsafe attributes. “onanimationstart” is found to be able to pass the XSS filter then gets its script executed in the CEF engine. This was only a cross-site scripting vulnerability. However due to a vulnerability in function “window.CallCppFunction” it was possible to jailbreak the CEF engine sandbox.
To exploit this vulnerability, attackers can send a chat message containing:
onanimationstart="window.CallCppFunction('OPEN_FILE', FILE)"
The “FILE“ will be executed on the victim’s system with Cisco Jabber process’s privilege. No user interaction is required as long as the attackers can send XMPP messages to the victim. The exploit process is as easy as sending a chat message. That’s why we think this vulnerability is highly critical and “wormable”.
CVE-2020-3430 is a protocol handler command injection vulnerability. Cisco Jabber for Windows calls “CiscoJabber.exe” when a user clicks a URI which contains the protocol recognized by the application, as shown below:
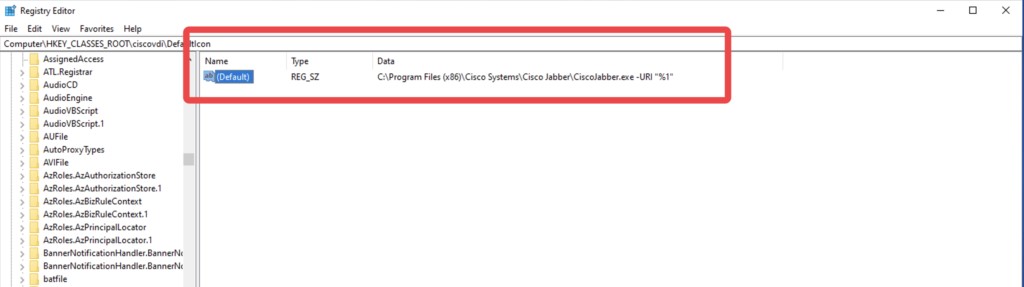
Command injection happens when the URI contains spaces. The command injected after the spaces will be executed on the victim’s system.
CVE-2020-3498 and CVE-2020-3537 are sensitive data disclosure vulnerabilities. CVE-2020-3537 allows attackers to steal sensitive information after convincing the victim to click the provided link. CVE-2020-3498 doesn’t need user interaction. It can simply be exploited by sending specially crafted messages to steal sensitive information.
Affected Products
These vulnerabilities affect all supported versions of Cisco Jabber for Windows.
Remediation
Cisco has released fixed versions to address these vulnerabilities.
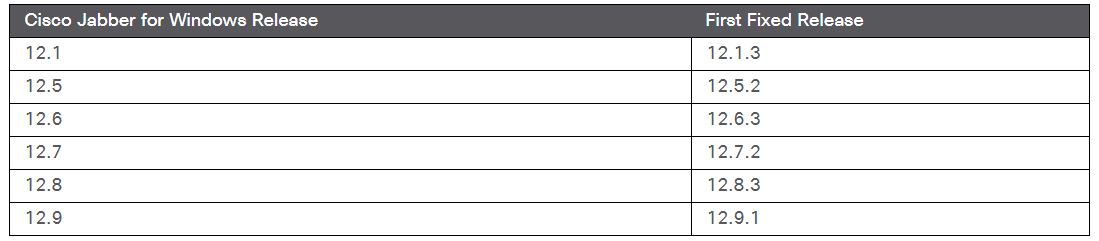
Image Source: Cisco
Detection
Qualys customers can scan their network with QID 316694 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-jabber-UyTKCPGg
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-jabber-vY8M4KGB
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-jabber-G3NSjPn7
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-jabber-ttcgB9R3
https://watchcom.no/nyheter/nyhetsarkiv/uncovers-cisco-jabber-vulnerabilities/