On the second Patch Tuesday of 2021, Microsoft published advisories to address 56 new security vulnerabilities. Of these, nine were rated as critical and one is actively exploited in the wild.
Elevation of Privileges in Windows Kernel (CVE-2021-1732)
This bug is in the Windows Win32k operating system kernel. It allows a logged-in user to execute code with higher privileges by running a specially crafted application. Successful exploitation of this vulnerability could allow attackers to execute in the context of the kernel and gain SYSTEM privileges.
Microsoft is aware that CVE-2021-1732 is actively being exploited in the wild. However, severity of this bug is ‘Important’ because it allows attackers to increase their authority and control on a device, which means the attackers needs to already have access to the target system. Even though CVE-2021-1732 is actively being exploited in the wild, this bug is classified as “Important” and not “Critical” because, while it allows attackers to increase their authority and control on a device, attackers need to have prior access to the target system.
Vulnerability Details
DBAPPSecurity researchers published a blog post with the root cause and exploit details of CVE-2021-1732. Researchers said “an advanced persistent threat hacker group called Bitter was exploiting the vulnerability in “a very limited number of attacks” against targets in China. The attackers could use it to escape the security sandbox when targets were using either Internet Explorer or Adobe Reader.”
In win32kfull!xxxCreateWindowEx, it calls the user32!_xxxClientAllocWindowClassExtraBytes callback function to allocate memory of WndExtra by default. The return value of the callback is saved to a kernel struct member (the WndExtra member).
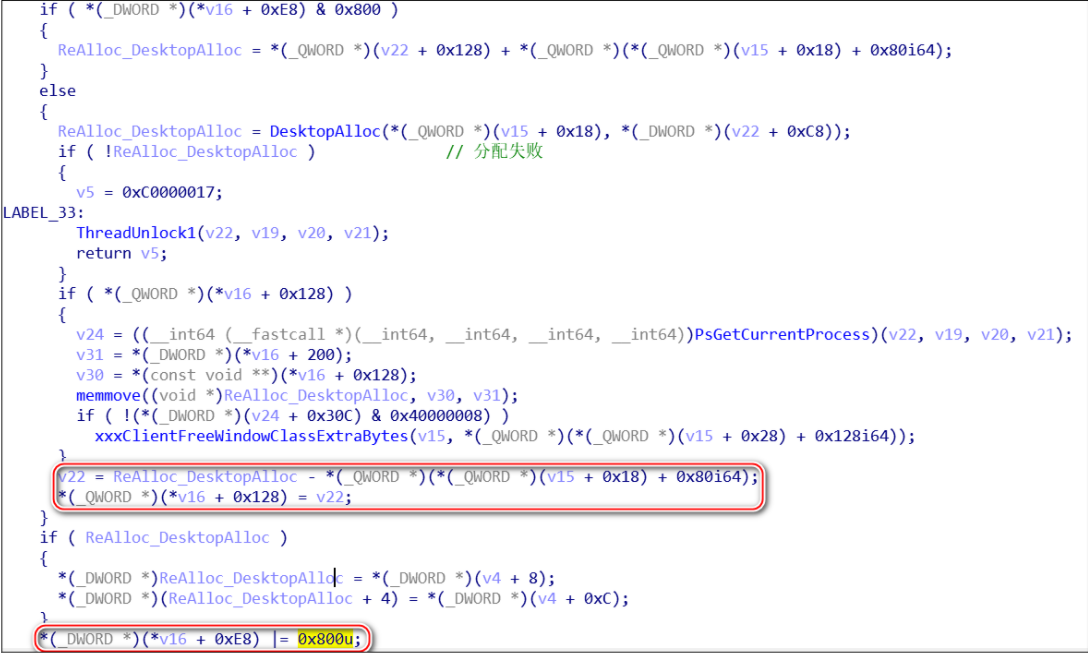
The PoC triggers a blue screen of death when calling DestoryWindow. The win32kfull!xxxFreeWindow function checks the flag above and if it has been set, xxxFreeWindow will call RtlFreeHeap to free the WndExtra area; if not, xxxFreeWindow will call xxxClientFreeWindowClassExtraBytes to free the WndExtra area.
In the PoC, we return a user mode heap address. The address overwrites the origin offset to a user mode heap address (fake_offset). This causes win32kfull!xxxFreeWindow to trigger an out-of-bound access when using RtlFreeHeap to release a kernel heap.
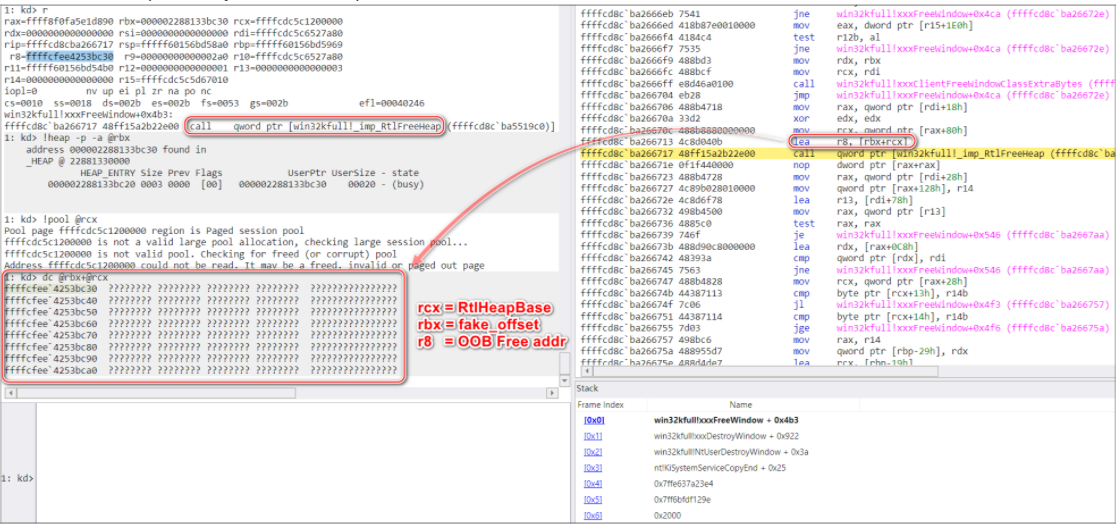
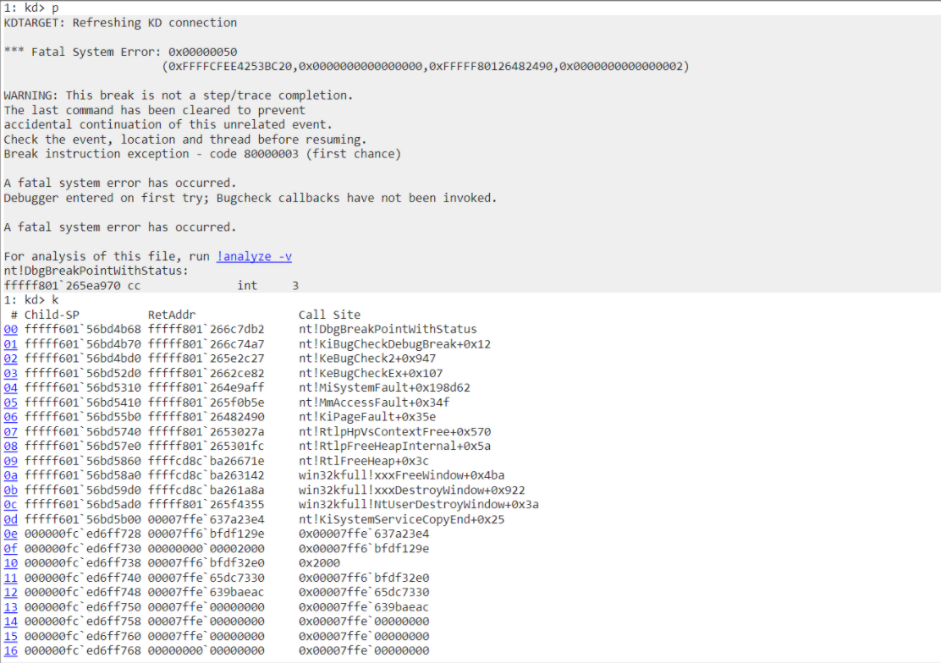
If we call the RtlFreeHeap here, it will trigger a Blue screen of death.
Affected versions
- Windows Server, version 20H2 (Server Core Installation)
- Windows 10 Version 20H2 for ARM64-based Systems
- Windows 10 Version 20H2 for 32-bit Systems
- Windows 10 Version 20H2 for x64-based Systems
- Windows Server, version 2004 (Server Core installation)
- Windows 10 Version 2004 for x64-based Systems
- Windows 10 Version 2004 for ARM64-based Systems
- Windows 10 Version 2004 for 32-bit Systems
- Windows Server, version 1909 (Server Core installation)
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows Server 2019 (Server Core installation)
- Windows Server 2019 Windows 10 Version 1809 for ARM64-based Systems
- Windows 10 Version 1809 for x64-based Systems
- Windows 10 Version 1809 for 32-bit Systems
- Windows 10 Version 1803 for ARM64-based Systems
- Windows 10 Version 1803 for x64-based Systems
- Windows 10 Version 1803 for 32-bit Systems
Remediation
Please refer Microsoft’s Advisories for Patch version details.
Detection
Qualys customers can scan their network with QID 91741 to detect vulnerable assets.
Please continue to follow on Qualys Threat Protection for more coverage on the latest vulnerabilities.
References and Sources
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1732