SonicWall is one of the latest IT security vendors, after Microsoft, FireEye, and Malwarebytes, to confirm a breach in recent weeks. All vendors disclosed cyberattacks related to the massive SolarWinds attack campaign targeting major US government agencies and businesses. SonicWall has issued a security advisory addressing a patch for the zero-day vulnerability used in attacks against the SMA 100 series of remote access appliances.
In a statement published on January 22, SonicWall officials disclosed that they detected an attack “by highly sophisticated threat actors exploiting probable zero-day vulnerabilities on certain SonicWall secure remote access products”. On February 1, SonicWall confirmed a zero-day vulnerability on SMA 100 series 10.x code.
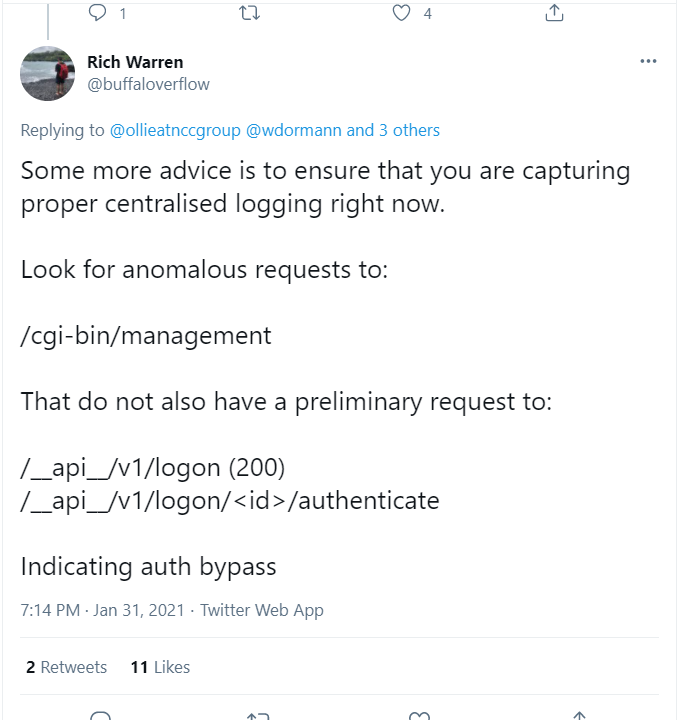
SonicWall has not disclosed any details on the vulnerability; however, it can be assumed from tweets from NCC Group’s Ollie Whitehouse and Rich Warren that it allows remote access to the management interface without authorization, leading to auth bypass vulnerability.
Affected Products:
- SonicWall SMA 100 Series
- SonicWall Virtual Appliances: SMA 500v
- SonicWall Physical Appliances: SMA 200, SMA 210, SMA 400, SMA 410
Mitigation:
SonicWall has published an official advisory to address this actively exploited zero-day vulnerability in SMA 100 series with the latest firmware version 10.2.0.5-29sv tracked under the SNWLID-2021-0001. All SMA 100 series users are recommended to apply this patch Immediately to avoid potential exploitation. Instructions on updating the SMA 100 10.x series firmware can be found here for physical appliances and this article for virtual devices.
The recommended update procedure for all customers requires you to:
- Upgrade to SMA 10.2.0.5-29sv firmware, available on www.mysonicwall.com.
- Reset the passwords for any users who may have logged in to the device via the web interface.
- Enable multifactor authentication (MFA).
Administrators/users who cannot immediately apply this patch should enable the Web Application Firewall (WAF) until they are ready to deploy the patch on affected devices.
Detection:
Qualys customers can scan their network with QID 10369 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References and Sources
- https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0001
- https://www.sonicwall.com/blog/2021/01/security-notice-update-on-sma-100-series-product-investigation/
- https://www.sonicwall.com/support/knowledge-base/smb-ssl-vpn-upgrading-firmware-on-sma-500v-virtual-appliance/170502851052498/
- https://www.sonicwall.com/support/knowledge-base/how-to-upgrade-firmware-on-sma-100-series-appliances/170502339501169/