The Apache Software Foundation has published additional security updates for its HTTP Server to remediate an incomplete fix for a path traversal and Remote Code Execution (RCE) vulnerability patched in the first week of October 2021 (CVE-2021-41773).
CVE-2021-42013 is based upon a path normalization bug, which allowed an unauthenticated remote user to view files on the Apache Web Server. Apache had released a patch (Apache 2.4.50) addressing the vulnerability. However, researchers found out that the patch was incomplete and can be used to execute arbitrary code remotely on the webserver server if the ‘mod_cgi’ module was loaded and the ‘require all denied’ configuration was absent. The target is vulnerable only if ‘require all denied’ is missing in the httpd.conf file.
Description
Apache has addressed the vulnerability stating, ‘It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. If files outside of these directories are not protected by the usual default configuration ‘require all denied’, these requests can succeed. If CGI scripts are also enabled for these aliased paths, this could allow for remote code execution.’
At Qualys Labs, we have tried to recreate the issue and tested it on Windows and Linux Operating Systems.
Windows
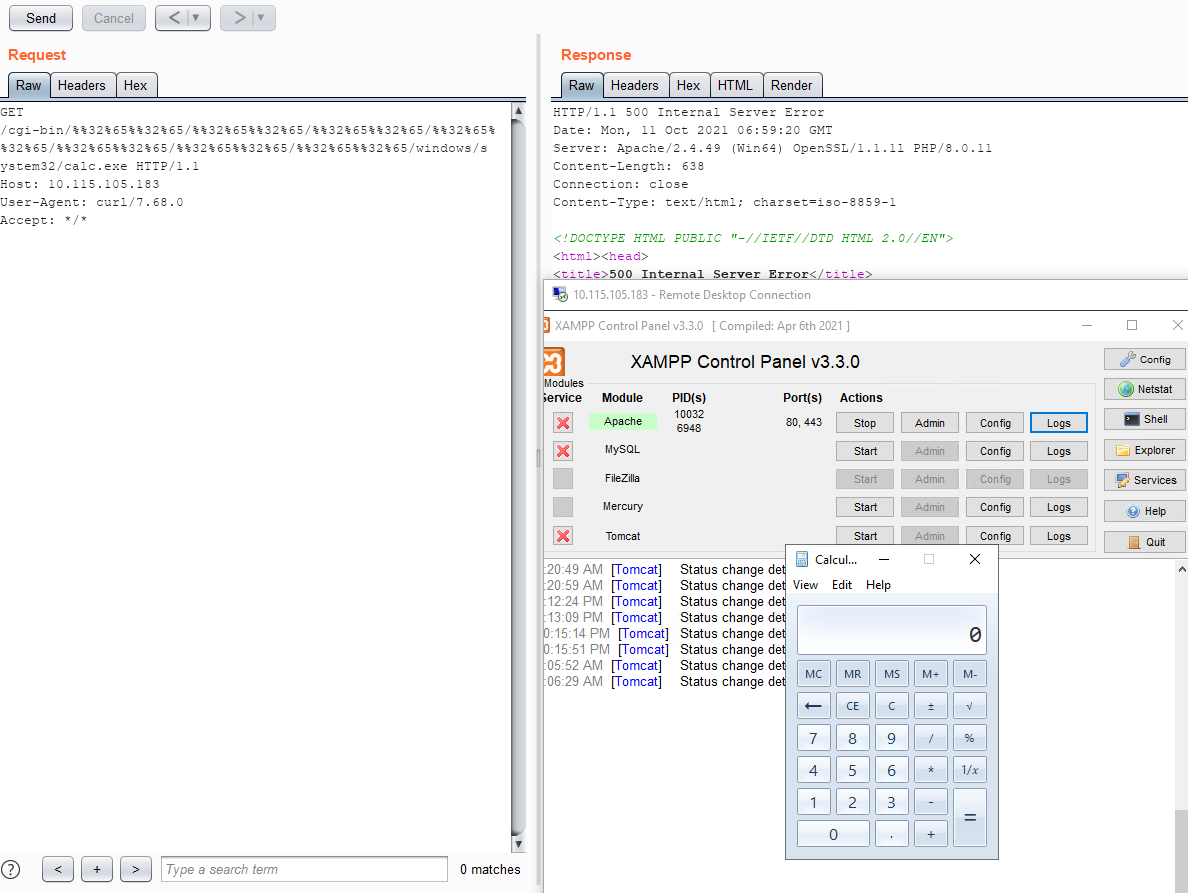
Image Source: Qualys
Linux
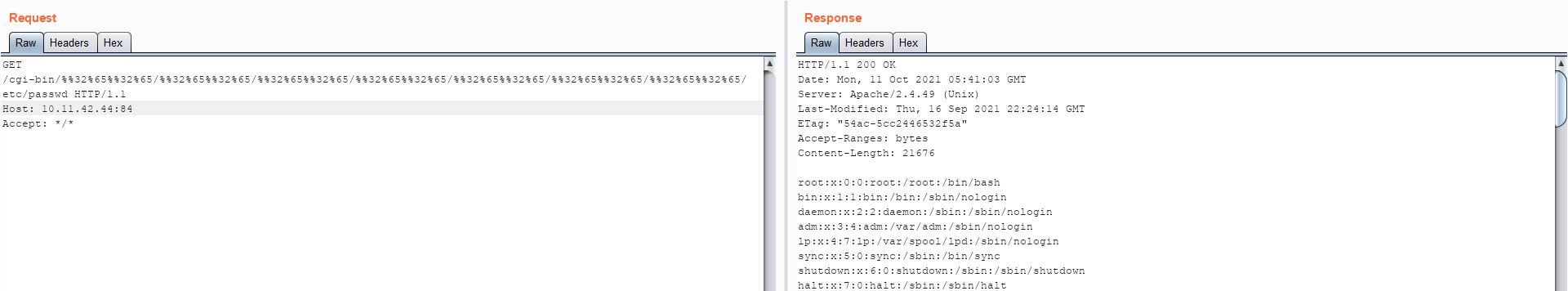
Image Source: Qualys
Affected versions
Apache HTTP Server 2.4.49 and 2.4.50 are the two versions affected by the vulnerability. All modern operating systems, including UNIX and Windows, are cross-platform compatible with this open-source web server version.
Mitigation
Customers are advised to update to Apache HTTP Server 2.4.51. For more information, please refer to the Apache HTTP Server download page.
Qualys Detection
Qualys customers can scan their devices with QID 87466 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://httpd.apache.org/security/vulnerabilities_24.html#CVE-2021-42013
https://thehackernews.com/2021/10/new-patch-released-for-actively.html
https://www.zdnet.com/article/additional-fixes-released-addressing-apache-http-server-issue/
https://www.bleepingcomputer.com/news/security/apache-emergency-update-fixes-incomplete-patch-for-exploited-bug/
https://us-cert.cisa.gov/ncas/current-activity/2021/10/07/apache-releases-http-server-version-2451-address-vulnerabilities