Overview
On 25 September 2020, HP released an advisory to address multiple vulnerabilities (CVE-2020-6925, CVE-2020-6926, and CVE-2020-6927) in the HP Device Manager. Successful exploitation of these vulnerabilities could lead to dictionary attacks, unauthorized remote access to resources, and elevation of privilege.
Description
CVE-2020-6925 – This vulnerability exists due to weak cipher implementation in HP Device Manager. It may allow dictionary attacks against locally managed accounts in HP Device Manager. Customers will not be affected by this vulnerability, if they are using Active Directory authenticated accounts.
CVE-2020-6926 – This is the most severe vulnerability existing in all versions of HP Device Manager. This flaw allows remote unauthenticated attackers to gain access to resources.
CVE-2020-6927 – This is a privilege escalation vulnerability that allows an attacker to gain the SYSTEM privilege of an affected device. Customers will not be affected by this vulnerability, if they are using an external database (Microsoft SQL Server) and have not installed the integrated Postgres service.
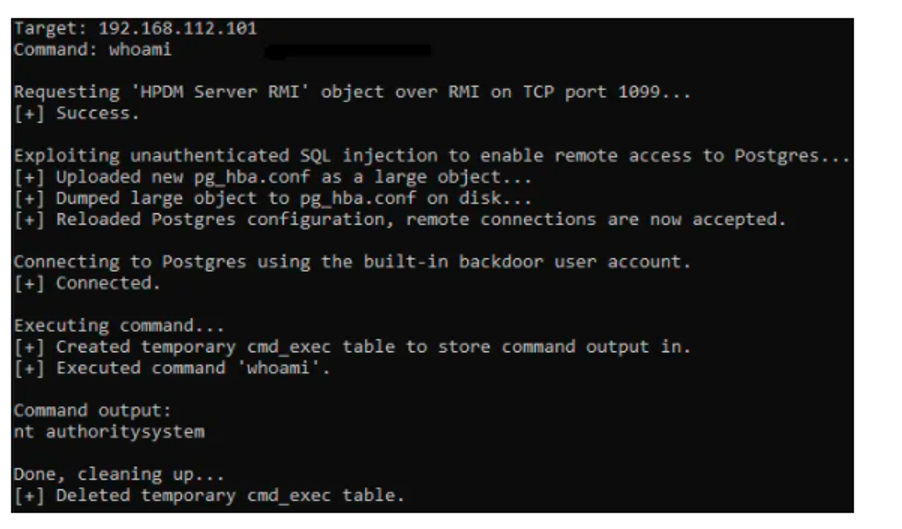
Infosec researcher Nick Bloor, who discovered these vulnerabilities, says in his tweet, “Combined with some other vulnerabilities this leads to unauthenticated remote code execution as SYSTEM”. The researcher has combined two vulnerabilities (CVE-2020-6926, CVE-2020-6927) to gain the SYSTEM level privilege on a remote target.
Image Source: Nick Bloor
| CVE ID | Impacted Version |
| CVE-2020-6925 | All versions of HP Device Manager |
| CVE-2020-6926 | All versions of HP Device Manager |
| CVE-2020-6927 | HP Device Manager 5.0.0 HP Device Manager 5.0.1 HP Device Manager 5.0.2 HP Device Manager 5.0.3 |
Mitigation
HP Device Manager users can partially mitigate this issue in any of the following ways:
- Limit incoming access to Device Manager ports 1099 and 40002 to trusted IPs or localhost only
- Remove the dm_postgres account from the Postgres database; or
- Update the dm_postgres account password within HP Device Manager Configuration Manager; or
- Within the Windows Firewall configuration, create an inbound rule to configure the PostgreSQL listening port (40006) for localhost access only.
| Product | Updated |
| HP Device Manager 5.0 | HP Device Manager 5.0.4 |
| HP Device Manager 4.7 | To be released: HP Device Manager 4.7 Service Pack 13 |
Qualys Detection
Qualys customers can scan their network with QID 373524, 373525 to detect the vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
- https://nickbloor.co.uk/2020/10/05/hp-device-manager-cve-2020-6925-cve-2020-6926-cve-2020-6927/
- https://support.hp.com/us-en/document/c06921908