Within a span of three months, one more critical vulnerability with a score of 10.0 has been observed in PAN-OS devices. When a Captive Portal or Multi-factor authentication interface is enabled on PAN-OS devices, it is considered to be vulnerable to critical buffer overflow vulnerability. This vulnerability is classified as CWE-120 and assigned CVE-2020-2040, on Sept 9, 2020.
This vulnerability disturbs the cadence of PAN-OS devices primarily because of two factors. Firstly, it doesn’t require any authentication, and secondly, it has a potential to disrupt system processes and execute arbitrary code injection. Once exploited, an unauthenticated user can gain root privileges by sending a malicious request to the PAN-OS Captive Portal or the Multi-Factor Authentication (MFA) interface. This issue is applicable only where either Captive Portal is enabled or MFA is configured as per the steps mentioned in the Configure Multi-Factor Authentication section of the PAN-OS® Administrator’s Guide.
So far, there has been no information of this CVE being exploited in the wild, and more than ~5k PAN-OS devices are active at the time when this blog was published.
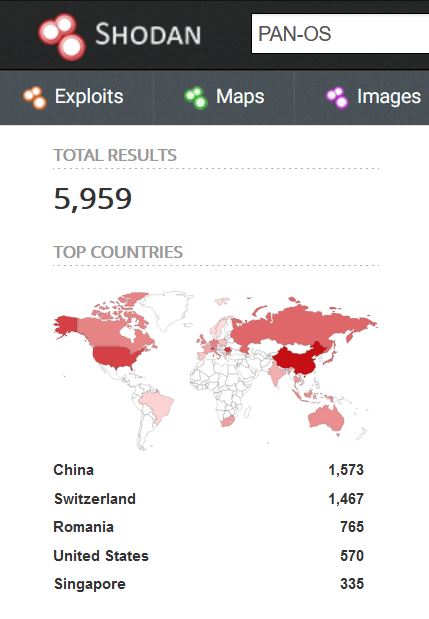
Image Source: Shodan
Affected Products
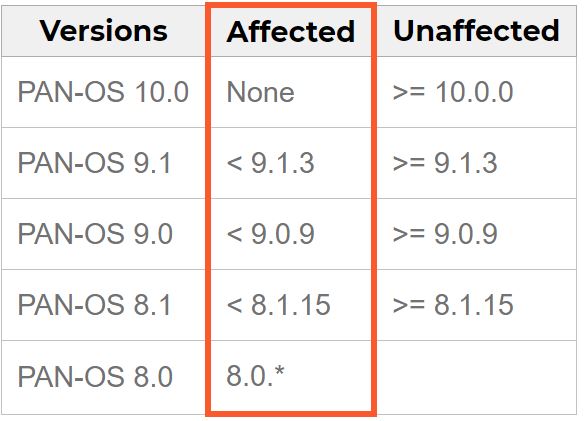
Image Source: Palo Alto
Advisory
https://security.paloaltonetworks.com/CVE-2020-2040
Solution
Users are advised to update their PAN-OS installations to PAN-OS 8.1.15, PAN-OS 9.0.9, PAN-OS 9.1.3, and all later PAN-OS versions. For information, refer to the following article:
Detection
Qualys customers can scan their network with QID 13975 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
https://security.paloaltonetworks.com/
https://security.paloaltonetworks.com/CVE-2020-2040
https://nvd.nist.gov/vuln/detail/CVE-2020-2040
https://cwe.mitre.org/data/definitions/120.html