On 25th May 2021, VMware released a security advisory to address two vulnerabilities (CVE-2021-21986, CVE-2021-21985) for vCenter Server. Successful exploitation of these vulnerabilities could allow a remote attacker to execute arbitrary code on the vulnerable system.
VMware has assigned critical severity for CVE-2021-21985 with a maximum CVSSv3 base score of 9.8. The severity of CVE-2021-21986 has been evaluated as “moderate” with a maximum CVSSv3 base score of 6.5.
VMware urges customers to immediately patch these critical vulnerabilities.
Vulnerability Details
CVE-2021-21985:
This RCE vulnerability occurred due to improper input validation in the Virtual SAN Health Check plug-in, which is enabled by default in vCenter Server. An attacker having network access to port 443 could exploit this bug to execute arbitrary commands on the vulnerable system.
Affected Product Versions, Patched Versions and Workarounds:
| Product | Version | Running On | CVSSv3 | Severity | Fixed Versions | Workaround |
| vCenter Server | 7.0 | Any | 9.8 | Critical | 7.0 U2b | KB83829 |
| vCenter Server | 6.7 | Any | 9.8 | Critical | 6.7 U3n | KB83829 |
| vCenter Server | 6.5 | Any | 9.8 | Critical | 6.5 U3p | KB83829 |
| Cloud Foundation (vCenter Server) | 4.x | Any | 9.8 | Critical | 4.2.1 | KB83829 |
| Cloud Foundation (vCenter Server) | 3.x | Any | 9.8 | Critical | 3.10.2.1 | KB83829 |
CVE-2021-21986:
This vulnerability was found in the vSphere authentication mechanism of vCenter Server plug-ins (Virtual SAN Health Check, Site Recovery, vSphere Lifecycle Manager, and VMware Cloud Director Availability). An attacker having network access to port 443 could exploit this bug to perform actions allowed by the impacted plug-ins without authentication.
Affected Product Versions, Patched Versions and Workarounds:
| Product | Version | Running On | CVSSv3 | Severity | Fixed Version | Workaround |
| vCenter Server | 7.0 | Any | 6.5 | Moderate | 7.0 U2b | KB83829 |
| vCenter Server | 6.7 | Any | 6.5 | Moderate | 6.7 U3n | KB83829 |
| vCenter Server | 6.5 | Any | 6.5 | Moderate | 6.5 U3p | KB83829 |
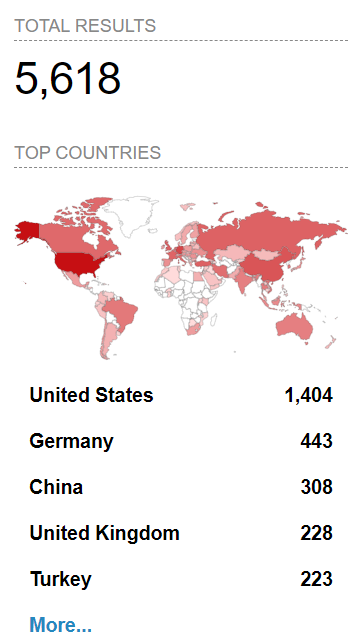
On Shodan, we observed more than 5000 publicly available devices on the internet that may be vulnerable.
Image Source: Shodan
Detection
Qualys customers can scan their network with QIDs 216259, 216260, 216261 to detect vulnerable assets.
Kindly continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
Workaround
Affected plugins must be set to “incompatible.” Disabling a plugin from within the UI does not prevent exploitation.
To check how to disable affected plugin refer workaround provided by VMware.
Workaround Detection
Qualys Policy Compliance customers can evaluate workaround on vCenter Linux-based virtual appliances by following controls:
21522 Status of the VMware Cloud Director Availability Plugin
21521 Status of the VMware vSphere Life-cycle Manager
21520 Status of the VMware Site Recovery Plugin
21519 Status of the VMware vSAN H5 Client Plugin
21464 Status of the VMware vRops Client Plugin
Note:
Customer should create Unix authentication record with target type “VMWare vCenter Server (Policy Compliance)”
References