Tracked as CVE-2021-20019, a vulnerability was observed in SonicOS where the HTTP server response leaks partial memory by sending a crafted unauthenticated HTTP request. This can potentially lead to an internal sensitive data disclosure vulnerability. The shortcoming was rectified in an update rolled out to SonicOS on June 22. However, there is no evidence that the flaw is being exploited in the wild.
The unsuccessful fix turned into a flaw, identified as CVE-2020-5135 with a CVSS score of 9.4, concerned a buffer overflow vulnerability in SonicOS that could allow a remote attacker to cause denial-of-service (DoS) and potentially execute arbitrary code by sending a malicious request to the firewall.
Craig Young, the security researcher who identified this vulnerability tried to show in a blog post, the values in the binary data which certainly look like they could be memory addresses. Discovery of a Memory dump shown below.
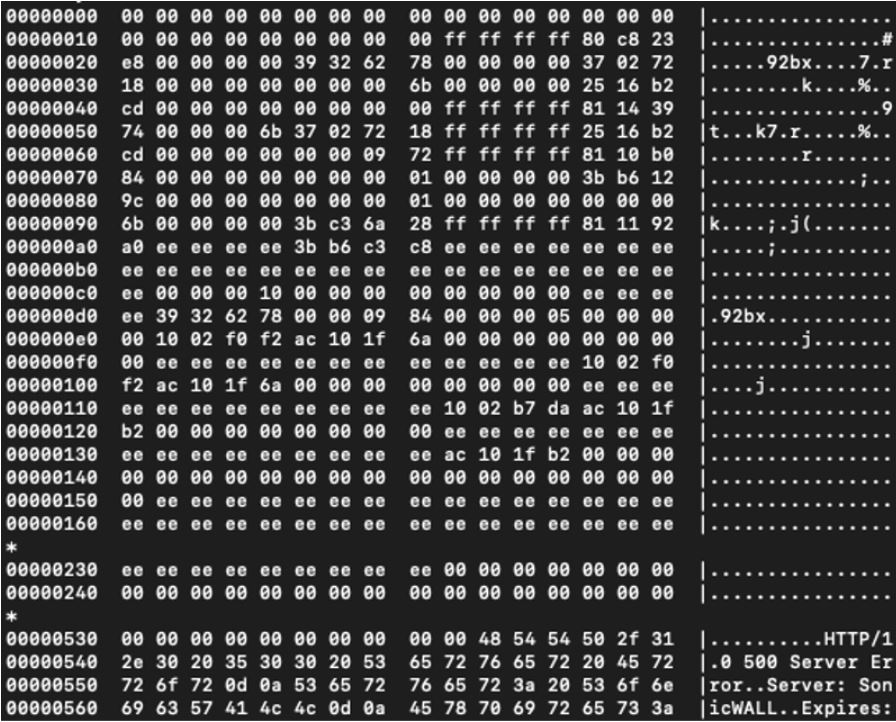
Image Source: Tripwire
Affected products
- SonicOS – 6.5.4.7-83n
- SonicOSv – 6.5.4.4-44v-21-955
- SonicOS – 6.5.1.12-3n
- SonicOS – 6.0.5.3-94o
- SonicOS – 7.0.0-R713 and earlier,
- SonicOS – 7.0.1-R1036 and earlier
- and below SonicOS – 7.0.0.376
Mitigation
SonicWall strongly advises customers apply the respective SonicOS patch immediately. After reviewing this security advisory, please go to MySonicWall and download the appropriate SonicOS patch.
Qualys Detection
Qualys customers can scan their network with QID 730122 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0006
https://thehackernews.com/2021/06/sonicwall-left-vpn-flaw-partially.html
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2020-0010