Three critical vulnerabilities were observed in SolarWinds products. All these severe bugs allow remote code execution with high privileges. At the time of this blog being published, there has been no active PoC in the wild.
CVE-2021-25274 – MSMQ Remote Code Execution
SolarWinds Collector Service uses MSMQ (Microsoft Message Queue), and it doesn’t set permissions on its private queues. As a result, remote unauthenticated clients can send messages that are processed by the Collector Service. Additionally, upon processing such messages, the service deserializes them in an insecure manner, allowing remote arbitrary code execution as LocalSystem.
SolarWinds Orion Collector uses MSMQ heavily, which contains is a huge list of private queues, and literally, every one of them has a specific problem such as security misconfiguration. According to Trustwave, a simple PoC, which will be tentatively released on February 9, allows remote code execution by unprivileged users through combining those two issues.
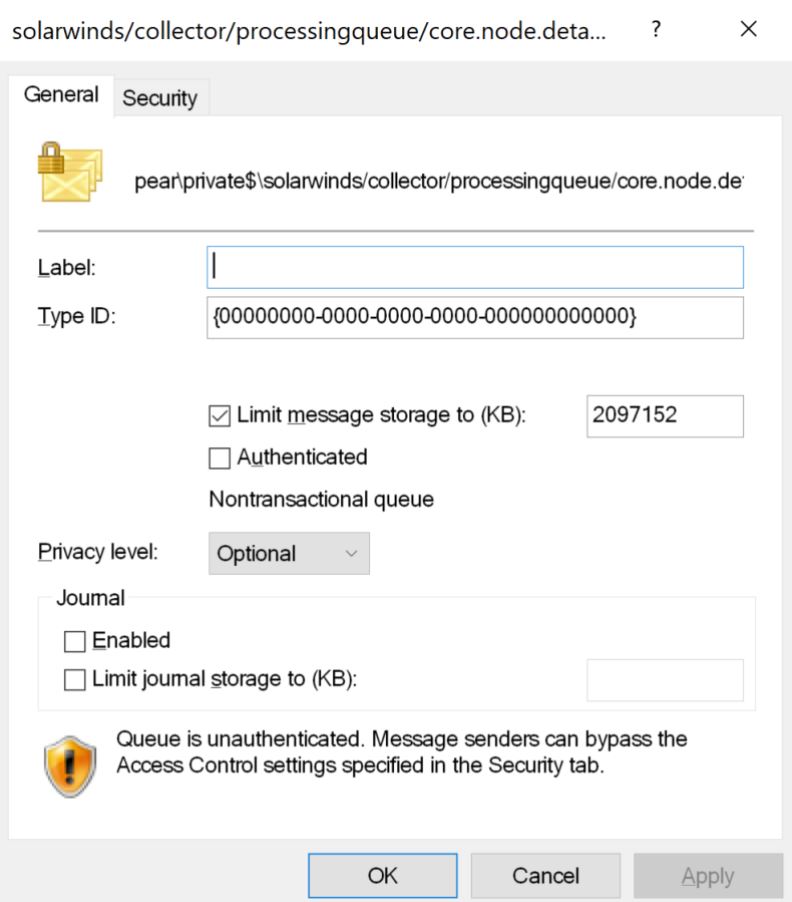
Image Source: Trustwave
CVE-2021-25275 – Unprivileged users can get DBO owner Access
Several SolarWinds products install and use SQL Server backend (Orion) and store database credentials to access backend in a file readable by unprivileged users. As a result, any user having access to the file system can read Orion database login details from that file, including the encrypted password, which can easily be decrypted after gaining access. The credentials can be used to get database owner access to the Orion database. This gives access to the data collected by SolarWinds applications and Admin-level access to the applications, via insert/change of authentication data stored in the Accounts table of the database.
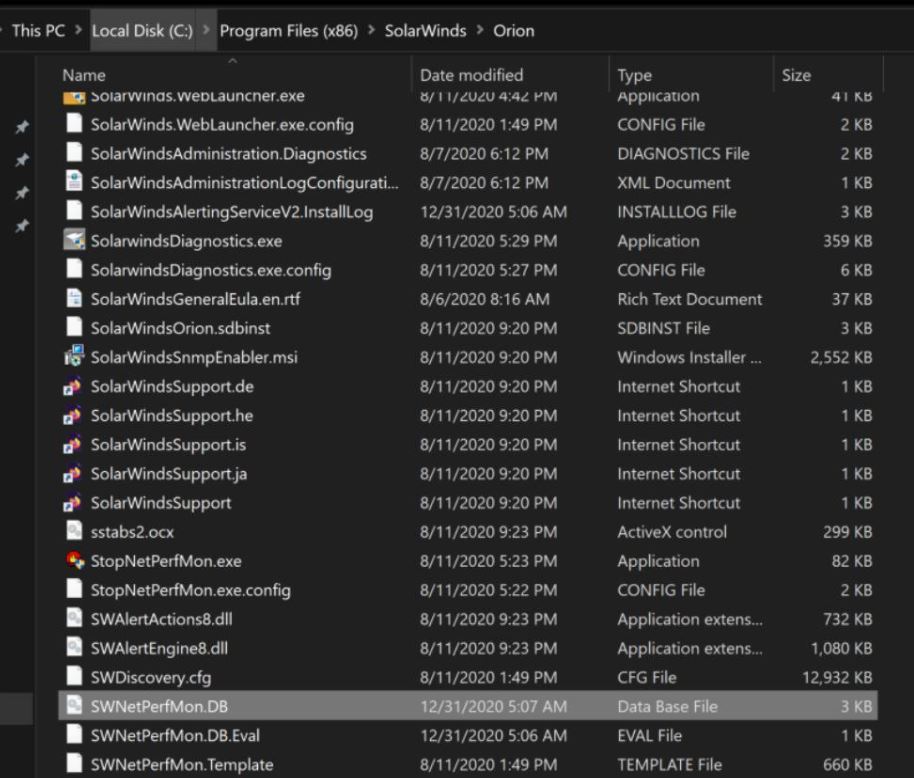
Configuration file with Orion backend database credentials.
Image Source: Trustwave
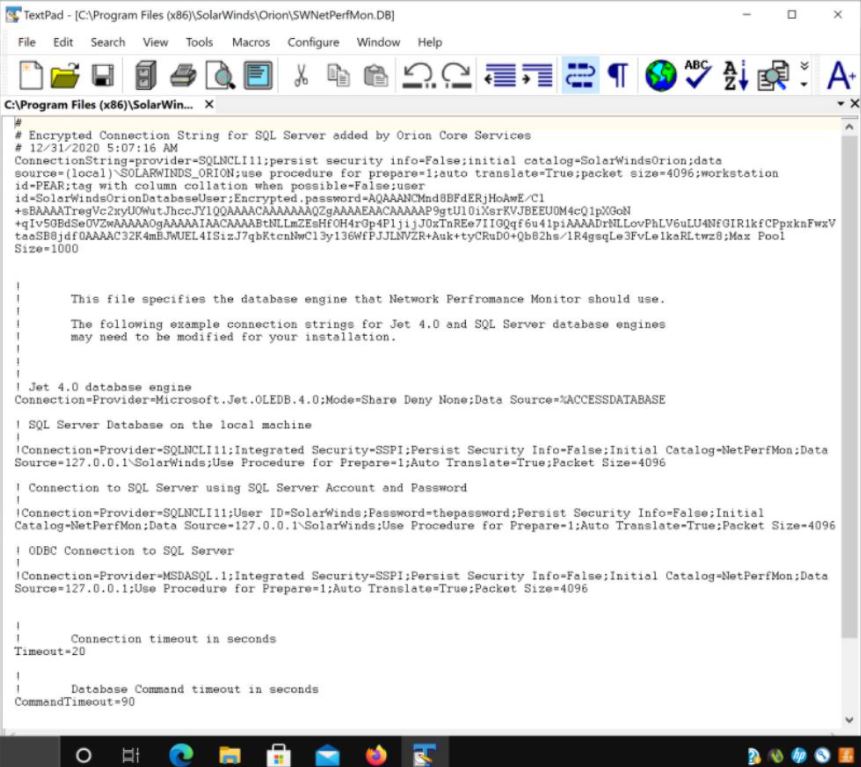
Inside the configuration file are database credentials for the Orion backend database
Image Source: Trustwave
CVE-2021-25276 – Privilege escalation locally or via RDP in Serv-U FTP
The directory (%ProgramData%\RhinoSoft\Serv-U\Users\<DOMAIN>\) is globally readable and writeable. This directory contains user profile files (bearing .Archive extension) that among other user properties store the user’s password hash.
Since one can create any Serv-U FTP user, it makes sense to define an Admin account by setting a simple field in the file and then set the home directory to the root of C:\ drive. Now, one can log in via FTP and read or replace any file on the C:\ since the FTP server runs as LocalSystem.
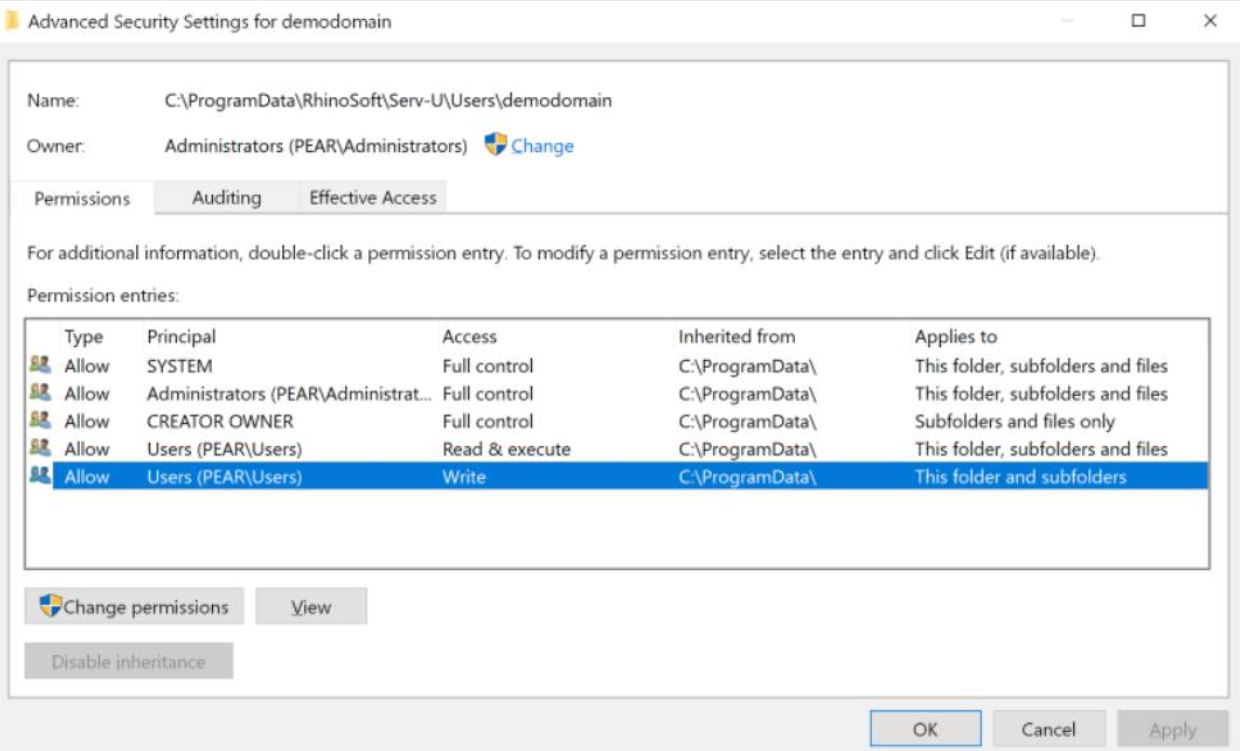
Authenticated users can write to the configuration directory.
Image Source: Trustwave
All these vulnerabilities have the potential of completely compromising the Windows servers.
Affected Products
SolarWinds Orion Platform 2020.2.1 and prior
SolarWinds Serv-U FTP Server 15.2.1 on Windows
Solution
SolarWinds has released patches for its Orion-based and Serv-U FTP products to address these vulnerabilities.
Detection
Qualys customers can scan their network with QID(s) 375081 and 27391 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://thehackernews.com/2021/02/3-new-severe-security-vulnerabilities.html
https://www.zdnet.com/article/solarwinds-patches-three-newly-discovered-software-vulnerabilities/
https://downloads.solarwinds.com/solarwinds/Release/HotFix/Serv-U-15.2.2-Hotfix-1.zip
https://nvd.nist.gov/vuln/detail/CVE-2021-25274