According to Microsoft Security Bulletin published on March 09, 2021, seven vulnerabilities concerning Microsoft’s DNS server were corrected. These vulnerabilities, identified as CVE-2021-26877, CVE-2021-26897, CVE-2021-26893, CVE-2021-26894 and CVE-2021-26895, are considered critical. Among these, two allow a denial of service, while the five others allow an execution of remote arbitrary code.
By default, DNS servers are installed on the Active Directory Domain Controllers. This characteristic makes the vulnerabilities particularly critical since their exploitation would allow an attacker to take control of the Active Directory domain.
The DNS mechanism is configured differently depending on the installations:
- When the DNS zone is integrated with Active Directory, secure mode is enabled by default.
- When the DNS zone is not integrated with Active Directory but stored locally on the DNS server, the Dynamic Zone Update mechanism is not enabled by default. If enabled, it is available in non-secure mode (not recommended).
The following table summarizes DNS Dynamic Update deployment models relative to the opportunity these RCE vulnerabilities present.
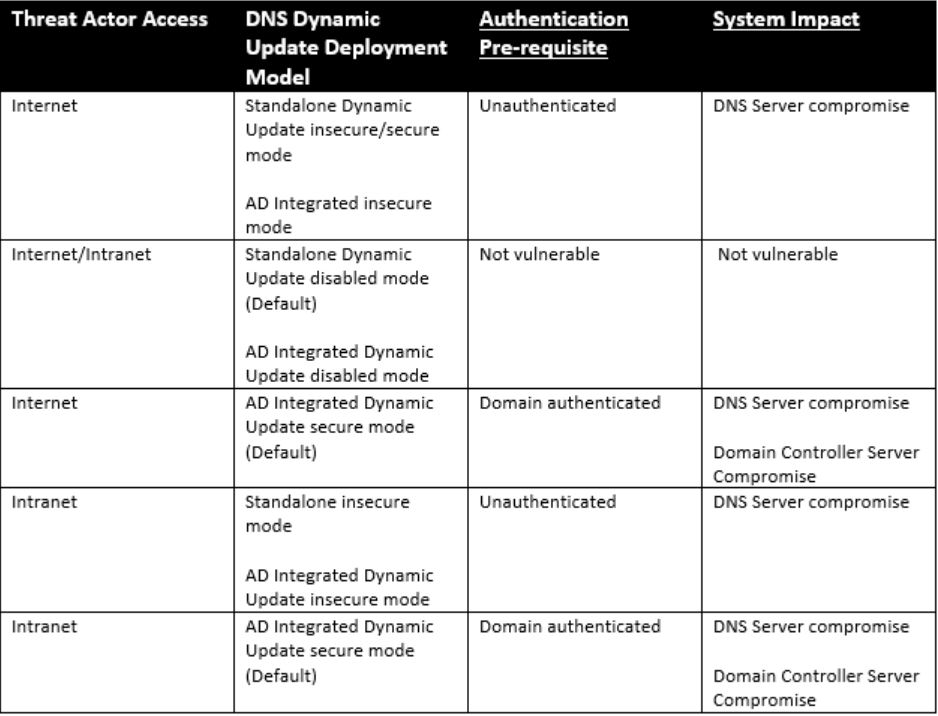
Image Source: McAfee
CVE-2021-26897 is a buffer overflow issue, wherein a series of oversized “dynamic update” DNS queries with SIG (signature) records cause writing beyond the buffer boundary when these records are saved to file. DNS server periodically saves all received updates to file (so they are not lost upon restart or crash), and the issue gets triggered by simply waiting for this file write to happen after sending several requests, or by stopping the DNS Server service.
The vulnerability is triggered when many consecutive Signature RRs Dynamic Updates are sent exploiting an Out-Of-Bounds write on the heap when combining the many consecutive Signature RR Dynamic Updates into base64-encoded strings before writing to the Zone file as shown in the packet snapshot shown below.
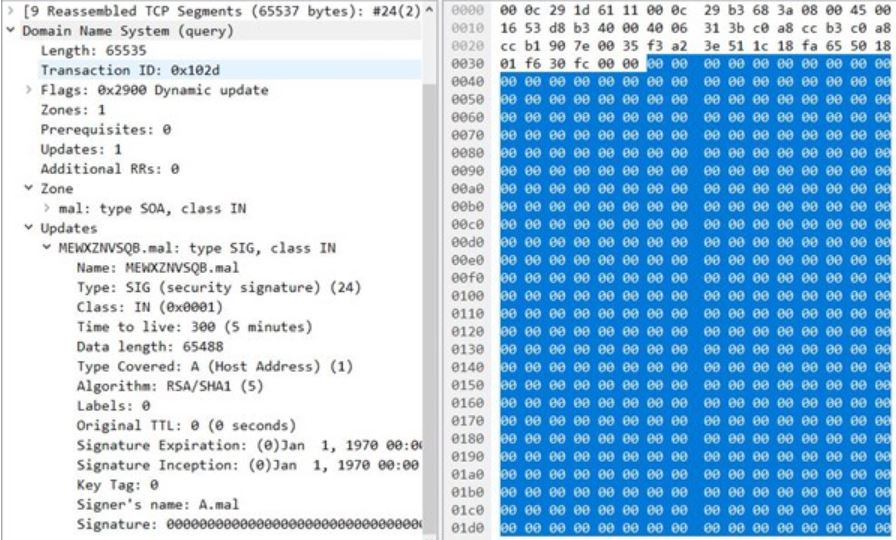
Image Source: McAfee
As per the advisory, this vulnerability impacts all DNS servers. The surrounding configuration may limit possible vectors/sources for the attack, but proper mitigation requires this month’s security update patch. Further, this vulnerability is only exploitable if the server is configured to be a DNS server.
Affected Products
The following versions of Windows hosting the Microsoft DNS server are affected:
- Windows server 2008, 2008 R2
- Windows server 2012, 2012 R2
- Windows server 2016
- Windows server 2019
- Windows server, version 1909, 2004, 20H2
Mitigation
To be vulnerable, a DNS server would need to have dynamic updates enabled. Microsoft has recommended to patch with the latest updates. Secondly, an organization must audit their DNS deployment configuration to limit Dynamic Zone Updates to trusted servers only.
CERT-FR recommends applying the patches as soon as possible and following the publisher’s recommendations to limit the window of exposure of vulnerable products.
In addition, CERT-FR strongly recommends:
- Not to expose Microsoft DNS service running on domain control or on a domain member server on the Internet.
- Not to allow dynamic DNS zone updates (secure or not) in the event of exposure of a Microsoft DNS service on the Internet.
- Not to allow insecure updates when using a Microsoft DNS service as part of an Active Directory infrastructure.
As a reminder, it is possible to control the configuration of a DNS zone with the command:
Dnscmd server_name / ZoneInfo zone_DNS_a_verifier AllowUpdate
The result is one of the following 3:
- 0: the zone is static.
- 1: DNS zone can be updated in an insecure way (not recommended)
- 2: the DNS zone can be updated in a secure manner (at risk for vulnerable equipment)
This information can also be verified by looking at the DSPROPERTY_ZONE_ALLOW_UPDATE value present in the dnsProperty attributes of each configured DNS zone.
Qualys Detection
Qualys customers can scan their network with QID 91754 to detect vulnerable assets .
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26897