Dell Technologies published an advisory on June 24, 2021 notifying customers of a set of vulnerabilities that can be combined to impersonate Dell.com and take control of the target devices’ boot process to break OS-level security controls. The vulnerabilities affect a wide range of Dell systems. Dell recommends that all customers update to the latest Dell Client BIOS version as soon as possible or apply mitigations if they cannot update.
To help address these issues, Qualys has released a QID to detect vulnerable assets.
About Dell Client Platform BIOSConnect and HTTPS Boot Multiple Vulnerabilities
On June 24, 2021, Dell published an advisory notifying about the Dell Client Platform Security Update for multiple vulnerabilities in the BIOSConnect and HTTPS Boot features as part of the Dell Client BIOS – DSA-2021-106. This patch addresses multiple CVEs – CVE-2021-21571, CVE-2021-21572, CVE-2021-21573, CVE-2021-21574. According to Dell’s website, the SupportAssist software is “preinstalled on most Dell devices running Windows Operating System,” while BIOSConnect provides remote firmware update and OS recovery features.
CVE-2021-21572, CVE-2021-21573, CVE-2021-21574
Dell BIOSConnect feature contains a buffer overflow vulnerability. An authenticated malicious Admin user with local access to the system may potentially exploit this vulnerability to run arbitrary code and bypass UEFI restrictions.
CVE-2021-21571
Dell UEFI BIOS https stack, leveraged by the Dell BIOSConnect and Dell HTTPS Boot features, contains an improper certificate validation vulnerability. A remote unauthenticated attacker may exploit this vulnerability using a person-in-the-middle attack, which may lead to a denial of service and payload tampering.
All these CVEs can be combined to form a chain of attack as shown below:
CVE-2021-21571 + (CVE-2021-21572 || CVE-2021-21573 || CVE-2021-21574) = RCE at the BIOS level via MITM attack.
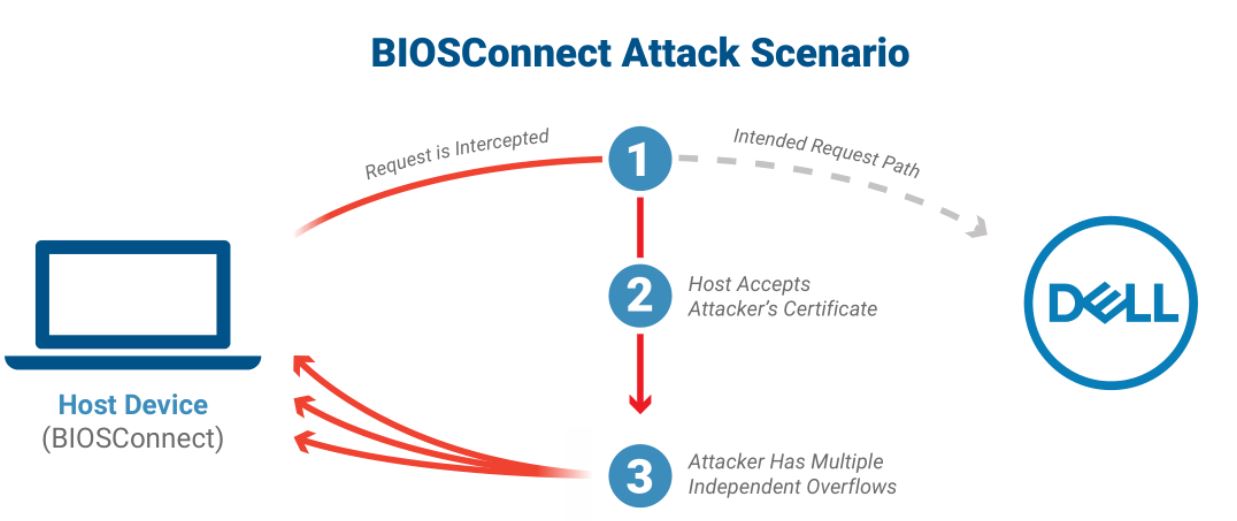
Image Source: Eclypsium
The chain of flaws, discovered by Eclypsium researchers, enables privileged remote attackers to impersonate Dell.com and take control of the target device’s boot process to break OS-level security controls.
According to Eclypsium, users will have to update the system BIOS/UEFI for all affected systems. The researchers also recommend using an alternate method other than the SupportAssist’s BIOSConnect feature to apply BIOS updates on their devices. “Successfully compromising the BIOS of a device would give an attacker a high degree of control over a device,” the Eclypsium researchers said. “The attacker could control the process of loading the host operating system and disable protections to remain undetected. This would allow an attacker to establish ongoing persistence while controlling the highest privileges on the device.”
Affected Products
Dell – Alienware m15 R6, Inspiron, OptiPlex, Latitude, Vostro, XPS
Mitigation
In all, the flaws affect 128 Dell models spanning consumer and business laptops, desktops, and tablets, an estimated 30 million individual devices in total. The weaknesses also impact computers that have Secure Boot enabled, a security feature designed to prevent rootkits from being installed at boot time in memory.
Additionally, the PC maker has published workarounds to disable both the BIOSConnect and HTTPS Boot features for customers who are unable to apply the patches immediately.
Dell recommends that all customers update to the latest Dell Client BIOS version as soon as possible. Customers who choose not to apply BIOS updates immediately or who are otherwise unable to do so at this time should apply the below mitigation.
- BIOSConnect:
Customers may disable the BIOSConnect feature using one of two options:
Option 1: Customers may disable BIOSConnect from the BIOS setup page (F2).
Note: Customers may find the BIOSConnect option under different BIOS setup menu interfaces depending on their platform model. These are referred below as BIOS Setup Menu Type A and BIOS Setup Menu Type B.
BIOS Setup Menu Type A: F2-> Update,Recovery -> BIOSConnect -> Switch to Off
BIOS Setup Menu Type B: F2 -> Settings -> SupportAssist System Resolution -> BIOSConnect -> Uncheck BIOSConnect option
Note: Dell recommends customers not to run “BIOS Flash Update – Remote” from F12 until the system is updated with a remediated version of the BIOS.
Option 2: Customers may leverage Dell Command | Configure (DCC)’s Remote System Management tool to disable the BIOSConnect and Firmware Over the Air (FOTA) BIOS settings.
- HTTPS Boot
Customers may disable the HTTPS Boot feature using one of two options:
Option 1: Customers may disable BIOSConnect from the BIOS setup page (F2).
F2-> Connection -> HTTP(s) Boot -> Switch to Off
BIOS Setup Menu Type B: F2 -> Settings -> SupportAssist System Resolution -> BIOSConnect -> Uncheck BIOSConnect option
Option 2: Customers may leverage Dell Command | Configure (DCC)’s Remote System Management tool to disable HTTP Boot Support.
Qualys Detection
Qualys customers can scan their network with QID 375659 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://eclypsium.com/2021/06/24/biosdisconnect/
https://thehackernews.com/2021/06/bios-disconnect-new-high-severity-flaws.html