Overview
Recently, Oracle released its critical October update to patch CVE-2020-14882. Oracle WebLogic Server has now observed that attackers can now bypass this patch exposing an unauthenticated Remote Code Execution (RCE) vulnerability (CVE-2020-14750).
As per CVE-2020-14750, unauthorized attackers can continue to bypass the WebLogic background login restrictions and control the server even after WebLogic is patched for CVE-2020-14882. Though there are no publicly available POCs for CVE-2020-14750 yet, it is believed that it can be exploited in a manner similar to CVE-2020-14882. That is, the vulnerability can be exploited by replacing %252E%252E with %252e%252e.
The patch can be bypassed by changing the case of character in a request.
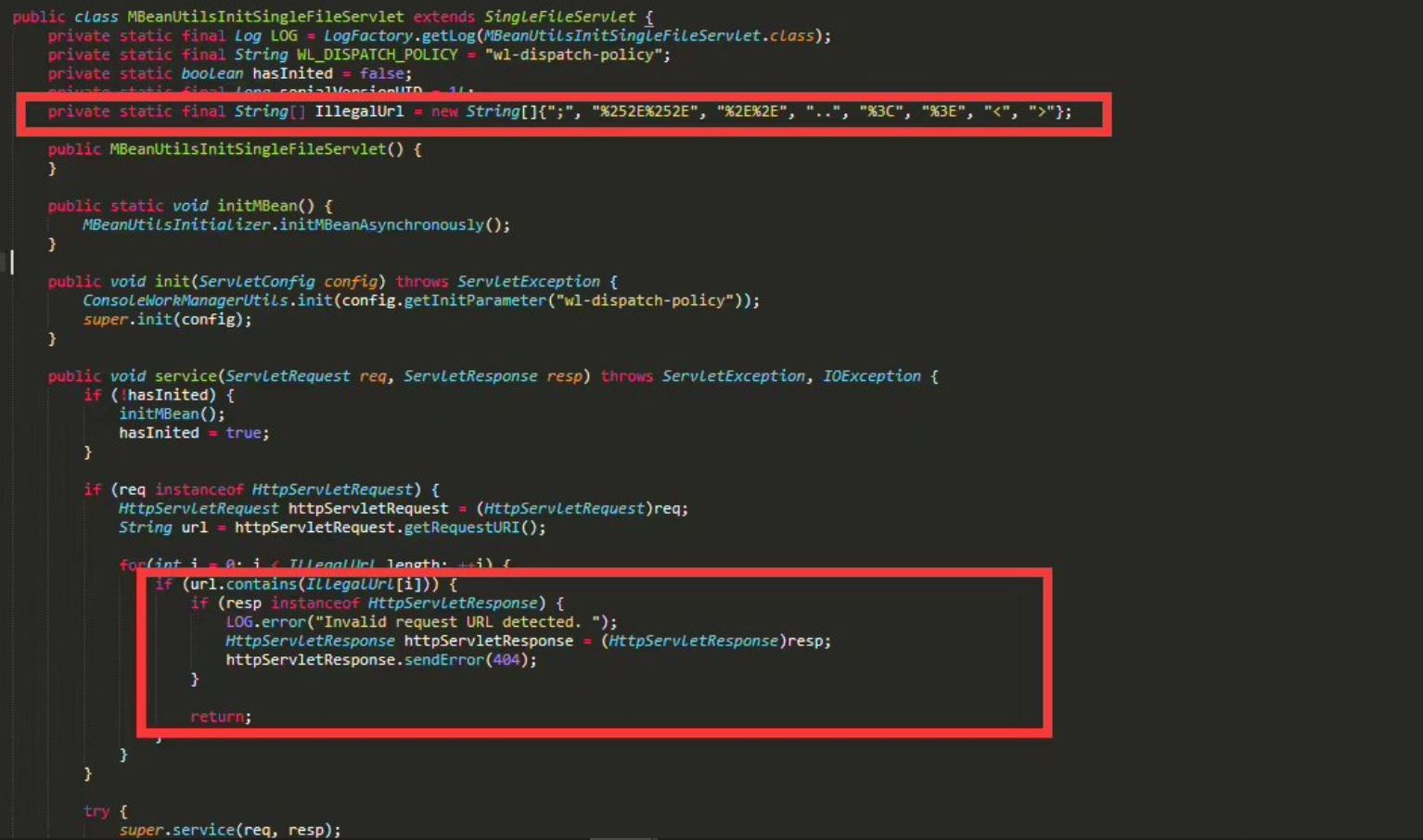
Image Source: chybeta
At Qualys Labs, a POC for CVE-2020-14882 has been already demonstrated – https://threatprotect.qualys.com/2020/10/29/oracle-weblogic-server-remote-code-execution-vulnerability-cve-2020-14882/
Affected WebLogic Versions
Oracle WebLogic Server 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0
Detection
Qualys customers can scan their network with QID# 87433 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References
https://www.oracle.com/security-alerts/cpuoct2020.html
https://www.oracle.com/security-alerts/alert-cve-2020-14750.html
https://threatprotect.qualys.com/2020/10/29/oracle-weblogic-server-remote-code-execution-vulnerability-cve-2020-14882/