Overview
Enterprises and businesses use SD-WAN as a cloud-based networking platform. Situated in different locations, it allows locations and cloud instances to be connected to each other and to company resources. It also applies software control to manage the processes including the orchestration of resources and nodes.
Remote Code Execution (RCE) vulnerabilities (CVE-2020–8271, CVE-2020–827, and CVE-2020–8273) have been observed in Citrix SDWAN Center due to three severe bugs.
Ariel Tempelhof of Realmode Labs in his research has depicted that two bugs need authentication and the other is an unauthenticated RCE with privilege escalation.
Description
According to Realmode Labs, for CVE-2020–8271 – “the /collector/diagnostics/stop_ping endpoint reads the file /tmp/pid_”. Furthermore, “$req_id and uses its contents in a shell_exec call. No sanitization is performed on the user-supplied $req_id which allows path traversal and thereby arbitrary commands. An attacker must be able to communicate with SD-WAN Center’s Management IP/FQDN according to Citrix advisory.
CVE-2020-8272 – ConfigEditor authentication bypass resulting in exposure of SD-WAN functionality. The flaw is in handling URLs in Apache with CakePHP2 framework of Citrix SDWAN. Citrix uses the function “_url in CakeRequest.php“.
For example, a URI of the form “aaaaaaaaaaaaaaaaa/://?/collector/diagnostics/stop_ping” translates to /collector/diagnostics/stop_ping and requires neither client certificate nor authentication, he said. This allows an unauthenticated attacker to access the ConfigEditor functionality.
CVE-2020–8273 – CreateAzureDeployment shell injection issue. To exploit this bug, attackers must be authenticated users on SD-WAN Center. Privilege escalation of an authenticated user to root can be achieved by user-supplied data being JSON encoded and concatenated to an exec call using the code.
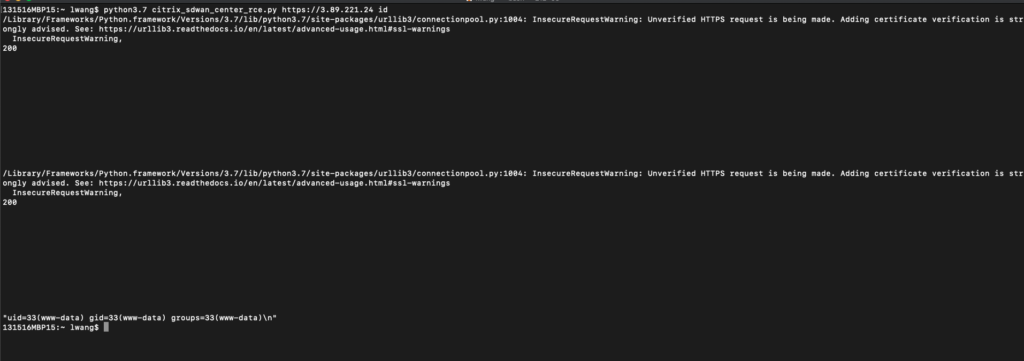
Image Source: Qualys Labs
Affected devices
- Citrix SD-WAN 11.2 prior to version 11.2.2
- Citrix SD-WAN 11.1 prior to version 11.1.2b
- Citrix SD-WAN 10.2 prior to version 10.2.8
Mitigation
Citrix SD-WAN Center is an internal management platform for Citrix SD-WAN and access to Citrix SD-WAN Center is likely to be restricted.
The latest versions of Citrix SD-WAN Center are available at Citrix SD-WAN (NetScaler SD-WAN).
Qualys Detection
Qualys customers can scan their network with QID 13953 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References
https://support.citrix.com/article/CTX285061
https://threatpost.com/citrix-sd-wan-bugs-remote-code-execution/161274/
https://github.com/RealmodeLabs/SD-PWN/blob/master/citrix_sdwan_center_rce.py