A zero-day security flaw in Apple’s macOS Finder system has been detected. This vulnerability allows remote attackers to fool users into running arbitrary commands.
Zero-day vulnerabilities are defects that have been publicly published but have not yet been patched by the vendor. These vulnerabilities are sometimes actively exploited by attackers or have publicly available proof-of-concept exploits.
The macOS Finder is the default file manager and GUI front-end on all Macintosh operating systems. It’s the first thing users see when they boot up, and it controls the launch of subsequent applications. This is also responsible for the user file, disc, and network volume management.
Description
The flaw lies in the way .Inetloc files are handled by the macOS Finder. The .Inetloc files are used to store information on the internet. These are Apple-specific files and can be used to view documents locally on someone’s Mac within a browser using the “file:/” format (instead of http://) as shortcuts to internet locations like an RSS feed or a telnet location.
The vulnerability allows .Inetloc files to run arbitrary commands. These files can be inserted inside emails, and when the user clicks on them, the commands embedded inside them are executed without a prompt or warning.
At Qualys Labs, we’ve tried to recreate the issue and tested it on the latest OS such as High Sierra and Big Sur successfully.
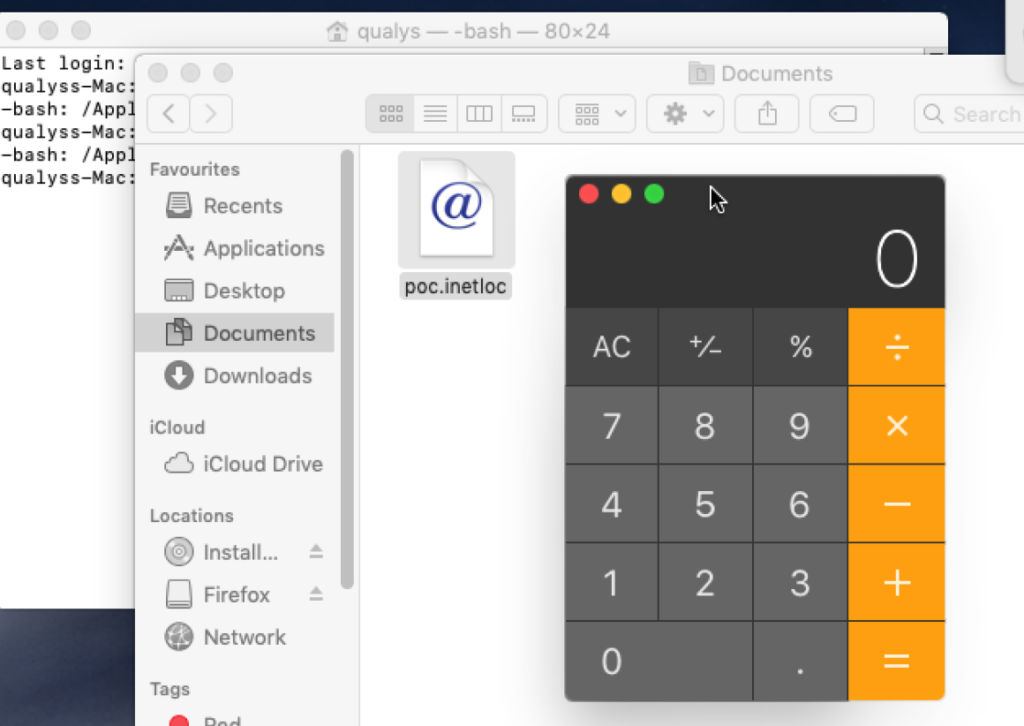
Image Source: Qualys
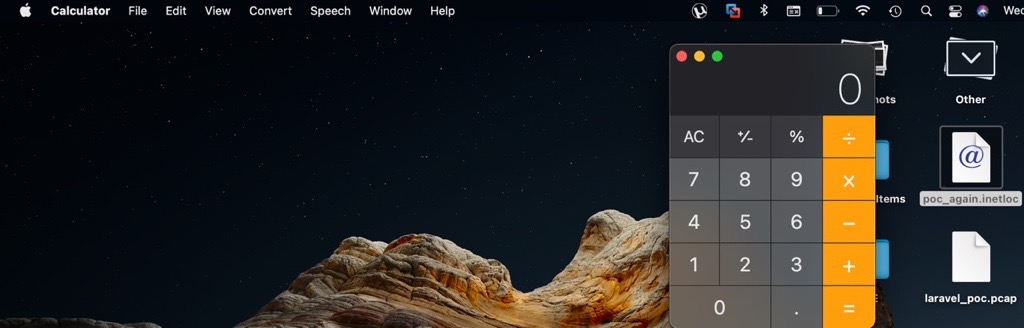
Image Source: Qualys
Source: Qualys
Affected versions
This vulnerability affects all macOS versions including the latest release, Big Sur.
Mitigation
Apple has informed that the vulnerability in file:/ has been discreetly patched in Big Sur and they have not assigned a CVE to it.
The file:/ prefix has been blocked (in the com.apple.generic-internet-location) in newer versions of macOS like Big Sur, however, they did a case matching, allowing File:/ or fIle:/ to bypass the check.
For more information, please visit the SSD Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 375909 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://ssd-disclosure.com/ssd-advisory-macos-finder-rce/
https://threatpost.com/unpatched-apple-zero-day-code-execution/174915/
https://cybersguards.com/a-new-vulnerability-found-in-apples-macos-finder-lets-attackers-run-commands-remotely/
https://www.bleepingcomputer.com/news/apple/new-macos-zero-day-bug-lets-attackers-run-commands-remotely/