In June, Microsoft released a patch for a vulnerability in Windows Kernel (CVE-2020-0986), which was fixed with a patch. However, attackers could still exploit this vulnerability using a different methodology (CVE-2020-17008).
CVE-2020-0986 – Old Vulnerability
An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. This flaw was discovered by Kaspersky along with a bug in Internet explorer.
The vulnerability makes it possible to read and write the arbitrary memory of the splwow64.exe process using interprocess communication and use it to achieve code execution in the splwow64.exe process, bypassing the CFG and EncodePointer protection. It can allow local attackers to elevate the privileges and execute the code in the context of the current user. Attackers would first have to log on to the system, but could subsequently run a specially crafted application to take control of an affected system.
The Microsoft updates released in June address the vulnerability by correcting how the Windows kernel handles objects in memory.
Now, Maddie Stone, researcher at Google Project Zero, has disclosed that the fix was faulty. According to her,
“The original issue was an arbitrary pointer dereference, which allowed the attacker to control the src and dest pointers to a memcpy. The ‘fix’ simply changed the pointers to offsets, which still allows control of the args to the memcpy.”
In a recently published technical report, she explains how to trigger the vulnerability, now identified as CVE-2020-17008.
CVE-2020-17008 – New Vulnerability
According to the report,
A low integrity process can send LPC messages to splwow64.exe (Medium integrity) and gain a write-what-where primitive in splwow64’s memory space. The attacker controls the destination, the contents that are copied, and the number of bytes copied through a memcpy call. The offset for the destination pointer calculation is only constrained to be:
Offset <= 0x7FFFFFFF
Offset + perceived size of structure <= 0x7FFFFFFFSplwow64 passes the LPC message to GdiPrinterThunk. The vulnerable memcpy is in message 0x6D.
The only difference between CVE-2020-0986 is that for CVE-2020-0986 the attacker sent a pointer and now the attacker sends an offset.
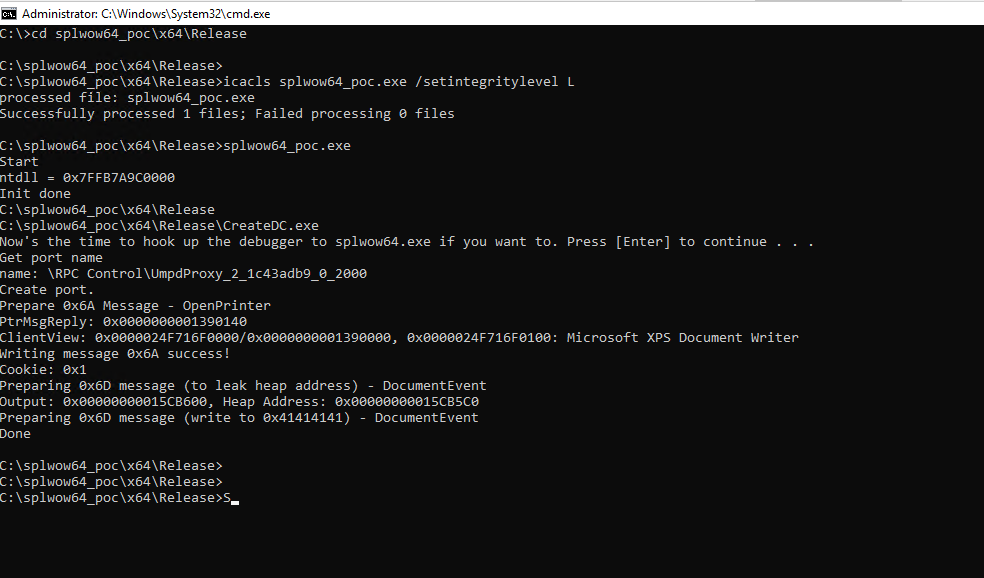
PoC
Researcher also published a proof-of-concept code for CVE-2020-17008 adapted from the original one from Kaspersky for CVE-2020-0986, along with instructions on how to run it properly. It triggers the memcpy vulnerability twice: first to leak the heap address where the message is stored and what the offset is added to generate the pointers, and then to do the write-what-where.
Affected Versions
- Windows 10 version 1607 (for x64-based systems)
- Windows 10 version 1607 for 32-bit systems
- Windows 10 (for x64-based systems)
- Windows 10 (for 32-bit systems)
- Windows 10 version 1709 (for ARM64-based systems)
- Windows 10 version 1709 (for x64-based systems)
- Windows 10 version 1709 for 32-bit systems
- Windows 10 version 1809 (for ARM64-based systems)
- Windows 10 version 1809 (for x64-based systems)
- Windows 10 version 1809 for 32-bit systems
- Windows Server version 1803 (Server Core installation)
- Windows 10 version 1803 (for ARM64-based systems)
- Windows 10 version 1803 (for x64-based systems)
- Windows 10 version 1803 for 32-bit systems
- Windows Server version 1903 (Server Core installation)
- Windows 10 version 1903 (for ARM64-based systems)
- Windows 10 version 1903 (for x64-based systems)
- Windows 10 version 1903 for 32-bit systems
- Windows Server version 1909 (Server Core installation)
- Windows 10 version 1909 (for ARM64-based systems)
- Windows 10 version 1909 (for x64-based systems)
- Windows 10 version 1909 for 32-bit systems
- Windows Server 2004 version (Server Core installation)
- Windows 10 version 2004 (for x64-based systems)
- Windows 10 version 2004 (for ARM64-based systems)
- Windows 10 version 2004 (for 32-bit systems)
- Windows Server 2016 (Server Core installation)
- Windows Server 2016
- Windows Server 2019 (Server Core installation)
- Windows Server 2019
- Windows Server 2012
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 (Server Core installation)
- Windows RT 8.1
- Windows 8.1 (for x64-based systems)
- Windows 8.1 (for 32-bit systems)
Patch Version
No patch has been released till now.
Detection
Qualys customers can scan their network with QID # 91709 to detect vulnerable assets.
Please continue to follow on Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://bugs.chromium.org/p/project-zero/issues/detail?id=2096
https://github.com/jas502n/CVE-2020-17008/blob/main/README.md#%E5%BD%B1%E5%93%8D%E7%89%88%E6%9C%AC
https://godecrypt.com/news/security/windows-zero-day-with-bad-patch-gets-new-public-exploit-code/