Overview
On 14th October 2020, Tripwire VERT has published the finding of a stack-based buffer overflow in SonicWall Network Security Appliance (NSA). An unauthenticated HTTP request via a custom protocol handler can exploit this vulnerability. Security researcher Craig Young reported this vulnerability.
Description
A persistent Denial of Service (DoS) condition and potentially arbitrary code execution is possible by sending a crafted HTTP request to the SonicOS firewall. The vulnerability can be exploited without authentication and insecure SSLVPN that is exposed to the public Internet. Below is a quick search on Shodan for potentially affected devices:
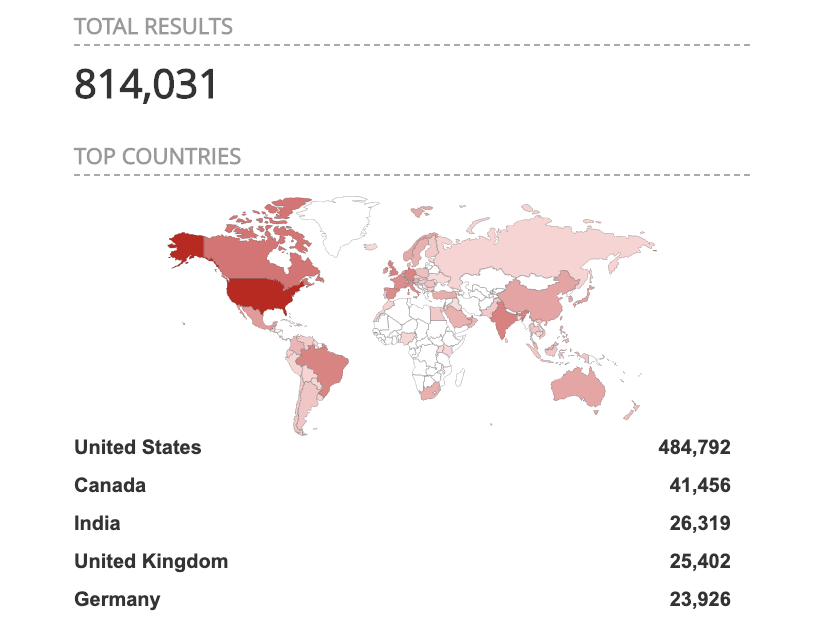
Image Source: Shodan.io
Use of VPN has surged drastically as organizations around the world switched to remote working arrangements in response to the challenge posed by COVID-19. DoS in SonicOS VPN puts organizations and their remote workforce at stake due to this flaw.
See below for a graphical representation of the SonicWall VPN workflow:
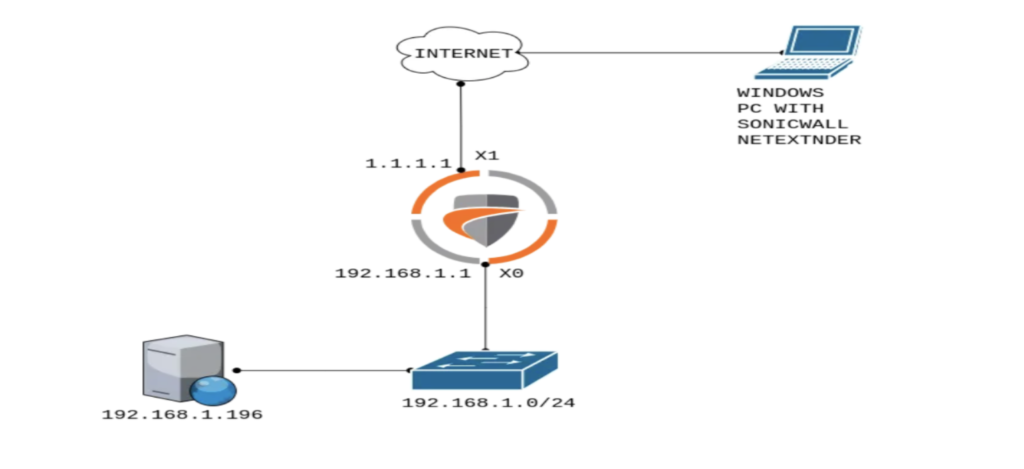
Image Source: SonicWall
Affected Versions:
- SonicOS 6.5.4.7-79n and earlier
- SonicOS 6.5.1.11-4n and earlier
- SonicOS 6.0.5.3-93o and earlier
- SonicOSv 6.5.4.4-44v-21-794 and earlier
- SonicOS 7.0.0.0-1
Remediation & Mitigation
SonicWall has released updates to remediate this flaw. SSL VPN portals may be disconnected from the Internet as temporary mitigation before the patch is applied.
Advisory
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2020-0010
Qualys Detection
Qualys customers can scan their network with QID 13995 to detect the vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://www.tripwire.com/state-of-security/vert/sonicwall-vpn-portal-critical-flaw-cve-2020-5135/
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2020-0010
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-5135