Overview:
On 19 May 2020, Apache published an advisory to address an insecure deserialization vulnerability in Apache OFBiz. The vulnerability occurs due to Java serialization issues while processing requests sent to the “/webtools/control/xmlrpc” URL. This vulnerability may lead to a variety of attacks like stealing user/admin credentials. This issue can be escalated into a Remote Code Execution.
Description:
This vulnerability exists when Apache OFBiz is configured to use XML-RPC to intercept and convert XML data in the HTTP body send to the “/webtools/control/xmlrpc” URL. The request sent to this URL is handled as follows:
- The request is initially handled by Java class apache.ofbiz.webapp.control.RequestHandler, which determines the mapping for the URL.
- Next, the execute() function is called from the java class apache.ofbiz.webapp.event.XmlRpcEventHandler.
- The parsing of elements in XML-RPC starts by calling the parse() method in the XMLReader class from the getRequest() method apache.ofbiz.webapp.event.XmlRpcEventHandler class.
- The insecure deserialization of the contents of the XML elements happens in the getResult() method of the org.apache.xmlrpc.parser.SerializableParser class.
John Simpson and Dusan Stevanovic, the security researchers from Trend Micro say, “To trigger the vulnerability, an attacker would send an HTTP request containing a crafted serialized object in an XML format to the affected target. The vulnerability is triggered when the server deserializes the XML data.”
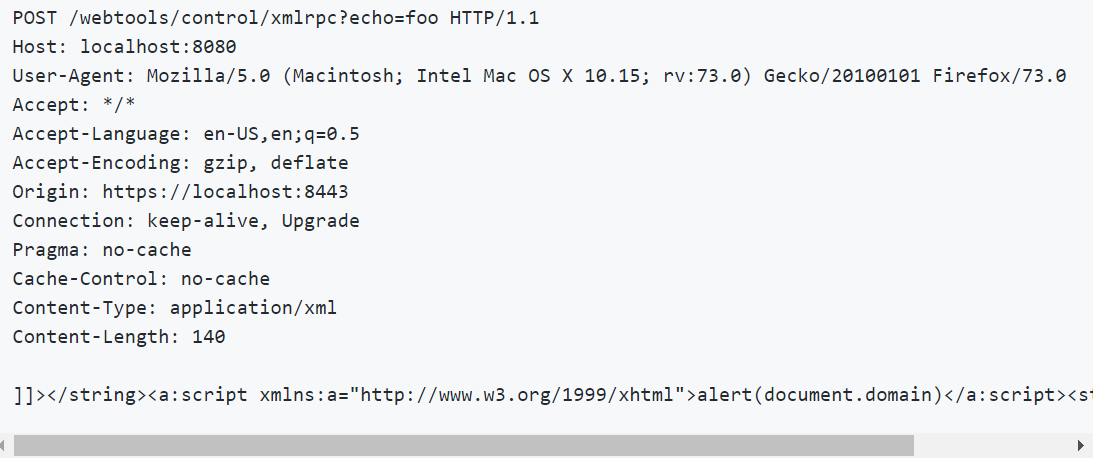
Alvaro Muñoz, the security researcher from the GitHub Security Lab team who discovered the vulnerability, says,”/webtools/control/xmlrpc exposes some unauthenticated services such as ping. We can use this service to reflect arbitrary data and get a Cross-Site Scripting issue.”
Image Source: GitHub Security Lab
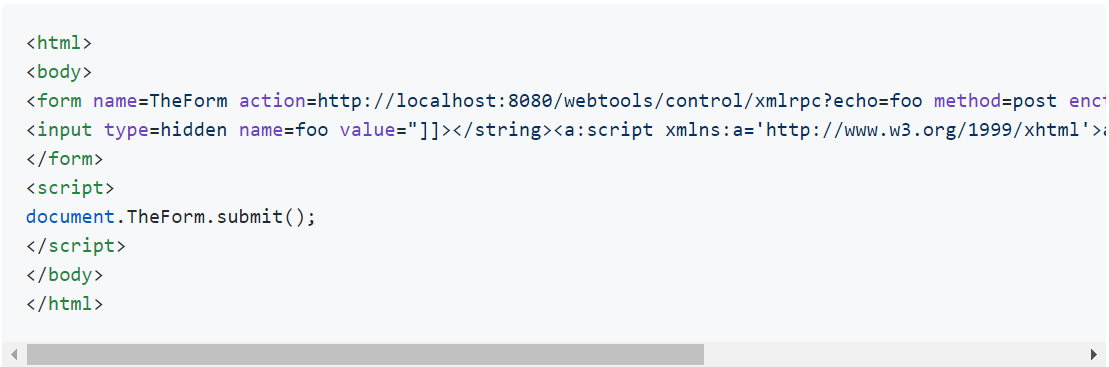
Cross-site scripting issues can be triggered by persuading the victim to visit a malicious page.
Image Source: GitHub Security Lab
Successful exploitation of this vulnerability would allow remote attackers to execute arbitrary code into the affected system.
Remediation
The vulnerability has been fixed in Apache OFBiz version 18.12.01, 17.12.04. Please refer to the recently published Apache advisory for applying patches.